Poke around the net for information on secure coding in Python, Java, Android, or C++, for example, and you will find yourself neck-deep in search results comprising endless streams of back and forths on what can go wrong and how you can stop that from happening. (Indeed, search for professional, secure coding training alongside the language, and you will undoubtedly be directed to our SecureFlag Labs on these topics and more, which we encourage you to visit.)
Surprisingly, though, there are plenty of no less ubiquitous languages – with no fewer security issues – that receive far less attention than they warrant.
Well, here at SecureFlag, we are out to change that, starting with one of the workhorses of modern-day enterprises – ABAP.

What is ERP?
Enterprise Resource Planning (ERP) business management software typically comprises a suite of applications that an organization can use to collect, store and make use of all business activity data. As can be imagined, this means scale, with ERP systems often catering to everything from production capacity monitoring, logistics tracking, all back-office necessities like business-resource tracking, HR, Accounting, Manufacturing, as well as front-office systems and processes that require data flow to clients and other third-party organizations.
Ok, so what is SAP ABAP?
The software vendor SAP is a giant in the Enterprise Software space, with its solutions residing deep within innumerable organizations’ stacks worldwide. SAP’s Advanced Business Application Programming or ABAP is a high-level, general-purpose programming language to create business applications for the SAP environment.
ABAP supports two models that both offer interoperability: an object-oriented programming model based on classes and interfaces and a procedural programming model based on function modules and subroutines.
Companies can work with ABAP in SAP NetWeaver – the application stack for many of SAP’s applications - customize their SAP ERP system and the SAP S/4HANA business solution to meet their business needs.
ABAP offers many benefits for developers and companies looking to create or customize SAP business solutions. However, as with all other programming languages, correct configuration and implementation must be adhered to in line with best practices to ensure security snags are mitigated early on.
The Evolution of ABAP
First introduced in the 1980s, ABAP began as a general report-creation processor for SAP’s early versions, allowing for the mass processing of data in SAP business applications. Up until the mid-2000s, ABAP programs could only be created by following a set of pre-defined procedures to perform specific tasks.
Since then, however, ABAP has evolved into a multi-paradigm language that allows programmers to use object-oriented programming (OOP) and procedural programming principles. Its OOP functionality, for example, enables developers to create complex programs by utilizing ABAP design patterns and objects that can interact with each other.
Over time, SAP introduced many new features and capabilities into ABAP, including:
- Extended syntax for Open SQL, ABAP Managed Database Procedures (AMDP), and core data services (CDS) Views.
- SAP HANA in-memory database and development platform.
- A programming model for developing SAP HANA-optimized OData services for SAP Fiori applications.
- ABAP RESTful programming model (RAP) with clear separation among the database, business logic, and UI layers.
- ABAP Workbench development environment with a toolset, guidelines, plugins, and core data service.
ABAP now offers abstraction between the database, operating system, and business applications. Consequently, applications don’t depend directly on a specific database or server, and developers can focus on business functionality rather than the system’s technical intricacies. Abstraction also enables organizations to easily port applications or migrate between different SAP versions while maintaining business continuity.
ABAP – Characteristics of Integration and Incorporation
While ABAP is SAP’s primary programming language, its programs can run alongside programs created in other languages, including Java, JavaScript, and SAPUI5. And thanks to OOP and other associated principles, ABAP code is relatively short, clean, and clear, an advantageous quality for both programmers and end-users.
In 2011, the SAP HANA database was released, supporting an in-memory architecture built to support and store vast amounts of data in the server’s main memory. The combination of SAP HANA and ABAP means processing that used to occur on the application layer can now happen on the database layer, decreasing processing time for speedier transactions.
Further ABAP characteristics include:
- Internal tables that dynamically store and process mass table data in working memory.
- Integrated logical unit of work (LUW) that allows multiple users to access the central database simultaneously.
- Integrated interface to other programming environments.
- Integrated interface to XML.
- Support for multilingual programs.
You make a case for a powerful tool! But should I be worried about ABAP security?
As you may have guessed - this is a secure coding training blog after all - the short answer is a resounding yes!
For the longer answer that points to specifics, read on!
The Pitfalls of Customization and Coded Authentication
Many security defects are introduced into these applications during the coding phase – ABAP is far from unique here – with customizability affording both business wins and potential disasters if uncovered.
For instance, ABAP enables SAP customers to extend the existing functionality of stock SAP systems with their own programs. Such customizability and flexibility is indeed useful – and even essential – for many companies. However, customized ABAP programs may have security vulnerabilities that expand the SAP attack surface and leave the organization vulnerable to exploitation.
Furthermore, SAP has an integrated roles and authentication model that mandates explicit checks to access ABAP application resources. This requires securing the code in the application. Also, exposing remote RFC functions requires the proper management and maintenance of S_RFC authorization objects.
Touching on the previous point concerning the (non)uniqueness of the problem, proper SAP ABAP management controls - and the guidelines for their use - do exist. The problem, as with so many other programming languages out there, is that they are not strictly adhered to. Thus, vulnerabilities still creep into ABAP applications because developers either don’t know much about ABAP secure coding practices or ignore these practices to speed up development and time-to-market.
ABAP Developers Need Hands-on Training Too
Any developer – ABAP or other - must endeavor to produce robust code that has been built in line with up-to-date best practices. They must also know how to secure their code from the many other dangerous vulnerabilities, including:
- SQL injections
- Command injection
- Cross-site scripting
- Path traversal
- Configuration issues
- Hardcoded credentials
- Missing authorizations
- Denial of Service attacks
SAP has added “security notes” to ABAP documentation to educate developers about secure coding practices for ABAP. However, these notes are exactly that – summarized notes – and, as with so many other instruction manuals that define how our digital environment should be constructed, such notes often get lost or fall from memory rapidly.
Of greater practicality is SAP’s ATC (ABAP Test Case) tool, which can be used for code vulnerability analysis, although to stress the point, clean code from the beginning means less reliance on post-analysis tinkering.
ABAP developers need comprehensive training and hands-on practice to prepare for real-world security challenges, especially given the prominence of the language in many of the world’s organizations.
To this end, SecureFlag has built a highly adaptive, 100% hands-on ABAP training program, providing:
- Hands-On Labs
- Real-world security challenges
- Practice with real vulnerabilities
- Adaptive learning content and learning paths customised to match the skill and knowledge level of each learner
- Real-time feedback
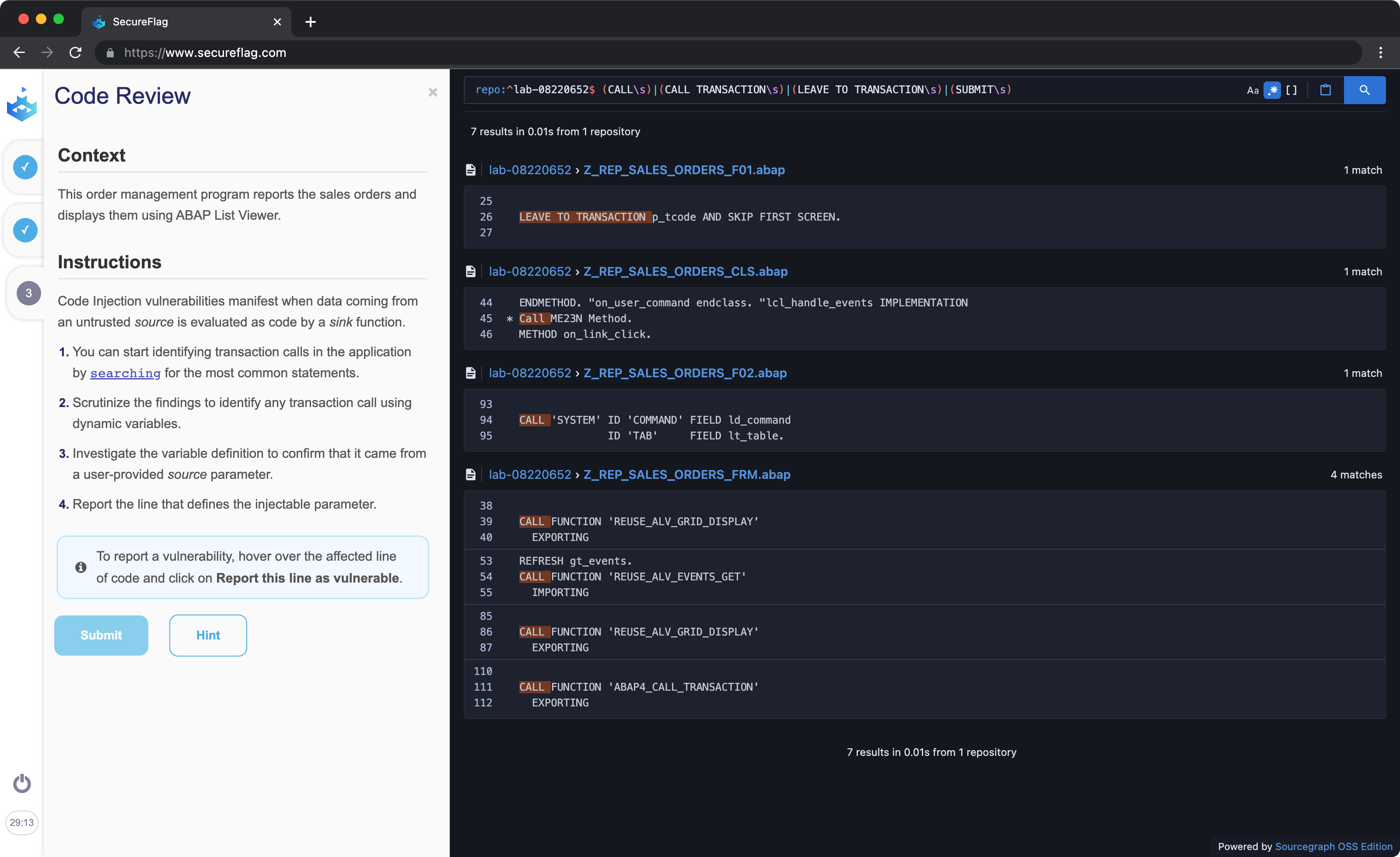
With SecureFlag, ABAP developers learn how to code securely and address real vulnerabilities all in a real working environment. In this way, those previously mentioned ‘summarized security notes’ make way for hands-on, practicable lessons learned and remembered for the real environment.
For more information on these or any of our other numerous current and upcoming Labs, don’t hesitate to get in touch.