As cyber threats become more sophisticated, the need for skilled Security Operations Center (SOC) Analysts is at an all-time high. SecureFlag recognizes this demand and offers comprehensive training solutions tailored for both aspiring and seasoned SOC professionals.

First things first, though - what exactly is a SOC, why is it a high-value asset to an organization’s security structure, and what do SOC Analysts actually do?
The Security Operations Center
A Security Operations Center is the nerve center of an organization’s cybersecurity efforts. It monitors, analyzes, and protects against cyber threats in real-time. The SOC team, comprising various cybersecurity experts, works tirelessly to identify potential security incidents, manage them effectively, and prevent future attacks.
The SOC Analyst
A SOC Analyst is a critical player within the SOC. Their primary role involves monitoring network security, analyzing alerts, and responding to incidents. Essential skills for a SOC Analyst include a deep understanding of network infrastructure, proficiency in various security tools, and the ability to analyze and interpret data. This role has various levels, ranging from entry-level analysts who handle initial incident detection to more senior positions focusing on complex threat analysis and strategy development.
The SIEM
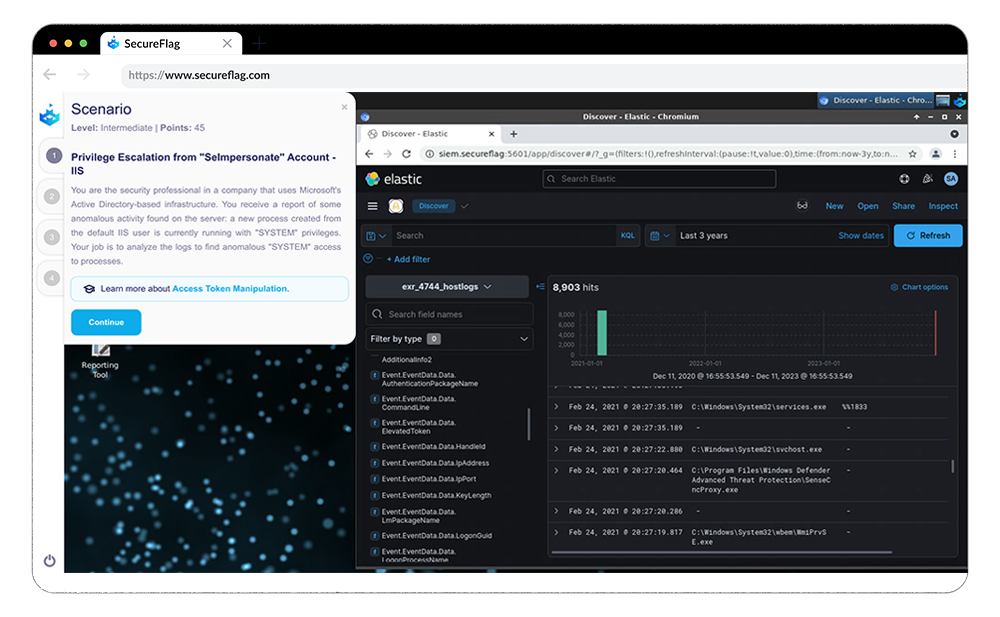
Security Information and Event Management (SIEM) systems are at the heart of SOC operations. They provide insights into an organization’s cybersecurity posture, aggregating data from various sources and using advanced analytics to detect suspicious activities. There are different types of SIEM systems, each with unique features, but all aim to provide real-time visibility into an organization’s security posture.
Whilst automation abounds, a human - a SOC Analyst - still remains a crucial component in making sense of the often overwhelming amount of information and identifying the threats amidst the noise.
Threat Analysis and Incident Response
Threat Analysis and Incident Response are two critical activities within a SOC. Threat Analysis involves examining and interpreting data to identify potential threats. Incident Response, on the other hand, is the action taken to mitigate and resolve security incidents. While Threat Analysis is proactive, Incident Response is reactive. For example, Threat Analysis might involve identifying a potential phishing campaign, whereas Incident Response would kick in once the phishing attack is underway.
SecureFlag’s Training Offering
SecureFlag offers specialized learning paths to enhance the skills of SOC Analysts:
- Detection of MITRE ATT&CK Most Used Techniques: this series of courses focuses on understanding and detecting the most common techniques used by adversaries, as outlined by the MITRE ATT&CK framework.
- Cyber Threat Intelligence: these courses provide insights into Cyber Threat Intelligence, teaching analysts how to gather, analyze, and apply intelligence effectively.
- Adversary Emulation: in these courses, real-world cyber attacks are simulated, helping analysts understand the tactics, techniques, and procedures used by attackers.
Secure Your Future with SecureFlag
The role of a SOC Analyst is more crucial than ever in our digital world. SecureFlag’s SOC Analyst Labs training offers an unparalleled opportunity to develop the skills needed to excel in this field. Whether you’re starting your cybersecurity journey or looking to advance your expertise, SecureFlag equips you with the knowledge and practical experience to stay ahead in the cybersecurity arena. Embrace the challenge and secure your future with SecureFlag!


