Back in March, we examined some best practices for improving the security of your MySQL database. While there is overlap and similarity between the two services, there is still enough difference to warrant highlighting some best practices for PostgreSQL security hardening.

Why is Database Hardening Important?
PostgreSQL is a powerful and feature-rich open-source database management system. It has become a go-to choice for many organizations due to its reliability, scalability, and robust security features. Due to how popular it is, there is a large pool of user support available as well. However, like any software, PostgreSQL is not immune to security vulnerabilities. Cybercriminals constantly seek to exploit weaknesses in database systems, and a compromised database can lead to devastating consequences, such as data breaches, financial losses, and reputational damage.
By implementing a database hardening strategy, we can significantly reduce the risk of such attacks and ensure the confidentiality, integrity, and availability of our critical data. Hardening your PostgreSQL database enhances overall security and demonstrates your commitment to data protection, whose importance is only becoming more relevant for compliance with industry regulations and standards.
Common security vulnerabilities in PostgreSQL databases
Any application with a database connected is open to some common weaknesses. SQL injection attacks are common in the wild, but this post will look more at the configuration side of things rather than directly at the front-end interactions. With that being said, some common weaknesses in PostgreSQL databases look like:
- Weak Authentication: Weak user authentication mechanisms or access control policies can be taken advantage of to allow unauthorized access to personal and customer data.
- Insufficient Access Control: Weak Access Control risks unauthorized data access and manipulation, posing significant risks to data confidentiality, integrity, and availability. This issue arises when users or roles are granted excessive permissions, or when security configurations are lax, allowing malicious actors to exploit vulnerabilities.
- Insecure Data Transmission: Transmitting data in plaintext or using insecure transfer methods can expose your system and applications to man-in-the-middle (MitM) attacks or data interception.
- Unencrypted Data: When data is stored in a database, storing it without encryption or in plaintext can make appealing targets for attackers looking to get access to a cache of plaintext passwords or other credentials and information.
- Lack of Monitoring: Logging and monitoring aren’t a proactive method for preventing vulnerabilities, so they might rank lower on lists of important tasks to implement. However, they are essential for effective and early detection of any breaches so that your systems can be secured in good time.
How can the security of a PostgreSQL Database be improved?
When improving PostgreSQL security, there are some procedures and processes that can be applied that are common in the industry.
Network Security
- Enforce SSL/TLS Encryption: Configure your PostgreSQL server to require SSL/TLS encryption for all client-server communications, ensuring the security of data transmitted between the application and the database.
ssl = on
ssl_cert_file = '/path/to/server.crt'
ssl_key_file = '/path/to/server.key'
ssl_ca_file = '/path/to/root.crt'
- Restrict Network Access: Limit the network interfaces and IP addresses that can connect to your PostgreSQL server, and use firewall rules to control inbound and outbound traffic.
- Implement IP Allowlisting: Configure your PostgreSQL server to only allow connections from a predefined list of trusted IP addresses, effectively blocking unauthorized access attempts.
Encryption
- Enable Transparent Data Encryption (TDE): Utilize PostgreSQL’s built-in Transparent Data Encryption feature to automatically encrypt data at rest, ensuring that even if an attacker gains access to the physical storage, the data remains unreadable.
-
Implement Column-Level Encryption: For sensitive data fields, consider implementing column-level encryption using PostgreSQL’s encryption functions, such as
pgcrypto.
CREATE EXTENSION pgcrypto
-- Create a table with a column to store encrypted data
CREATE TABLE users (
id serial PRIMARY KEY,
username text NOT NULL,
password bytea NOT NULL
);
-- Insert data into the table, encrypting the password
INSERT INTO users (username, password)
VALUES ('alice', pgp_sym_encrypt('mysecretpassword', 'mysecretkey'));
- Manage Encryption Keys Securely: Ensure that the encryption keys used for data protection are stored and managed in a secure manner, such as in a dedicated key management system or hardware security module (HSM).
Authentication and Authorization
- Enforce Complex Passwords: Require users to create strong, complex passwords that meet your organization’s password complexity requirements. This can include minimum length, character mix, and password expiration policies.
- Implement Multi-Factor Authentication: Enable multi-factor authentication (MFA) for all user accounts, including administrative users, to add an extra layer of security beyond just a password.
- Utilize Role-Based Access Control: Implement a well-structured role-based access control (RBAC) system to ensure users can only perform actions and access data relevant to their job responsibilities.
Update and patch PostgreSQL
- Monitor for PostgreSQL Security Advisories: Be aware of the latest security vulnerabilities and patches released by regularly checking for PostgreSQL security advisories.
- Keep your server up-to-date: Stay informed of the latest releases in PostgreSQL and whether your server needs to be upgraded. When looking at this it’s important to consider whether your data can be safely migrated, or if any extra steps need to be taken prior to upgrading.
- Test Patches in a Controlled Environment: When possible, apply patches and upgrades in a test or staging environment before applying them to production. Thoroughly test them in a non-production setting to ensure compatibility and prevent any unintended consequences with data migration.
Logging
- Enable Logging: Configure your PostgreSQL server to log all relevant security-related events, such as failed login attempts, privilege escalations, and database modifications.
# Enable logging
logging_collector = on
# Log IP of successful logins
log_connections = on
# Log hostname of authentication attempts
log_hostname = on
As well as logging authentication attempts, you can enable logging for statements that have been run using the property below:
log_statement = 'all' # options: none, ddl, mod, all
- Implement Centralized Log Management: Integrate your PostgreSQL logs with a centralized logging solution, such as a Security Information and Event Management (SIEM) system, to facilitate log analysis and security incident detection.
Backup and Disaster Recovery
Not only should you prepare to defend against attacks or vulnerabilities, but your organization must also have a plan in place if something goes wrong. Backups and recovery plans are the best approach.
- Implement Backup Strategies: Establish a comprehensive backup strategy that includes regular full backups, incremental backups, and off-site storage of backup data to ensure the recoverability of your PostgreSQL database in the event of a disaster, cyber attack, ransomware attack, or other forms of data loss.
- Test Backup and Restore Procedures: Regularly test your backup and restore procedures to ensure that you can successfully recover your PostgreSQL database in the event of an emergency.
SecureFlag and PostgreSQL training
With SecureFlag, we take an approach to immerse users in reviewing code and configuration settings for interactions with their databases. The SecureFlag platform features labs that allow looking at PostgreSQL config files and spotting where the misconfigurations or vulnerable settings are, allowing for knowledge to be taken away and immediately applied to real-life environments.
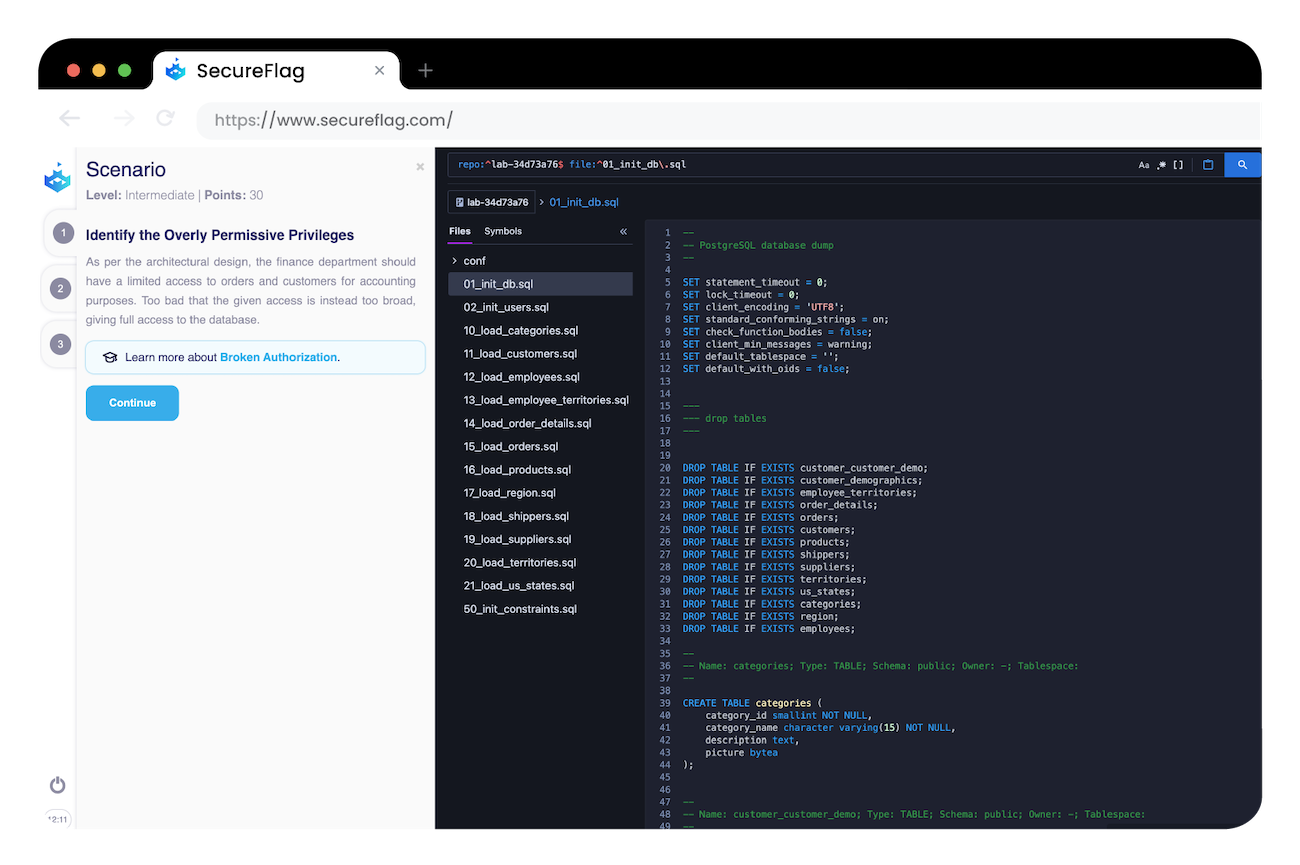
SecureFlag offers much more than PostgreSQL labs too. It offers many examples of securing databases and writing secure mobile applications with Kotlin, React Native, and web frameworks such as Django, Flask, Ruby Sinatra, and many more. Browse our catalog for a full insight into our continuously growing list of labs!
If you’re looking to take your application security to the next level, contact our team to learn more about how SecureFlag can help boost your organization’s security knowledge.