- The modern approach—a cycle of reintroducing vulnerable code
- Current security does not go far enough to avoid reintroducing vulnerable code
- Are automated security tools enough to prevent the reintroduction of code vulnerabilities?
- The solution to avoid reintroducing vulnerable code? Train your developers in Secure Coding techniques
- 6 ways Secure Coding Training benefits developers
- Choosing a Secure Coding Training Platform
Code vulnerabilities compromise your security and can stem from insecure coding practices. Learn how to break the cycle and avoid reintroducing vulnerable code and insecurities in your software.
Planning out your roadmap to keep up with the demand of customers and keeping ahead of the competition means getting new features out the door. This means that processes need to be streamlined and efficient throughout the development lifecycle.
Unfortunately, we still see breaches and failures occurring all the time. With recent crises bringing international travel to a standstill and wreaking havoc on health services, we need to ask questions such as: Are automated scanning tools enough to combat the issues that arise not just from threat actors but also from our own rush to get new software released?

The modern approach—a cycle of reintroducing vulnerable code
Security practices in the industry are always changing, but a common theme in the modern approach to software development is to deploy automated tools such as static code analysis, dynamic analysis, and software composition analysis to root out security flaws and poor design patterns. They can detect a wide range of security flaws, from simple input validation errors to complex issues like race conditions and memory leaks. However, despite their effectiveness in finding vulnerabilities and recommending changes and different approaches, these tools often reveal a frustrating pattern: the same types of vulnerabilities are being reintroduced by developers after they’ve already been fixed before.
This cycle of finding, patching, and reintroducing vulnerabilities not only undermines the efforts of security teams but also represents valuable time and effort being wasted. Each time a vulnerability is reintroduced, it must be identified, prioritized, and fixed again, leading to repetitive and redundant work and significantly increasing the overall cost of software development and maintenance.
Current security does not go far enough to avoid reintroducing vulnerable code
We’ve talked about this before in our post—Shift Left with Effective Security Training—where shifting security left does not go far enough and that teams should be encouraging secure code training for developers. In fact, The Linux Foundation’s “Secure Software Development Education 2024 Survey” found that 28% of professionals involved with software development are not familiar with secure software development, meaning that many developers are operating with an “as needed” approach to security when programming rather than from the offset.
Many professionals (28%) involved with software development are not familiar with secure software development.
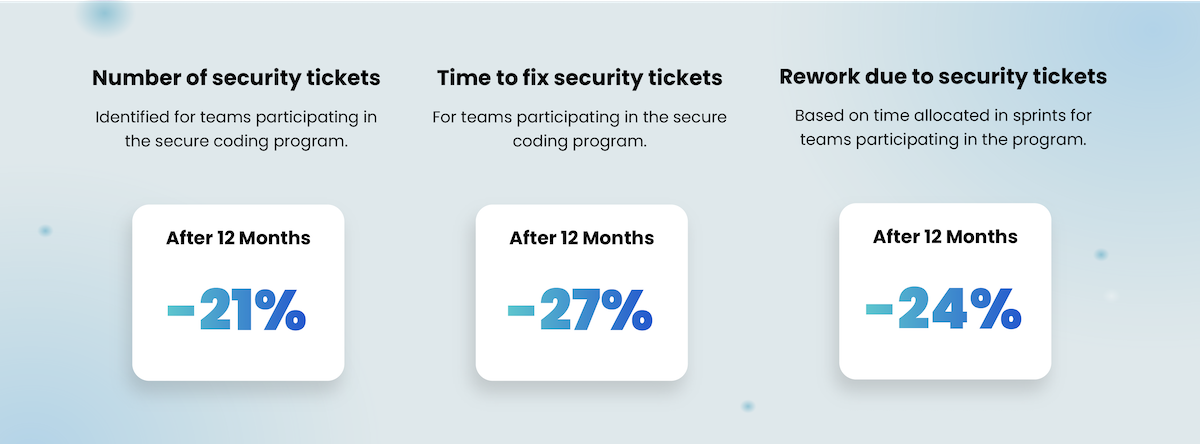
Our own findings report that implementing a secure coding training program can reduce the number of new security tickets by 21%, and the time spent conducting security rework is reduced by 24%.
Are automated security tools enough to prevent the reintroduction of code vulnerabilities?
You would assume that automated tools would be enough to prevent the reintroduction of code vulnerabilities.
It seems an obvious statement to say that most companies hire developers with a background in Computer Science, Engineering, and Mathematics. This makes sense given the nature of the role, but what this kind of background is usually missing is a working knowledge of what makes software secure, secure design principles, or how to write more secure code.

Referring back to The Linux Foundation’s report, developers with less than one year of experience report a lack of familiarity with secure software development, with 75% being unfamiliar with secure concepts. Lowering only to 72% for those with one to two years of experience, highlighting the lack of training and exposure even after entering the workforce.
Software developers with less than one year of experience report the highest lack of familiarity [with secure software development] at 75%, with this number dropping to 72% for those with one to two years of experience.
With the numbers reporting that developers aren’t getting the training required to help tackle vulnerabilities, it’s understandable that there is a reliance on automated tools to do some heavy lifting. This solution represents its own problem: not upskilling developers in favor of a quick-fix solution that encourages redundant rework.
The solution to avoid reintroducing vulnerable code? Train your developers in Secure Coding techniques
To break the cycle of reintroducing the same kind of insecurities and vulnerabilities in your software, train your teams on how to address issues at the root source. This doesn’t just mean committing to an annual training once a year but rather introducing your teams to the idea of regular training through a dedicated platform to teach them core concepts across all of the languages that are used in your tech stacks.
Ideally, this new training should encompass modern vulnerabilities and be vendor-neutral about how it refers to them, providing unbiased information and objective facts about how to remediate issues.
Some topics that should be common attacks are Cross-Site Scripting (XSS), Code Injection, SQL Injection, and more. Developers should be aware of what these attacks are called and how they are carried out to better inform them on how to defend against them.
6 ways Secure Coding Training benefits developers
Secure coding training helps developers in more ways than one, enhancing skills, efficiency, and contribution to an organization’s overall security posture.
1. Formalizes training
Current trends in software development see developers seek out their own methods of remediation and solutions, usually through online research for a fix. This offers several problems:
- Developers will potentially rely on inaccurate or out-of-date information from older sources.
- Inconsistent approaches from different team members.
- Lack of understanding of what a fix is actually addressing—meaning repeated occurrences of the vulnerabilities are likely.
Through formalizing developer training with a dedicated platform, developers gain access to a structured approach, problem-specific solutions researched and addressed by industry security experts, and certifications to validate their efforts and encourage continuous learning.
2. Reduces vulnerabilities
Enrolling developers in a secure coding training program increases developer knowledge of secure design methods and patterns, allowing them to create more secure code from the beginning and, in turn, increasing the overall security of applications.
3. Less time spent on vulnerability management
Less time working on another vulnerability patch and remediation means more time spent on developing features and progressing the product roadmap.
4. Meeting compliance
Multiple legislations and industry standards, such as PCI DSS and HIPAA, require regular security training to be implemented for employees interacting with user data or systems that secure it.
Implementing a relevant secure coding training program ensures your organization is compliant whilst also giving developers meaningful and directly transferable skills to immediately put to use.
5. Security Champions
Regular training with developers and teams increases security knowledge across your organization, giving rise to more Security Champions who can help others address vulnerabilities and teach new methods to their teams.
6. Reduce testing tool reliance
By increasing the level of knowledge and experience in developers across the Software Development Life Cycle, you, in turn, reduce the reliance on automated scanning tools to do the heavy lifting.
Choosing a Secure Coding Training Platform
SecureFlag’s Platform sets out to ensure developers get access to hands-on labs that represent a real-life environment. In SecureFlag labs, developers complete hacks to get an understanding of the risks and dangers of different vulnerabilities. After completing a hack, the lab sets out the task of remediating the vulnerability, providing the same tools, IDEs, and terminals that are used in everyday work.
Culture of security
With SecureFlag, we encourage participation from all. From developers to managers and CISOs, wide participation across the organization helps create and promote a culture of security where training is encouraged and recognized. Using gamification techniques, SecureFlag engages teams to compete with one another and gain experience at the same time.
We’d love to talk more about how Secure Coding Training can benefit your organization. Get in touch today to arrange a chat and find out more!