- What is CI/CD?
- GitLab as a provider of CI/CD
- The importance of security in CI/CD
-
Best practices for CI/CD security
- 1. Stop malicious code insertion with better reviews
- 2. Patch and update your CI/CD tooling regularly
- 3. Secure secret management
- 4. Implement access control measures to your CI/CD
- 5. Choose third-party dependencies carefully
- 6. Monitoring and logging
- 7. Backup and recovery
- 8. Training and awareness
- How can SecureFlag help
You’re probably familiar with CI/CD tools like GitLab, GitHub Actions, and Travis CI. But are you aware of the security challenges that come with them? This guide dives into key security practices to safeguard your CI/CD pipelines.

What is CI/CD?
CI/CD stands for Continuous Integration and Continuous Deployment, which automates code integration and software deployment. Tools like GitLab streamline this process, but security risks can still slip through if you’re not careful.
It’s pretty standard for these types of systems to be integrated with development teams’ version control systems, such as Git, which allows each developer to contribute individually.
GitLab as a provider of CI/CD
GitLab is a powerful DevOps platform that integrates CI/CD processes to enhance the overall software development life cycle. It combines source code management and project management into a single application, allowing teams to collaborate more efficiently, automate testing and deployment, and deliver software faster.
With features like version control, issue tracking, and merge requests, GitLab provides the tools for managing code, tracking project progress, and ensuring seamless integration.
GitLab has many features for finding security vulnerabilities in code repositories, with various automated scanning tools in the pipeline.

Implementing this sort of functionality into your pipelines, along with targeted training like SecureFlag to address vulnerabilities when they are discovered, helps train developers with knowledge and skills at the perfect time.
Read more about this integration on our blog or on GitLab.
The importance of security in CI/CD
It’s common now for large platforms like GitLab to feature a whole host of security features and tools that allow scanning your project’s code for vulnerabilities, scanning containers in production, and performing dependency analysis. But in this post, we’re taking a look at some of the more fundamental security steps your team can take.
Why CI/CD security is important
Confidentiality: CI/CD pipelines often handle sensitive data, including proprietary code, user information, and, in some unfortunate cases, credentials. Ensuring this data remains confidential is critical to maintaining trust and compliance with relevant industry standards and regulations.
Integrity: As code passes through the pipeline, there are countless opportunities to have malicious code inserted. Robust security and configuration reviews are needed to ensure the integrity of the software.
Availability: CI/CD systems play such an important role now that any downtime will disrupt the entire software development life cycle (SDLC pipeline). Potentially stopping developers from releasing new software updates and products.
Compliance and Regulatory Requirements: Many industries have stringent security and compliance requirements. Ensuring CI/CD pipelines are secure helps meet these regulations and avoid legal and financial penalties.
Reputation Management: Security breaches can severely damage a company’s reputation. Implementing strong security practices in CI/CD pipelines helps prevent incidents that could lead to loss of customer trust and business.
According to GitLab, 57% of respondents admit that their CI/CD pipelines were not adequately secured.
Best practices for CI/CD security
CI/CD systems are complex, and it can be difficult to know where to start. There are some commonly accepted best practices to implement to establish a secure baseline for your systems:
1. Stop malicious code insertion with better reviews
Malicious code insertion is a serious risk, especially when code reviews are lax. Here’s how to tighten things up:
Smarter Code Reviews
-
Peer reviews: Don’t let code go live without at least two sets of eyes on it. Having a peer check your work can catch issues you might miss.
-
Checklists Are Your Friend: Use a simple checklist during reviews to look for common security problems, such as SQL injection or unchecked inputs.
Automate for Safety
- Perform scans: Many commercial and open-source tools are available to scan your code automatically for vulnerabilities right in your CI/CD pipeline. One such tool might be a Static Analysis tool or a Software Compositional Analysis tool.
Lock Down Your MRs
-
Protect Your Branches: Only let trusted team members approve Merge Requests (MRs) for critical parts of your codebase.
-
Automated Checks: Set up your CI/CD to run security scans on MRs automatically so nothing risky slips through.
2. Patch and update your CI/CD tooling regularly
Because of how CI/CD pipelines work, they’ll often use high-risk (read/write) credentials. Check for updates if your system is private and local, and opt-in for the latest security updates if it is hosted by a cloud provider.
Also, be sure to check for updates for any dependencies included or installed throughout your pipeline, and be aware of any recent security vulnerabilities that have been published.
3. Secure secret management
Due to the nature of secrets and all that they can encompass, such as credentials, certificates, and API keys, they need to be highly available—to both users and also for use within applications. Secrets should only be accessible on a need-to-know basis with the “least privilege” principle applied.
Secrets management should be fully automated using cloud-based secret management services. If these services are not used, secrets should be dynamically injected into the pipeline through environment variables, with strict controls to prevent unauthorized access.
4. Implement access control measures to your CI/CD
Role-Based Access Control (RBAC) is widely adopted as a best practice that assigns permissions based on users’ roles and needs within the organization to limit access. For example, a developer may have access to commit and push code changes, while only security engineers can approve and deploy those changes to production.
When implementing this system, you should enforce the principle of least privilege so that users are allocated only the minimum necessary permissions to perform their tasks. This helps ensure the risk of accidental or malicious actions from insider threats is reduced.
5. Choose third-party dependencies carefully
Modern applications heavily rely on third-party libraries and frameworks.
But these dependencies can introduce vulnerabilities if not properly vetted. Here’s how to manage them securely:
Review dependencies thoroughly
-
Security Issues: Before integrating any third-party dependency, review it for known security vulnerabilities. Use tools like OWASP Dependency Check or another commercial alternative to identify potential risks.
-
Outdated Versions: Always check if the dependency is up-to-date. Outdated libraries can expose your application to known vulnerabilities that have already been patched in newer versions. Using older versions might expose you to a vulnerable supply chain.
-
Transitive Dependencies: Don’t just scan your direct dependencies—check their dependencies too. Transitive dependencies can also introduce vulnerabilities into your pipeline.
-
Reputation and Maintenance: Prioritize dependencies from reputable sources that are actively maintained. Regular updates and a strong community indicate a lower risk of unpatched vulnerabilities.
Exercise caution using community-published tools
-
Unreviewed Actions: Using third-party and community-published scripts and tools carries its own risk as these are often not reviewed by the hosting platform. This means they could be compromised by malicious actors.
-
Prioritize Trusted Sources: When possible, use actions or libraries that are widely recognized and come from reputable maintainers. Avoid newly published or little-used actions without a strong reputation.
Implement a Review Process
- Security Review: Establish a review process for any new dependencies added to your pipeline. This should include a thorough security assessment and consideration of alternative, more secure options. Implement an approval workflow where your security team must vet new dependencies before they are used in production.
6. Monitoring and logging
Part of a secure CI/CD pipeline is having the correct tools in place to effectively assess its performance if or when something goes wrong, allowing teams to detect and respond to potential security incidents with speed.
Enable comprehensive logging for all activities within the CI/CD environment, including code commits, build processes, deployment actions, and access requests. This data provides invaluable insights for identifying abnormal behavior or unauthorized access attempts.
7. Backup and recovery
Sometimes, things don’t go as we plan, and ironically, you should have plans in place for this, too. Backups and recovery plans are crucial for maintaining the integrity and availability of your CI/CD pipeline in the event of data loss, corruption, or an attack.
Schedule regular backups of critical data, including configuration files, source code repositories, and pipeline scripts, to ensure that you can quickly restore operations if something goes wrong. It’s also important to test your backup processes to verify that they function correctly; after all, there’s no point in having processes in place if they don’t work.
Ideally, backups should be stored in a location separate from your primary systems to guard against data breaches or disasters. Additionally, establish a clear and well-documented recovery plan to help your team respond to incidents and minimize downtime.
8. Training and awareness
Continuous and regular training should cover secure coding practices, the importance of maintaining updated dependencies, and the recognition of common attack vectors within environments and software as a whole.
Educating developers, operations staff, and other stakeholders about the security implications of their actions and decisions within the CI/CD environment helps create a security-conscious culture.
Additionally, fostering awareness about new threats and evolving security practices ensures that your team remains vigilant and informed.
How can SecureFlag help
How does SecureFlag fit in? Our platform is unique in that it offers training suitable for everyone involved with the SDLC.
We don’t just cater to developers. QA engineers, DevOps engineers, Solution Architects, and anyone else involved with the SDLC should be trained in the latest threats. Every organization is different, and so is everyone’s skill set, so we need to address any gaps that might arise within our software teams.
Train in virtual sandboxes
SecureFlag training labs allow users to perform attacks on sandboxed applications to get an understanding of how genuine vulnerabilities materialize in real life.
After performing an attack, participants set about remediating the vulnerability and get the opportunity to perform the hack again or continue the lab.
Our labs are created by our team of security experts with regular releases of new and current vulnerabilities.
Assess potential threats with ThreatCanvas
Don’t leave your applications open to attacks, just because you think that you’ve covered all attack surfaces and threats, doesn’t mean you have.
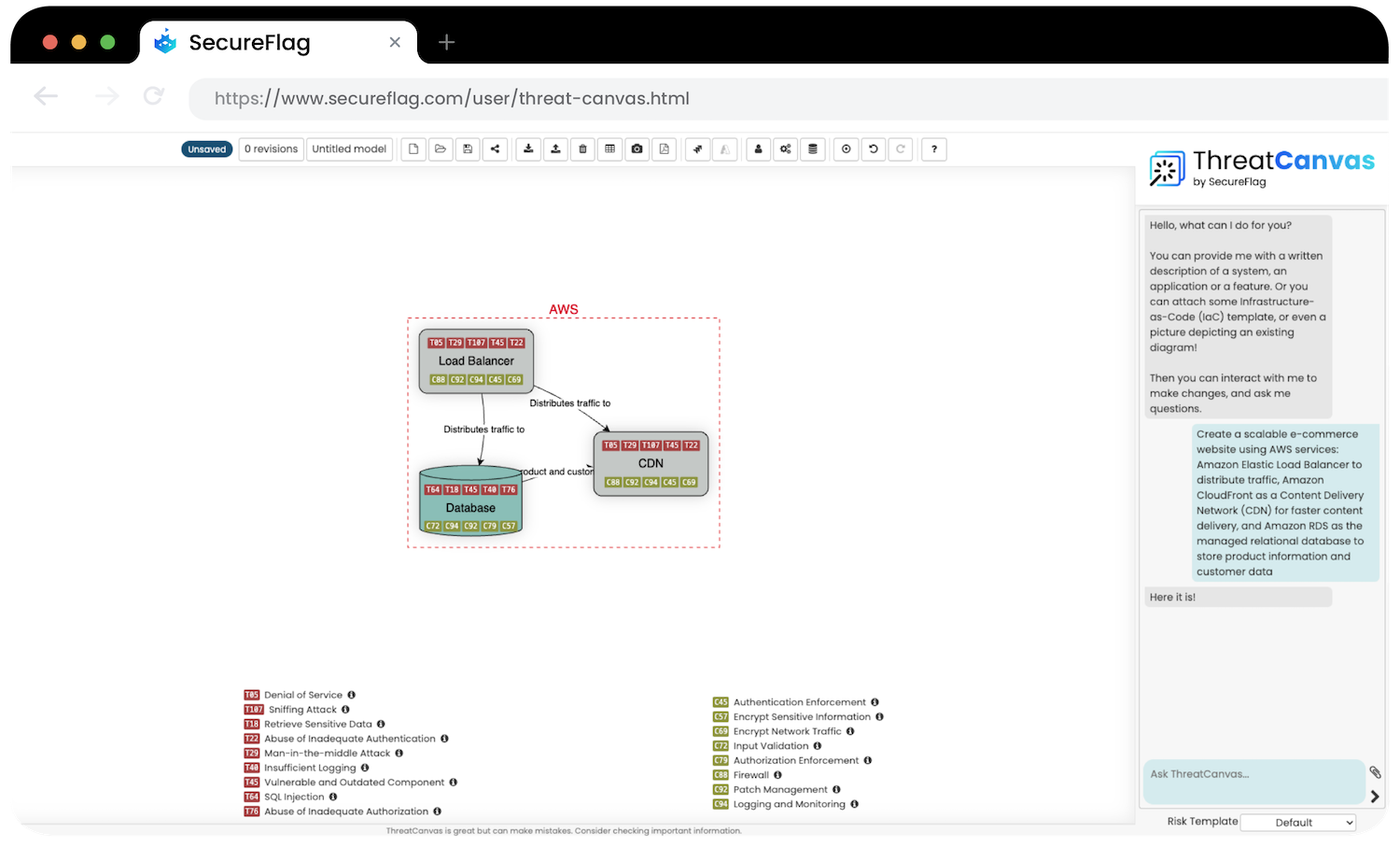
The security design review and threat analysis stages should cover the range of threats your system is open to and how to mitigate them. Threat modeling is an effective method for this.
With ThreatCanvas, threat modeling is an automated, scalable, and shareable process that can be undertaken by anyone and everyone involved in the SDLC.


