Considering developers already commit and push code every day, why not make security compliance part of that process? SecureFlag Git hooks allow teams to enforce training requirements automatically, embedding security compliance directly into Git workflows.
The hooks make it easy to integrate security awareness without interrupting development, whether that’s by ensuring assignment completion before code is pushed or verifying training when a commit references a GitHub Security Advisory (GHSA).

The Assignment Completion Hook
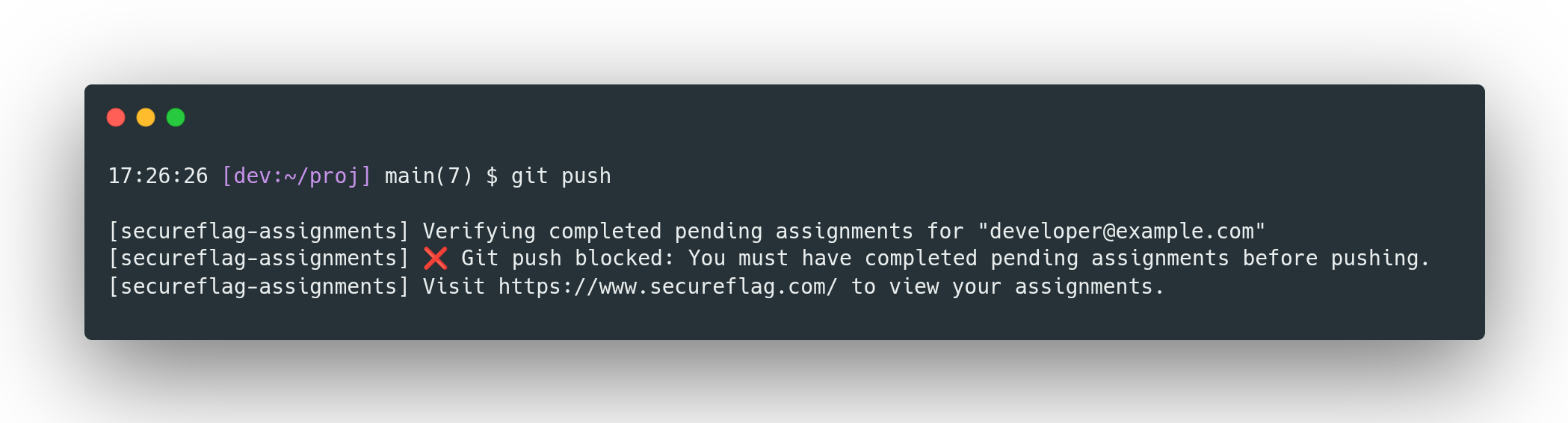
The Assignment Completion Hook ensures developers meet your organization’s training and compliance requirements before pushing code to remote repositories.
The hook can be configured to check one of three assignment requirements:
-
Completed initial assignments: All onboarding or initial training assignments are complete (default).
-
Completed pending assignments: All currently pending assignments are complete.
-
No expired assignments: The user has no assignments that have passed their deadline.
If the configured requirement isn’t met, the push is blocked. Developers receive clear instructions and direct links to the relevant SecureFlag modules, making it easy to complete the necessary training.
The Advisory Training Commit Hook
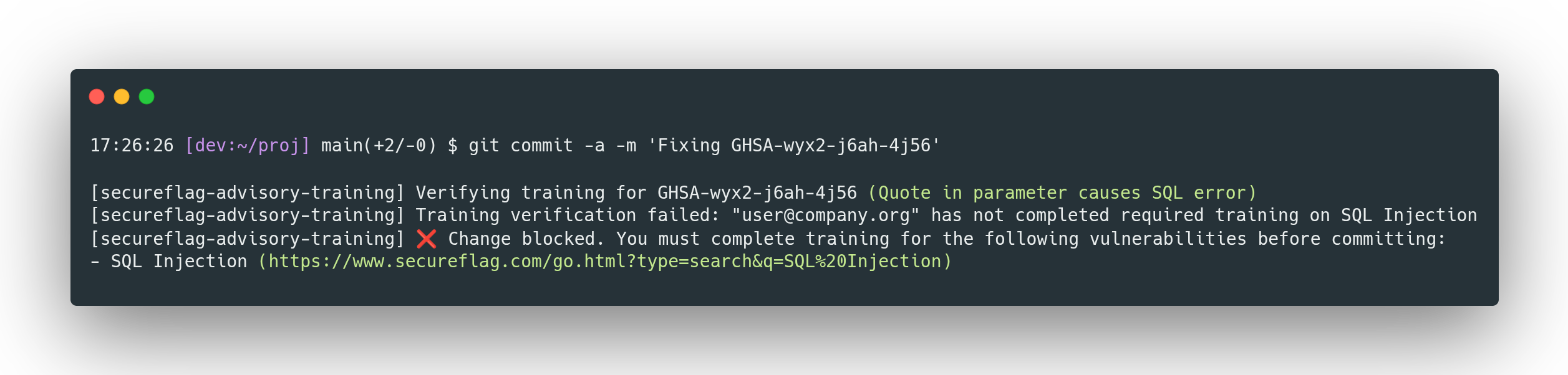
Our Advisory Training Commit Hook makes it easy to embed security awareness whenever code is committed.
Each time a commit is made that references a GHSA, the hook checks if the required SecureFlag training for that vulnerability has been completed.
Here’s how the hook works in practice:
-
The hook scans the commit message for GHSA IDs.
-
For each ID, it verifies training status via the SecureFlag API.
-
If the training hasn’t been completed, the commit is blocked, and the user is given direct links to the relevant SecureFlag modules.
Installation Overview
Here’s an overview of how to get started:
-
Add the hook to your repository: Make it available in your Git environment so it runs automatically.
-
Set up dependencies and access: Ensure the hook can communicate with your SecureFlag account.
-
Configure assignment requirements: Hooks can enforce assignment completion, GHSA-based training, or other configurable compliance policies.
-
Start committing or pushing: Once set up, the hook runs in the background, checking that requirements are met before code reaches the remote repository.
For more detailed installation guidance, see the repo instructions.
Benefits for Development Teams
Security checks don’t have to get in the way of writing code. When integrating SecureFlag training directly into Git, developers get instant feedback directly where they work, without having to switch tools and do extra steps.
Instead of treating training and compliance as separate tasks, the hooks make them part of the Git process. Developers can stay focused, and teams can be sure that vulnerabilities are managed before code is committed and pushed to the repository.
This integrated approach keeps organizations proactive about security and reinforces secure coding best practices without impacting delivery times.
About SecureFlag
SecureFlag helps developers and teams build safer software from the very first keystroke.
Through hands-on labs, interactive learning paths, and tools like the Git hooks, SecureFlag turns security training into something practical and integrated into everyday practice.
From secure coding to vulnerability awareness and staying up to date with the latest advisories, developers get guidance they can use immediately, while organizations benefit from stronger security standards.