Given that Salesforce supports thousands of businesses worldwide, it’s become a tempting target for attackers. Earlier this year, a researcher uncovered a serious SOQL injection flaw in a default Salesforce Aura controller, showing that enterprise platforms can be vulnerable when secure coding practices aren’t followed.
SecureFlag’s new Salesforce Apex labs are here to help developers recognize these risks and prevent them through practical, hands-on training.

The Security Side of Salesforce Apex
Apex is Salesforce’s proprietary programming language, used to extend the platform’s capabilities and implement custom business logic. It allows developers to automate workflows and create customized applications on top of Salesforce.
Custom code written in Apex also faces the same risks as code written in other enterprise platforms. Aside from SOQL injection, other vulnerabilities, such as Insecure Direct Object References (IDOR), cross-site scripting (XSS), or misconfigured access controls, can cause damage if the code isn’t secure.
If your organization doesn’t want sensitive customer data exposed or unauthorized actions taken, it’s essential to understand how these risks arise and how to prevent them.
The Risks of Insecure Apex Code
Even though Salesforce has a strong security framework, custom Apex code can still introduce vulnerabilities that aren’t covered by the platform’s built-in controls.
Last year, a security advisory warned users about Apex coding errors and misconfigurations. This happened after multiple government organizations and companies had customized or added features to their Salesforce Apex code that leaked sensitive information.
Security guidelines do exist that include enforcing CRUD and field-level security (FLS) checks, using parameterized queries, and proper data-sharing models. However, understanding these principles is different from actually applying them.
Developers may unknowingly:
-
Leave input unvalidated, enabling SOQL injection, XSS, or other injection attacks.
-
Misconfigure access control and expose data through improper sharing rules.
-
Use insecure patterns in controllers that bypass security checks.
-
Fail to enforce CRUD/FLS checks.
-
Expose sensitive data through debug logs or improper error handling.
These are real issues that can affect organizations using Salesforce, as shown in the earlier example. All it takes is a single overlooked line of code to grant unintended access to sensitive data or allow a malicious actor to manipulate business logic.
Learning Security Through Practice
SecureFlag’s new Apex labs engage developers in realistic Salesforce coding scenarios where vulnerabilities exist. Instead of reading about what can go wrong, learners see the issues firsthand and get the chance to fix them.
Each lab walks through a specific security flaw that developers may encounter, such as:
-
Lack of object-level and field-level authorization controls.
-
A stored XSS vulnerability that’s hidden in a page element.
-
A spoofable frame that allows clickjacking attacks.
-
An SOQL injection in a business-critical page.
Developers find vulnerabilities and use various practical methods, from secure coding practices to access controls and input validation, to resolve them.
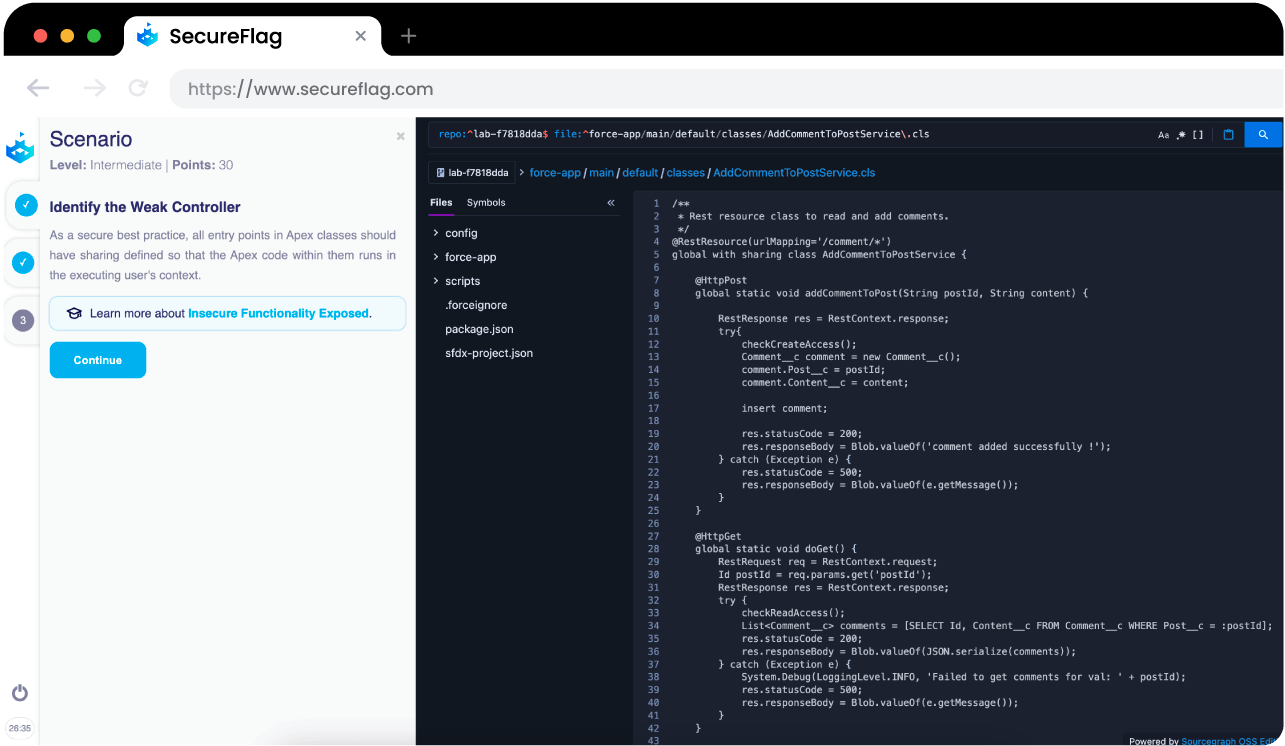
Secure Coding Training for Salesforce with SecureFlag
The Salesforce Apex labs give developers an engaging and fun way to learn how to code securely. With hands-on training, developers learn to identify and fix vulnerabilities in realistic code scenarios, improving their understanding of Apex security and reducing risks.
Organizations that incorporate SecureFlag’s labs into their training programs can help keep their Salesforce applications secure.