All applications risk being hacked without robust, properly configured application security controls in place. Whereas employing a team of ethical hackers may help provide assurance on the system’s resilience post-deployment, having a secure Software Development Life Cycle (SDLC) better equips organisations in addressing security concerns at the foundational level. Building security early in the SDLC is more cost-efficient and scalable, enabling organisations to identify and correct security issues earlier in the development life cycle.
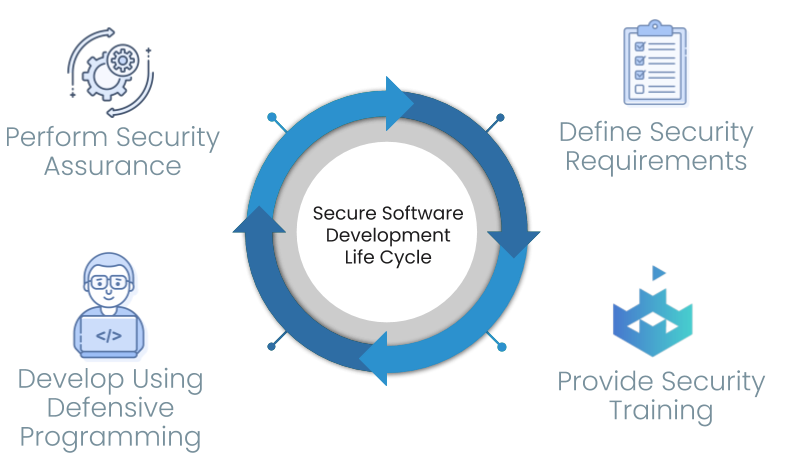
Copious, reliable information concerning the implementation of secure SDLC processes is readily accessible. Complementarily, a few simple yet critical actions can be taken to ensure your AppSec regimen seamlessly integrates with your SDLC. These actions are as follows:
-
Define security requirements, establishing a baseline of what constitutes “good” application security, both as defined by the broader developer community and as it applies to your organisation (more below).
-
Conduct training with developers and DevOps personnel focusing on your organisation’s specific AppSec requirements.
-
Develop using secure coding standards and reuse approved tools.
-
Perform security testing combining static, dynamic, and open source analysis.
Security requirements that establish a baseline of what constitutes good application security are best defined during the initial planning and design phases. These requirements usually come from multiple correlative sources, such as legal and industry requirements (e.g. PCI-DSS, HIPAA, etc.), internal policies and coding practices, as well as known threats and lessons learned from previous incidents. Providing AppSec training to the development and testing teams increases the understanding of security issues and enables the development of more secure software from the start.
MITRE has catalogued more than 700 different kinds of software flaws as part of its CWE Project, describing numerous, diverse paths that all lead to software insecurity. Understanding modern security defects and attack methods, and developing the capacity to protect against these flaws, is a crucial aspect of modern secure application development. When developers know what to look and test for during the development phase, the number of security defects introduced will naturally be reduced. In addition, when the testing team receives application security training, they are more likely to spot a security concern before the application is pushed to the next phase of development.
Uniting developers in training initiatives results in greater confidence in the overall security of the application. Additionally, it engenders a deeper appreciation of the importance of application security and its prevalence within the team and the interconnected parts of the organisation. Importantly, training reduces costs and resources in addressing security bugs which, left unchecked, may re-emerge down the track with grave ramifications.
While developing software, make yourself and your team aware of secure coding standards and patterns. The SEI CERT Coding Standards are great resources for defensive programming in; Java, C, C++, and Perl. The Japan Smartphone Security Forum (JSSEC) maintains the highly regarded Android Secure Coding Guidebook.
To ensure your software meets the security requirements set for the project and is also resilient to attacks, it is crucial to integrate security testing activities as part of your SDLC. The OWASP Application Security Verification Standard and its mobile counterpart provide a basis for testing your applications’ technical security controls, and they also furnish a list of secure development requirements for developers to integrate into their coding practice.
The entire process is meant to be iterative; results from security assurance activities should be used to augment security requirements and tune AppSec training to focus on the areas where gaps have been identified. If developers are trained in defensive programming techniques, new code that is produced won’t be affected by the same security defects.
Some of the fallouts of an ineffectual AppSec program
There are a multitude of negative impacts stemming from ineffectual AppSec programs, so careful consideration and procurement of the right AppSec platform is a prudent measure for any organisation appropriately managing their risk. Security holes identified late in the software development process are far more costly to remediate than when discovered early on. In addition, addressing security bugs in isolation and not at the root cause substantially increases the likelihood of code flaws being layered on top of code flaws lower in the stack, thus compounding the risk of exploitation. However, the cause for most alarm is the heightened potential for exploitation by malicious actors taking advantage of an AppSec program’s ineffectiveness. The legal, reputational, IP, and economic fallout from breaches that exploit poorly written code could mean the end of the organisation.
Considering automated security scanning tools can only identify a subset of security vulnerabilities, ensuring your developers possess (and maintain) the right capacities to produce secure software merits your undivided attention. Vulnerabilities identified in your production application could result in:
-
Reporting of product vulnerabilities on public websites.
-
Brand erosion.
-
Diminishing of future profitability, or even negative growth.
-
Stiff fines levied by the relevant authorities when customer data is leaked/stolen.
Many companies appreciate this and already have AppSec Training programs in place; however, optimal results remain elusive. While slides, videos, and quiz-based training methods may have some limited success in raising generic security comprehension, they are inadequate at covering the complexity of technology in use today, nor in embedding the information in a manner that will be applied to reason and solve problems in dynamic environments. A hands-on, practical secure coding training is the only way to ensure that developers internalise the required skills and knowledge and are actually capable of applying it when addressing real-world security problems.
What are the common AppSec training needs in your organisation?
Training experts often conduct an initial training needs analysis (TNA) to understand the unique learning requirements of each trainee. One approach - especially in the capricious world of application security for developers — does not fit all needs. Computer-based training sessions, such as presentations, quizzes and multiple-choice questions, scale well for large enterprises but don’t translate to hands-on skills. Unsurprisingly, certain old, well-documented vulnerabilities are still seen in many applications in the market today.
Our exhaustive TNA shows that:
-
Every developer in an organisation has individual AppSec Training needs, typically influenced by the seniority and experience of the developer, as well as by the specific technology the developer works with.
-
New hires will come into your organisation with different levels of AppSec skills, all of them initially lacking awareness of internal coding guidelines and procedures. Ineffective training means considerably slower onboarding of new hires.
-
Seasoned developers are often seen as the point of contact between the security and the development teams; they require training that empowers them to act as Security Champions, which in turn allows security to scale throughout the organisation.
-
AppSec training should replicate your development environment to be as relevant as possible. Developers face the daunting and frankly unnecessary task of bridging the gap between training inputs and real-world challenges if the training environment is designed to answer multiple-choice quizzes instead of simulating live scenarios.
-
Developers who are not trained adequately in secure coding present a huge risk to your company and its customers. Although we couldn’t find any studies collating and quantifying the damage caused by insecure code, and by extension, the damage caused by the developer of stated code, it seems safe to say that the risks are incredibly high.
How does SecureFlag deliver the required training results?
To deliver individualised application security training, we built SecureFlag as a highly customisable and affordable AppSec training platform.
With SecureFlag, developers learn how to identify vulnerabilities and remediate the code of vulnerable applications running in real development environments accessed via a web browser. The platform offers 100% hands-on training, with no multiple-choice questions involved, and uses an engine able to live-test code changes, instantly displaying whether the code has been fixed and awarding points upon exercise completion.
It seamlessly fits into your training and development environments; developers are trained with the same IDE used to develop the product. Be it ground-up defensive programming training for new developers or specific training inputs for the experienced, you can start a dedicated, online secure coding class in seconds. SecureFlag aligns well with the hectic pace of your development environment—with little effort. You achieve this through individualised AppSec learning paths to align developer skills to the company’s mission with training that adapts to previous results and goals.
SecureFlag provides a gamified experience where users can assemble into teams, track their progress through a leaderboard, and create time-boxed tournaments to get the entire developer community involved. Learning Paths are training courses that enable participants to attain expert, usable knowledge in relatively small steps. When candidates complete a Learning Path, they receive a SecureFlag certification which needs to be maintained by taking refresher exercises throughout the year.
With special features and easy integration into both small and enterprise environments, you will be able to effortlessly service increased numbers of developers and the resulting additional complexities of training for enlarging teams. For example, if you have recently undergone a mass hiring of new developers, setting up a dedicated Learning Path for each of them is several clicks away. Additionally, the efficacy of the platform is complemented by its flexibility; in the event that a new vulnerability has been recently detected or a regulation update has been announced, you can bring your entire development team up to speed by instantly setting up the corresponding vulnerability scenarios in SecureFlag.
SecureFlag offers you another major advantage. By collecting metrics during every training session, SecureFlag tells you exactly where the risks lie in your development team. For instance, the training metrics may indicate that some developers are not proficient in defensive programming against SQL injections. To address this issue, SecureFlag automatically shifts the focus of the training to those developers in order to fill the identified gap. In this manner, you can effortlessly implement iterative and individualised training through SecureFlag.
Why is practical AppSec training for developers vital for your organisation? Because the genesis of every online attack inevitably begins with a keystroke. SecureFlag ensures that each successive keystroke performed by the developer is as real as the real-(cyber!)-world itself, applying a cost-effective training system that educates an organisation at the level of the individual developer. Not a bad way to incentivise your staff to augment their secure coding skills, reduce your risk, and elevate the resilience of your bottom line!