Even to the layman, the sheer volume of successful high-profile attacks on public and private entities the world over speaks volumes about the state of defensive security concerning the management and protection of technological infrastructure. From small family-run businesses with 5 employees, to purportedly impenetrable government and defence organisations like the National Security Agency, attackers continue to gain the upper hand in the ongoing fight to extract secrets, and seemingly infinite budgets are evidently ineffective at stemming the low. In short, getting defensive security right is an incredibly difficult job.
With all of that in mind, however, there continues to be impressive advancements in the evolution of defensive tools and methodologies aimed at detecting and eliminating threats, with much of this improvement hinging on a perennially more transparent approach to the release of post-breach analysis. Lessons learned that remain obfuscated ensure other entities will suffer the same attacks. It is this last point regarding the dissemination of best practices that paves the way for more wins against a persistent adversary. In this article, we’ll explore a small fraction of our own lessons learned at the coalface and discuss just how crucial it is to emphasise a heightened level of security awareness and implementation beginning at the first keystroke.
Our commitment to offering the highest level of training to all disciplines on our platform has led to our partnering with CYS4, a company with a vast amount of experience in training SOC personnel. Throughout the numerous Red Teaming and Incident Response engagements they have undertaken, CYS4 has again and again identified the same, recurring issue that lays bare the porous nature of a defensive architecture: Security Operations Centres (SOCs) often possess limited capabilities to identify and stay abreast of rapidly evolving threats.
Importantly, this lack of capacity doesn’t necessarily boil down to a lack of tooling - indeed, there are a plethora of highly sophisticated tools that have been developed and deployed in organisations. Where this all gets complicated is in the adequate implementation of all of these moving parts, and, since we haven’t unburdened our humanoid selves of all SOC responsibilities in favour of entirely AI-driven defence, we - us flesh and blood folk - are continually proving to ourselves just how fallible we are! Crucially, though, all is not lost - modern, hands-on, effective training, training, training… and more training, has a huge impact on the effectiveness of security teams.
The life & times of a SOC Analyst
Life as a SOC Analyst was never meant to be easy. It is a task that necessitates dogged perseverance in the face of a seemingly never-ending barrage of false positives and an unflagging attention to detail despite it. Because buried within the benign communications of the devices in the network are the telltale signs of sophisticated adversaries. Knowing how to separate one from the other, i.e., ‘normal’ from ‘malicious’ behaviour, particularly when attack techniques pivot and update, is the job description.
It is essential for every SOC analyst to be able to investigate potential compromises within the organization as quickly as possible, in accordance to known «standards», such as the MITRE ATT&CK framework, which represents the gold standard in defensive security analysis, preparation, and mitigation. However, although one can review a technical handbook packed to the brim with theoretical exercises and scenarios, cyber security is more than many things a truly hands-on endeavour.
Teams need to be supported with real-world, «Hands-on Training» in order to effectively identify, recognize and fully understand security alerts in a SIEM, attack chains and expected paths an adversary will take, and most importantly, attacker behaviours that deviate from the predictable. Again, attacker creativity must not be under-estimated - refer to the opening paragraph! - and training in live environments is how one must prepare for the real-world.
So, I need to train for real - what’s on offer?
The absence of tactile training based on real-case scenarios was the catalyst for the creation of the SecureFlag platform, and with our partners at CYS4, a simulated environment for SOC Analysts is now a reality. Whilst most of the existing courses are hugely on dependent on theoretical documentation, our platform ensures both theoretical and practical notions are delivered in equal, effective measure. The analyst will first study the main components present in enterprise environments and then move towards realistic attacks scenarios inside computer networks to recognize how cybercriminals exploit such elements. Finally, the analyst will learn how to apply the appropriate mitigation measures and the best detection strategies.
The below comparison between traditional learning and our updated methodology conveys just how divergent these two approaches are.
Traditional Methods
Classroom Training
❌ Expensive both in terms of time and cost investment: companies must pay on-site trainers to prepare their SOC teams. This could take up a lot of training hours, possibly forcing exhausting schedules.
❌ In many cases, there is less distinction amongst the levels of capacity a team of analysts possess, and even if these differences are taken care of with multiple classes, they are still not tailored to the individual learner.
❌ Courses are often one-time events that load the user with a lot of information in a short amount of time: a typical training session will generally condense a comprehensive subject into a 4-hour session. Think of this being akin to cramming for an exam… how much of the information that led to a pass mark - or even top marks - is effectively retained several weeks post-test?
Video lectures & Multiple-Choice Questions
❌ Starting with the obvious - this isn’t a hands-on approach. Sure, videos can be a great tool to help visualise processes and structures - indeed, our platform has developed a range of in-house animations as accoutrements - but without immediate integration into exercises that test hands-on efficacy in identifying adversaries in a simulated live-environment, visualisations alone underserve the analyst. In addition, video lessons are often limited to a small set of cases, preventing the analyst from trying out alternative techniques during the learning process.
❌ Multiple choice questions - the bane of effective learning. Many providers offering training, whether that be in a classroom or passively via video, evaluate their participants’ comprehension with multiple choice quizzes that present a selection of answers that simply cannot precisely evaluate whether the analyst understands the approach leading up to the answer.
The SecureFlag Method
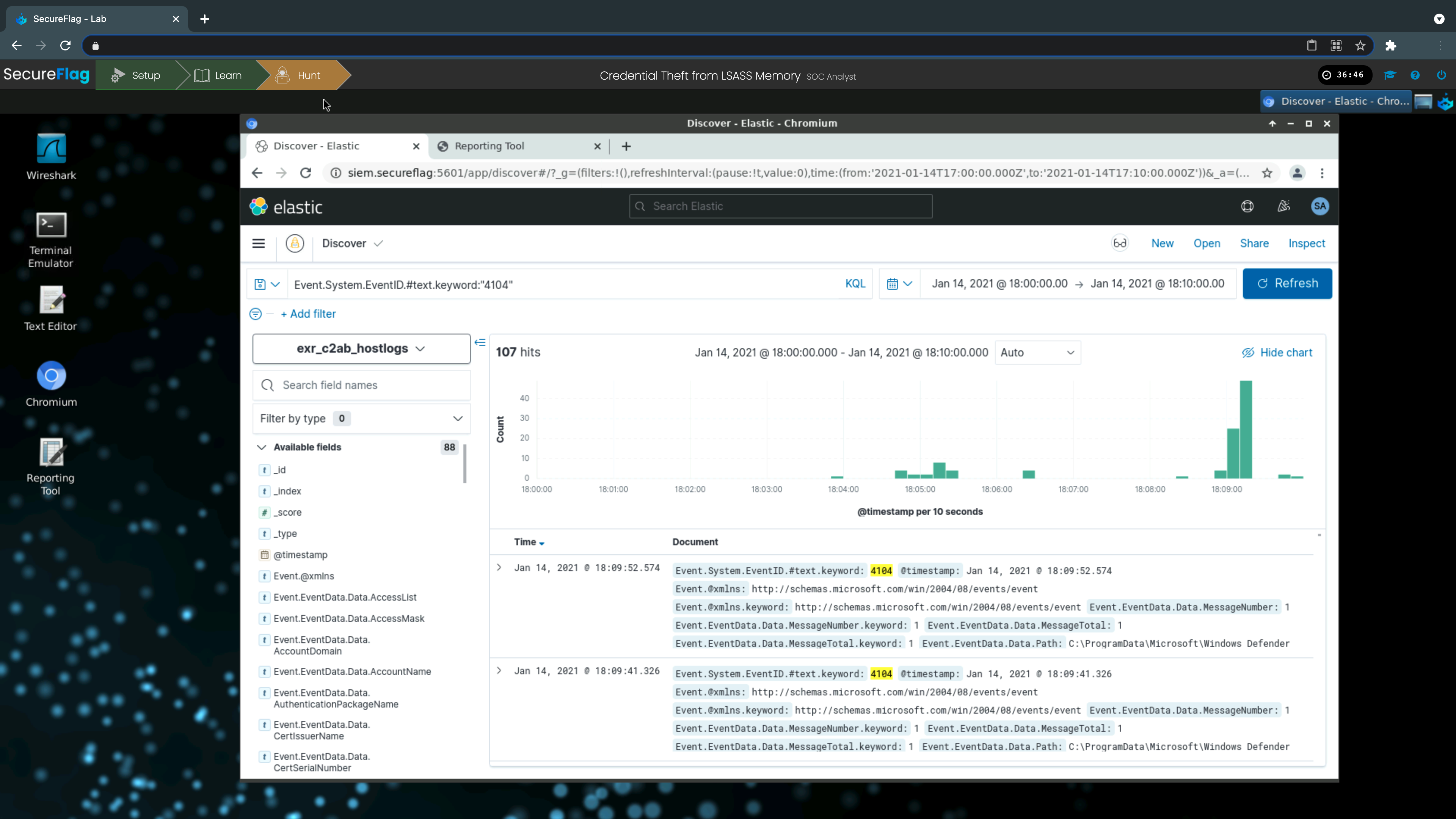
Hands-on, real-world scenarios are at the core of our platform. We afford our practitioner the opportunity to identify and respond to incidents in a manner that is quite literally an exact replica of the same thing. Throughout the process, the analyst will explore an individualised training path to understand and recognize the principal attack methodologies used by the most common Advanced Persistent Threats (APT). Once these methodologies are deeply understood, practitioners will tackle defensive measures based on the MITRE ATT&CK framework that they can put to the test.
All exercises take place in a custom laboratory set up by the CYS4 team atop the SecureFlag platform, recreating realistic infrastructural structures based on Active Directory environments and POSIX systems. Just as in a live environment, logs, enriched by firewall, network, and systems information, are extracted and assessed by the analyst who is guided toward the most appropriate solution based on the data at hand.
When they make a misstep, they will be informed as to why, and be able to adjust their approach accordingly - again, in real-time. To make things even more realistic, the perennial competitive cat-and-mouse game that professional SOC Analysts and their attackers partake in daily in real-world entities is recreated in our Tournaments, affording fellow learners to compete with one another in a fun and engaging manner, learning the tough way… albeit in a benign - safe - environment!
Lastly, the security landscape is constantly moving, evolving, and testing the limits of all sides involved. As such, we offer a large landscape of exercises and scenarios that are continually updated and augmented with the latest attack and defence techniques from real-world successes and failures.
Advanced Practical SOC Training Platform
✅ Guide the SOC Analyst on an individualized, responsive learning path that sees them identify, exploit, understand, and resolve the same security issues faced by live teams the world over.
✅ Learning is individual! The tools a particular practitioner uses in the workplace are available on the platform… and if they are the ‘wrong’ tools for the job, the SOC Analyst will quickly find out why and adjust accordingly!
✅ Continuously updated training - if you see a novel attack in the wild making use of previously unseen techniques, you can be sure we will be dissecting and integrating it for our community to be prepared.
✅ A knowledge base amassed from years of research, hints, and live corrections, real-time results and suggestions are all always available in our dedicated environment, accessible in seconds, via a web browser.
✅ Hybrid learning with support as needed from SecureFlag & CYS4 specialists.
… and then there are the Tournaments!
✅ The provision to organize time-based challenges to increase collaboration leveraging team building.
✅ The provision to compare results to identify personal and team growth.
✅ Participants use an active approach to solve safety problems.
✅ Points, Trophies, Certifications… and bragging rights!
Getting Started
The SecureFlag platform is the perfect tool for Developers, DevOps engineers, QA Engineers, SOC Analysts, Incident Responders, and IT personnel charged with securing their environments. It is tailored to the learner’s requirements, adapts to their progress, and rewards by ensuring the lessons learned and successes experienced are embedded into their daily working lives.
To learn more about what SecureFlag can do for you and your team, contact us to take our platform for a test drive.