For a sector that swears by cutting-edge technology, it’s somewhat ironic that the software industry still heavily relies upon an over 60-year-old programming language. However, not only is the language in question - COBOL - in use today, it is often tied to critical data and functions on mainframe systems and has proven over the years to be resilient and malleable.

According to a report by IBM in 2019, there has been a notable shortage in the number of COBOL programmers since most of the old guards are retiring, and the fresh crop is more interested in newer languages. Unfortunately, this decline in COBOL uptake has resulted in a serious skill gap, a conundrum on the minds of many technologists with oversight of COBOL systems that will soon lack the operational hands to maintain them adequately.
A superficial rebuttal of this argument is that it’s high time to simply design a new language - one more ‘age-appropriate’ - and do away with COBOL altogether. However, dig a little deeper, and we find this ‘start anew’ approach is plagued with disincentives, including the outlandish costs required for such an overhaul, and simply the fact that COBOL is, in the main, still robust and resilient and has proven to be a reliable workhorse for decades.
But reliable though it may be, COBOL is still a programming language and is thus susceptible to poor implementation at the hands of its human implementers. And if all the knowledge leaves the building, the question is: how can enterprises confront the security vulnerabilities and mitigate the risk associated with the use of COBOL?
What is COBOL?
COBOL is an acronym for Common Business-Oriented Language. It’s a computer programming language explicitly designed to develop business applications for mainframe computers used in business, finance, and government organizations. It was developed in 1959 by CODASYL as an imperative language but redesigned as an object-oriented language in 2002. Micro Focus, IBM, Fujitsu, and GnuCOBOL are the leading vendors of COBOL compilers.
COBOL gained popularity quickly, primarily due to its English-like syntax, which was easy to comprehend and learn. COBOL is still relevant because its accuracy is unmatched — an element that is essential for organizations in sectors like banking. Another reason is legacy lock-in, where enterprises might have considered replacing applications written in COBOL with something newer but lacked the wherewithal or case to present to management. Indeed, the IT functions in many organizations are still - to this day - relegated to the ‘if it ain’t broke, don’t fix it’ pile of documents on the CEO’s desk!
Security Vulnerabilities in COBOL Systems
As robust as it is, a COBOL program is still an application, and like any other application, it is not free from vulnerabilities. For seasoned COBOL practitioners, most all of these security vulnerabilities can be easily mitigated as years of working in the field have elicited what to watch out for. However, as stated in the introduction, there is an overwhelming shortage of COBOL experts in the market and a lack of awareness about security risks as a result. Some major technical security vulnerabilities are:
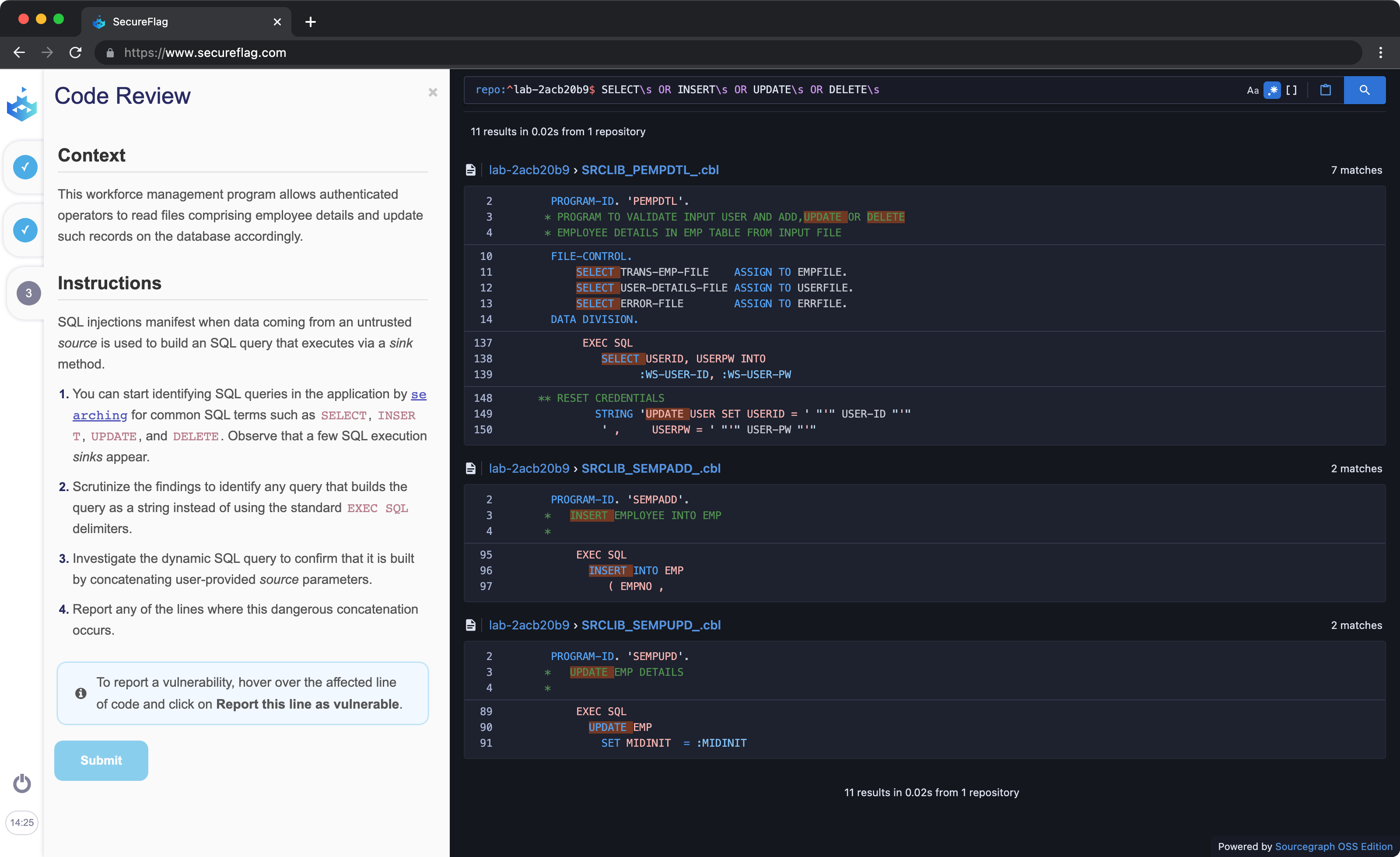
COBOL uses a lot of SQL statements that allow data to be ingested in and out of the database. Non-parameterized dynamic SQL statements can be a source of SQL injection vulnerability. Consider the following code snippet:
STRING "INSERT INTO TBL (a,b,c) VALUES (" X "," Y "," Z ")" INTO MY-SQL
EXEC SQL PREPARE STMT FROM :MY-SQL END-EXEC.
EXEC SQL EXECUTE STMT END-EXEC.
The non-parameterized query directly uses the user input to build the statement. If any of the host variables X, Y, and Z come from an untrusted source, it can lead to SQL injection.
Many other security vulnerabilities can affect the software running in your mainframe: from non critical code “smells” to insufficient security controls, such as input validation. Since processed data may come from untrusted input, any kind of injection attacks, like path traversal or code injection, are possible. This happens because there are insufficient security validation controls in place, meaning the attackers can get unauthorized access to the underlying system of the affected application.
Best Security Practices for COBOL Systems
The exploitation of vulnerabilities is inevitable unless the workforce is attuned to dangerous implementation and configuration and follows safe coding practices to protect the mainframe and the applications. This rule applies as much to COBOL as it does to every other language designed, built, and implemented in any stack.
However, best practices do exist, so it is essential that programmers and enterprise stakeholders ensure they adhere to them to avoid any cybersecurity incidents:
- Strictly follow safe coding practices that include data encryption, multi-factor authentication, proper input validation, and enforcement of session timeout.
- Do not use outdated cryptographic algorithms that might weaken the overall security posture.
- Do not ignore errors, as examining errors can expose vulnerabilities and make debugging easier.
- Do not hard-code secrets — a practice of embedding application passwords into the source code — that might expose it to insider threats.
- Have at least one security expert in COBOL programming on your payroll. The expert should be experienced in incidents related to security vulnerabilities.
Hands-on Training in COBOL Labs with SecureFlag
The retirement of COBOL programmers and the resulting skill gap have raised concerns among organizations that use legacy COBOL systems. Rewriting these systems into newer languages is not as easy as it sounds, at least for the foreseeable future. So, it has become imperative for businesses to train their relatively newer employees in COBOL.
SecureFlag takes care of transforming your workforce into industry experts in secure coding, with bonafide hands-on training in COBOL. SecureFlag goes a step further than your average run-of-the-mill course frameworks that bombard trainees with boring slideshows and quizzes that are practically ineffective. We believe in simulating real-world vulnerabilities with our interactive practical sessions that align perfectly with your enterprise’s software and business goals.
To know more about SecureFlag’s 100% practical secure coding training platform for COBOL, contact us today.


