At the OWASP Global AppSec conference held in Dublin this past February, SecureFlag attended an intriguing talk by Gil Cohen and Omri Inbar from CYE who introduced a novel hacking technique known as FrontJacking.

What is FrontJacking?
FrontJacking is a combination of CRLF injection, HTTP request header injection, and XSS that exploits a poorly configured NGINX reverse proxy deployed in a shared hosting environment.
By leveraging this technique, attackers can inject a new host header, seize control of the frontend server, and replace the accessed server with one under their control. This enables them to execute reflected XSS and phishing payloads while circumventing any existing defensive measures.
In simpler terms, FrontJacking allows attackers to display a completely different website, while maintaining all the security information from the original website such as TLS certificates and Content Security Policy.
For instance, an attacker can send a payload URL of https://victimwebsite.com/PAYLOAD and display a different website such as https://attacker.com, bypassing all security mechanisms.
“People often ask us, wait, how serious is FrontJacking? Is it a severe vulnerability? Our answer is it really depends, would you consider cross-site scripting a severe vulnerability, as depending on the system it can be used for phishing, open redirects and sensitive information disclosure but it really depends on what the vulnerable website is and who can access it.” - Gil Cohen
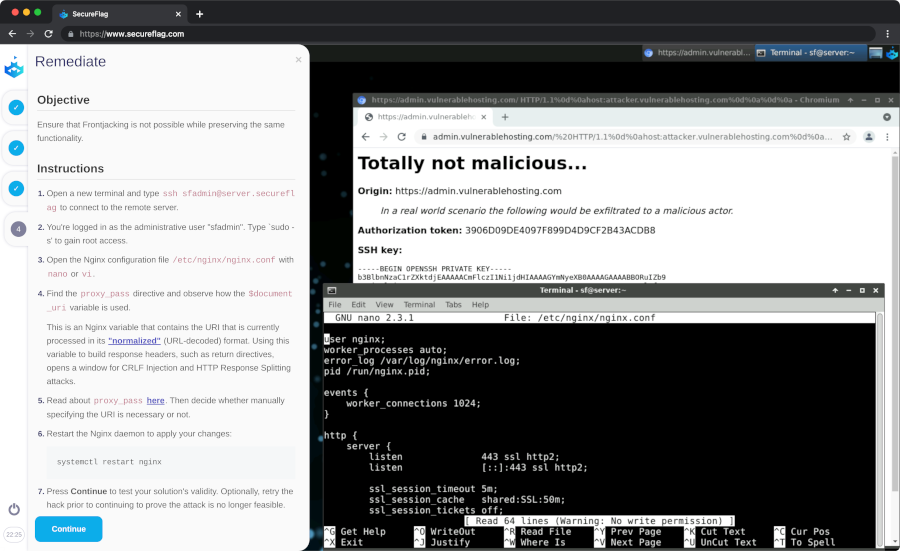
Gil and Omri’s talk piqued the interest of SecureFlag, and during our interaction at the conference, we agreed to collaborate and build a training lab to demonstrate this new hacking technique. SecureFlag’s lab offers a secure environment for developers and security professionals to explore and comprehend the implications of FrontJacking, enabling them to devise countermeasures against potential future exploitation by cybercriminals.
Despite the non-trivial nature of modern hacking techniques, SecureFlag’s R&D team of security specialists were able to recreate the environment and misconfiguration required for the exploit to take place.
The lab was published a few weeks after the conference, allowing all our customers to gain a better understanding of the FrontJacking technique. The lab received great feedback and not only served as a demonstration of the technique, but also helped to spread awareness of the vulnerability to different companies.
The advent of FrontJacking underscores the ever-evolving landscape of cyberattacks and the ongoing necessity for vigilance in safeguarding ourselves and our organizations. The joint effort between CYE and SecureFlag to develop a lab showcasing this technique also emphasizes the value of knowledge-sharing and collaboration within the cybersecurity community in order to stay ahead of emerging threats.
If you would like to learn more about “What is FrontJacking”, check out the following CYE blog post “FrontJacking: A New Attack That Threatens Reverse Proxy Servers”.