When you can understand what OWASP SAMM is and how to integrate the framework with SecureFlag, you can elevate your software security practices.
What is OWASP SAMM?
The Open Web Application Security Project’s Software Assurance Maturity Model (OWASP SAMM) was created to help organizations implement, evaluate, and improve their software security posture. With its foundation rooted in industry-accepted principles, the model provides an effective strategy to integrate security into the software development lifecycle (SDLC) through its business function-oriented approach.
The OWASP SAMM offers a measurable and incremental strategic framework, enabling organizations to tailor and prioritize their security practices based on their specific needs and resources. The core objective of SAMM is to assist in understanding, formulating, and executing a balanced software security assurance program.
The Model Overview
The OWASP SAMM framework comprises five business functions, each focusing on different aspects of software development and its inherent security considerations.
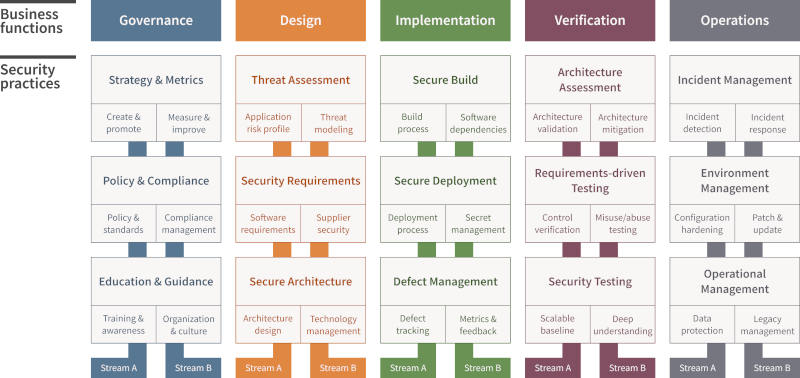
Governance
The Governance function emphasizes establishing software security as a core part of the business process. This involves the development of policies, strategies, and metrics, ensuring the organization has a defined roadmap for software security. It also encompasses third-party management, focusing on the security practices related to vendors and service providers.
Design
The Design function of the OWASP SAMM framework revolves around integrating security principles right from the initial stages of software development. This includes threat assessment, secure architecture design, data classification, and protection strategies. The objective is to incorporate a ‘security by design’ approach that reduces vulnerabilities in the final product.
Implementation
This function focuses on maintaining security during the software coding phase. Secure coding practices are encouraged, including the use of approved libraries and secure build processes. It also highlights the importance of defect management, ensuring any security bugs discovered are managed and remediated appropriately, i.e., in line with up-to-date best practices.
Verification
The Verification function involves the use of various testing and review techniques to ensure that the software developed is as secure as planned. This includes design review, code review, and security testing, among others. The goal is to identify and address any potential security issues before deployment.
Operations
The Operations function of the OWASP SAMM framework aims to ensure security in the software’s operational environment. This includes incident management, environment hardening, and operational management. It emphasizes maintaining security during the deployment phase and post-deployment, ensuring a robust security posture throughout the software’s lifecycle.
A Focus on the Training and Awareness Stream
A key aspect of the Governance function is the Training and Awareness stream. This stream highlights the importance of cultivating a security-conscious culture within an organization. The idea is to ensure that all relevant stakeholders, from developers to senior executives, are aware of security best practices and understand their role in maintaining a secure SDLC. This is a key principle of OWASP SAMM.
Regular training sessions, workshops, and awareness campaigns play a pivotal role here, as these activities help to keep the organization’s personnel updated with the latest security trends, threats, and mitigation strategies, thus fortifying the organization’s overall security posture.
How to Use SecureFlag to Improve Your Security Across The Entire Software Lifecycle
SecureFlag is a comprehensive platform that provides interactive, hands-on application security training to software development teams. Its unique approach blends training with the existing SDLC, allowing developers to learn and apply security principles in real-world situations.
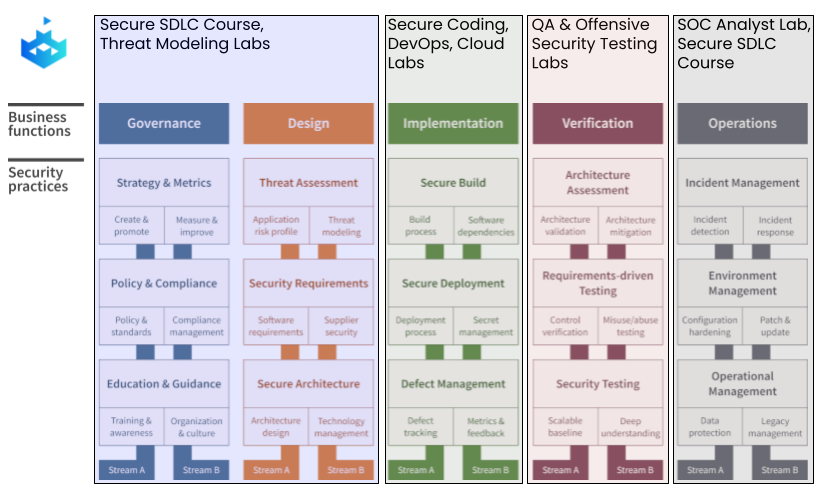
This is achieved by delivering tailored training to different segments of your workforce, thus supporting each SAMM business function:
-
Governance: SecureFlag’s SDLC suite and accompanying (and unique!) Threat Modeling labs are specifically designed for decision-makers in charge of this function. These training resources help them acquire the necessary skills to effectively navigate and manage the software security landscape.
-
Design: Architects and developers overseeing design functions can leverage SecureFlag’s Secure SDLC class and Threat Modeling labs. These resources aim to impart a solid understanding of secure design principles and proactive threat management.
-
Implementation: For builders, such as developers, DevOps, and Cloud engineers involved in this phase, SecureFlag provides tailored Coding, DevOps, and Cloud Labs. These labs focus on instilling secure coding practices and promoting the development of secure applications and infrastructure.
-
Verification: Testers and QA personnel are well catered to with SecureFlag’s QA Secure Testing labs and Exploitation Labs. These tools empower them with practical knowledge and techniques to validate the security of the products effectively.
-
Operations: Security operation teams involved in the Operations function can benefit from both the hands-on SecureFlag SOC Analyst Labs and the accompanying Secure SDLC course. These resources bolster their skills in maintaining a secure operational environment throughout the software lifecycle.
Implementing large-scale secure software development practices is a massive undertaking. Yet there’s no getting around it if an organization wishes to a) minimize risk and b) avoid being hit with hefty fines for non-compliance. The exact approach to integrating such a program will vary from organization to organization but tried and tested frameworks such as the OWASP SAMM offer a well-thought-out roadmap toward success.
And the optimal tool for the practical training and culture-building aspects of the model? SecureFlag! SecureFlag acts as a powerful tool to instill a culture of security within your organization by not only aligning with the OWASP SAMM model but also augmenting its effectiveness, providing a practical, hands-on approach to securing your entire software lifecycle.
Implementing the OWASP SAMM and integrating platforms like SecureFlag can elevate your software security practices to the next level. They provide a roadmap for continuous security improvement, instilling a security-conscious culture within your organization, and ensuring the safety of your software across its lifecycle.
Contact SecureFlag today to book your demo and initiate a free trial of the platform to understand why hundreds of organizations have chosen SecureFlag for their secure coding training program.


