In today’s fast-paced software development environment, safeguarding Continuous Integration/Continuous Deployment (CI/CD) pipelines is crucial. Acknowledging the significance of and demand for specialized education in this area, the team at SecureFlag is incredibly proud to unveil a completely new set of hands-on labs that specifically cater to CI/CD Security.
A Closer Look at SecureFlag’s CI/CD Security Labs
Designed to address security issues that arise in prevalent CI/CD tools, SecureFlag’s new security labs offer a hands-on learning experience that mimics real-world scenarios. Among the first CI/CD systems under scrutiny is Jenkins—a widely used automation server recognized for its adaptability and robustness.

Zooming in on Jenkins Security
The appropriate adoption of security best practices in Jenkins build systems is essential for ensuring that the software development process is as secure as possible. Adhering to such practices that have emerged from many years of lessons learnt helps protect the code, infrastructure, and even the entire software delivery process. So, without further ado, let’s have a look at the main risks a Jenkins CI/CD system can introduce, and how they should be properly handled.
Overexposed Jenkins
A Jenkins instance on the public internet can easily become an attacker’s playground. Malicious actors can pair this setup with deprecated authentication methods, vulnerable plugins, weak username-password combinations… in short, exposed Jenkins instances are a recipe for disaster.
The remediation for this is entirely logical… make sure to host your CI/CD internally! This guarantees that it’s only accessible from within a protected internal network. In instances where developers working remotely require access, mandate the use of a Virtual Private Network (VPN).
Weak Access Control
Utilizing insecure or deprecated authentication can leave your Jenkins instance—and by extension, your entire operation—vulnerable to attacks.
Surprisingly, some Jenkins instances are still deployed with an old and deprecated form of authentication called “Anyone can do anything”. This is the most insecure configuration possible (it’s in the name!), essentially leaving your server’s front door wide open.
To counter this, implement strong authentication and authorization measures by using Matrix-based or Role-based Security. Additionally, move from username and password to a centralized authentication method, such as LDAP or AD-based authentication, to simplify teams management and align with company-wide security policies.
Disclosed Credentials
Given that Jenkins often has access to critical parts of your infrastructure—like code repositories, build servers, and deployment targets—securing authentication material is crucial.
Jenkins is capable of handling credentials, such as API keys and passwords, in a secure and encrypted manner. Always opt for the official method over hardcoding credentials into your build scripts or source code.
Furthermore, use the option to limit the credential’s scope. If a credential is only required for a specific project, don’t make it globally available. Additionally, remember to rotate credentials regularly.
Insecure Build Environments
In many default installations, especially smaller setups, the master often acts as its own agent, executing builds on the same system where Jenkins is installed. Additionally, builds run as the internal SYSTEM user that has full permissions to run on any node.
This is risky because a malicious script or a compromised build could potentially gain unrestricted access to the entire system.
To avoid this, make good use of the Jenkins master-agent architecture that allows you to segregate the building components. Isolate build agents both from the Jenkins master and the production environment, and use access control for builds to avoid using the SYSTEM user. Note that dedicated virtual machines or containerized environments can limit the potential blast radius of a security incident.
Vulnerable and Outdated Components
Before installing any plugin, it’s imperative to thoroughly vet it, check for community reviews, and look into its update history. A poorly maintained or malicious plugin can introduce vulnerabilities into your system, compromising the integrity of your software delivery pipeline.
Keep the Jenkins core and installed plugins up-to-date. Software updates often include patches for known vulnerabilities, so neglecting updates is akin to leaving your doors unlocked.
Poor Monitoring
Jenkins has access to sensitive parts of your infrastructure: source code repositories, build servers, and sometimes even production environments. A security breach in Jenkins could lead to a plethora of problems, including code theft, unauthorized access to servers, and data loss.
Configuring continuous monitoring as an early warning system is paramount to enabling you to handle potential security incidents appropriately. By keeping an eye on the security metrics, you’ll be equipped to respond promptly to security incidents, reducing the potential damage they can cause.
SecureFlag’s new CI/CD Security Labs offer an unmatched opportunity for developers to enhance their skills in securing complex CI/CD systems, such as Jenkins instances.
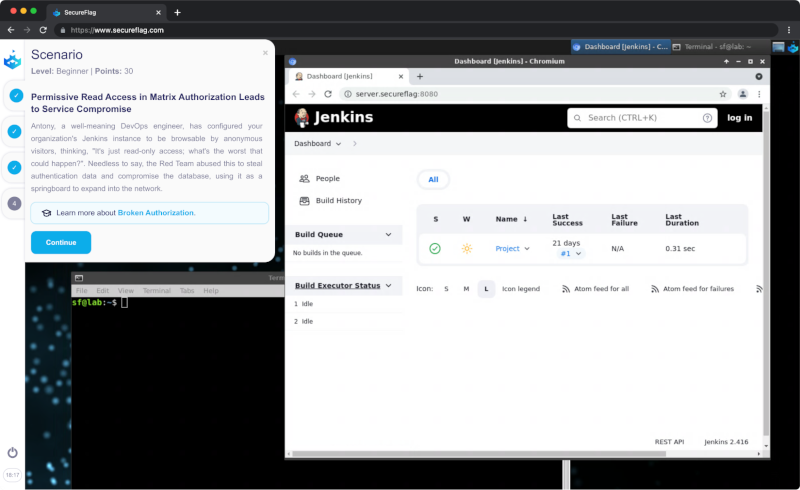
For those looking to sharpen their skills, deepen their understanding of CI/CD security, and learn using the tools they use every day at work, SecureFlag’s CI/CD Security Labs is the definitive choice. It’s not just about learning; it’s about mastering the craft with real-world expertise. Secure your spot in these pioneering labs today, and take your career to the next level.