Securing sensitive data should be a top priority for businesses, especially those that handle credit card transactions. With increasing cyber threats, organizations need to adopt security measures to protect their customers’ payment card data. This is where security threat modeling for the Payment Card Industry Data Security Standard (PCI DSS) comes into play.
By using security threat modeling, businesses can identify potential vulnerabilities and assess the impact of various attacks on their systems. This approach allows organizations to proactively address security loopholes before they are exploited, minimizing the risk of data breaches and ensuring compliance with PCI DSS regulations.

What is PCI DSS?
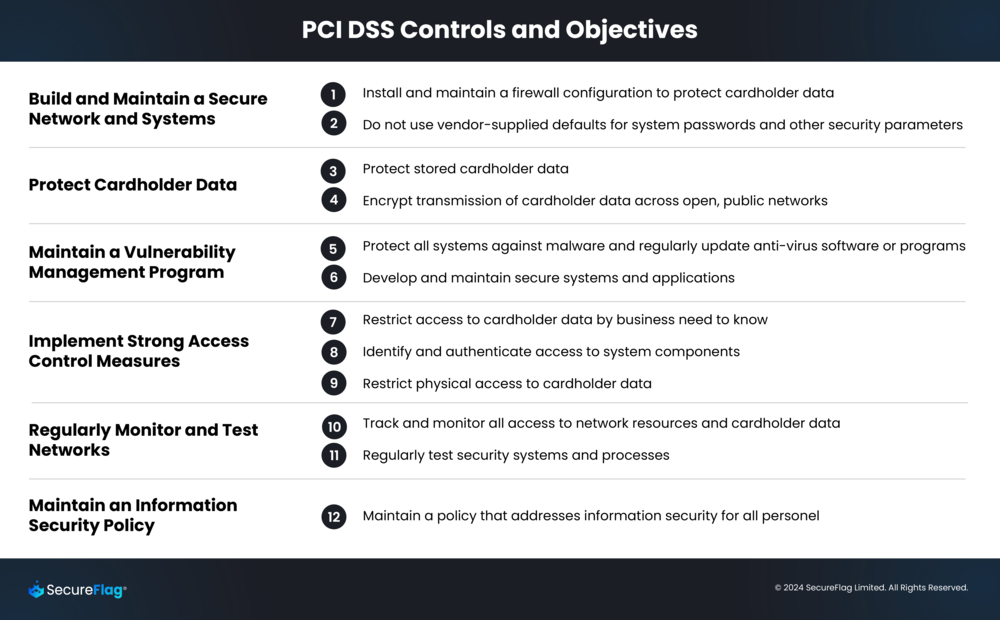
PCI DSS is a standard that sets expectations for merchants dealing with credit card transactions to ensure related data is protected to the highest degree. PCI DSS guidance details what is expected of organizations’ staff and developers, including training developers on secure software design and secure coding techniques and ensuring code is reviewed before release, amongst many other requirements. There are 12 requirements in the PCI DSS, organized under six control objectives:
What is threat modeling?
Threat modeling is a process that helps organizations identify potential risks and vulnerabilities in their systems. It involves analyzing the various components of a system, understanding how they interact, and determining the potential threats that could exploit any weaknesses. In the context of PCI DSS, threat modeling focuses on analyzing the payment card data environment and assessing its potential risks.
Threat modeling aims to proactively identify, assess, and address security vulnerabilities before malicious actors exploit them. By understanding the potential threats and their impacts, organizations can add appropriate security controls to protect their customers’ payment card data.
Importance of threat modeling for PCI DSS Compliance
Compliance with PCI DSS is necessary for businesses that handle credit card transactions. Failure to comply with these regulations can result in severe consequences, including your bank refusing to accept credit card transactions and imposing fines and financial penalties for non-compliance. On top of this, you are more likely to suffer from a data breach if the requirements are not fulfilled, which impacts your organization’s reputation and customer trust.
Conducting a thorough security threat modeling assessment means organizations can identify potential vulnerabilities and risks in their payment card data environment. Allowing them to implement appropriate security controls to mitigate these risks and ensure compliance with PCI DSS requirements. Moreover, security threat modeling helps organizations demonstrate due diligence in protecting their customers’ payment card data, which is essential for maintaining trust and credibility.
Common security threats in PCI DSS environments
From a threat modeling perspective, addressing potential security threats and vulnerabilities is crucial for protecting sensitive payment card information. The PCI DSS requirements are structured to mitigate these risks through a comprehensive approach:
-
Build and Maintain a Secure Network and Systems: Requirements 1 and 2 involve implementing robust network security controls and configuring all system components.
Threats regarding this requirement range from missing network security controls to insecure software configuration.
-
Protect Account Data: Requirements 3 and 4 include protecting stored account data and using strong cryptography.
Common threats that these requirements address are interception of data transmission, insufficient data-at-rest encryption, and use of weak encryption algorithms.
-
Maintain a Vulnerability Management Program: Requirements 5 and 6 mandate up-to-date security measures and the adoption of secure software development techniques.
Section 6.2.4 specifically addresses security development techniques to prevent or mitigate common software attacks, including but not limited to:
- Injection flaws, such as SQL and LDAP injections
- Attacks on data structures, such as buffer-overflow vulnerabilities
- Attacks against cryptography usage
- Attacks on business logic, which includes XSS and CSRF attacks
- Authentication and authorization vulnerabilities
- Other vulnerabilities are identified in the vulnerability management process.
-
Implement Strong Access Control Measures: Requirements 7, 8, and 9 are about restricting access based on the need to know, authenticating user access, and controlling physical access.
These sections focus on the many threats affecting regulated environments’ authentication and authorization mechanisms.
-
Regularly Monitor and Test Networks: Requirements 10 and 11 address monitoring and logging of access, along with regular security testing.
These requirements address common issues such as insufficient logging and missing security testing processes in the SDLC.
-
Maintain an Information Security Policy: Requirement 12 establishes the need for a robust information security policy.
This section focus on missing policy threats, such as lack of security training and risk analysis processes.
Conducting a Security Threat Modeling Assessment for PCI DSS
A security threat modeling assessment for PCI DSS involves several key steps. These steps help organizations identify potential threats, assess vulnerabilities, and implement appropriate security controls to protect payment card data.
-
Identifying assets
The first step in security threat modeling is indentifying assets such as systems, networks, applications, and processes involved in handling payment card data. -
Identifying security threats
Once the assets are identified, the next step is to analyze potential threats in the systems and processes that may be exploited to degrade the security of the card process environment. It also includes assessing the potential impacts of these threats based on the confidentiality, integrity, and availability of payment card data. -
Identifying Security Controls
After identifying threats and potential impacts, organizations need to investigate appropriate security controls to mitigate these threats. This includes technical controls like firewalls, intrusion detection systems, and encryption mechanisms. It also involves using administrative controls, such as access control policies, auditing capabilities, employee training programs, and incident response plans.
Tools and resources for security threat modeling in PCI DSS
Several tools and resources are available to assist organizations in conducting security threat modeling for PCI DSS. These tools provide guidance, frameworks, and templates to streamline the process and give your organization comprehensive coverage.
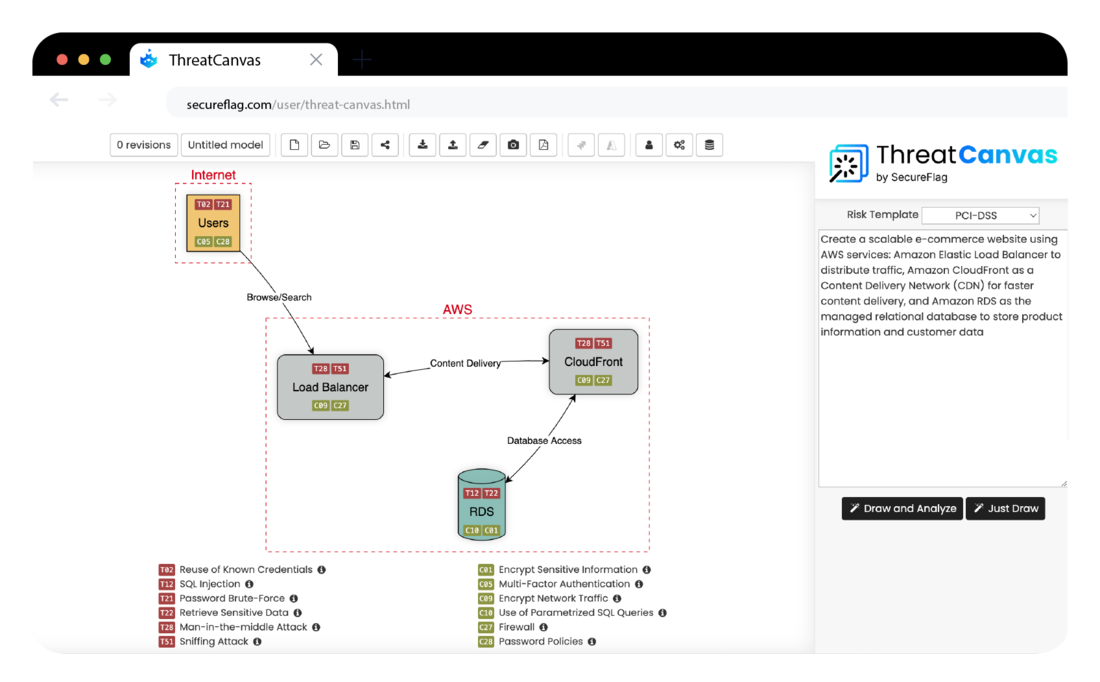
SecureFlag ThreatCanvas: ThreatCanvas is an AI-powered, fully automated tool purpose-built to help organizations create threat models and identify potential risks and vulnerabilities in their systems. It generates Threat Models by taking a textual prompt of a system description or by uploading an Infrastructure as Code template, and identifies threats and their controls based on the context selected. AI is baked into ThreatCanvas to generate reports for translating your built models into digestible and actionable summaries for various levels of stakeholders to understand.
ThreatCanvas provides the options to model Threats to adhere to compliance standards for Payments (PCI-DSS), Health (HIPAA), Privacy (LINDDUN, GDPR), or performing security threat modeling aligning to OWASP Top 10 or STRIDE. With ThreatCanvas, you can also create a custom risk template that aligns directly with your business needs with our Custom Risk Template feature.
PCI Security Standards Council: The PCI Security Standards Council provides resources, guidelines, and best practices for organizations aiming to achieve and maintain PCI DSS compliance.
NIST Cybersecurity Framework: The National Institute of Standards and Technology (NIST) provides a comprehensive framework for improving cybersecurity posture, including threat modeling.
Security threat modeling for PCI DSS is a crucial process that helps organizations identify potential vulnerabilities and risks in their payment card data environment. By proactively analyzing potential threats, assessing vulnerabilities, and implementing appropriate security controls, organizations can minimize the risk of data breaches and ensure compliance with PCI DSS.
Organizations can streamline the process and ensure complete coverage by leveraging tools like ThreatCanvas and resources for security threat modeling in PCI DSS. Investing in security threat modeling is an investment in the security and trust of your customers and the long-term success of your business.
Get in touch with us today to learn more about SecureFlag training and ThreatCanvas!


