Within cybersecurity, nothing stands still for long; organizations are all too familiar with this as they continuously seek to stay ahead of the latest threats. Recognizing this, ThreatCanvas introduced Risk Templates in December, a feature that revolutionized Automated Threat Modeling by enabling the tool to focus its analysis on specific sets of Threats and Controls aligned with compliance models like PCI-DSS, HIPAA, and GDPR. Building on this innovation, ThreatCanvas is now expanding its capabilities to empower organizations further with the introduction of custom Threat Library and Risk Templates.

Custom Threat Library: Tailoring Threats and Controls to Your Organization
Every organization faces unique challenges and threats based on its industry, size, and technological landscape. The new feature of creating custom Threats and Controls within the Threat Library on ThreatCanvas is a game-changer. It allows organizations to incorporate specific threats they are facing and company-wide approved controls that developers should utilize. This customization ensures that the automated analysis performed by ThreatCanvas is not only comprehensive but also highly relevant to each organization’s specific security landscape.
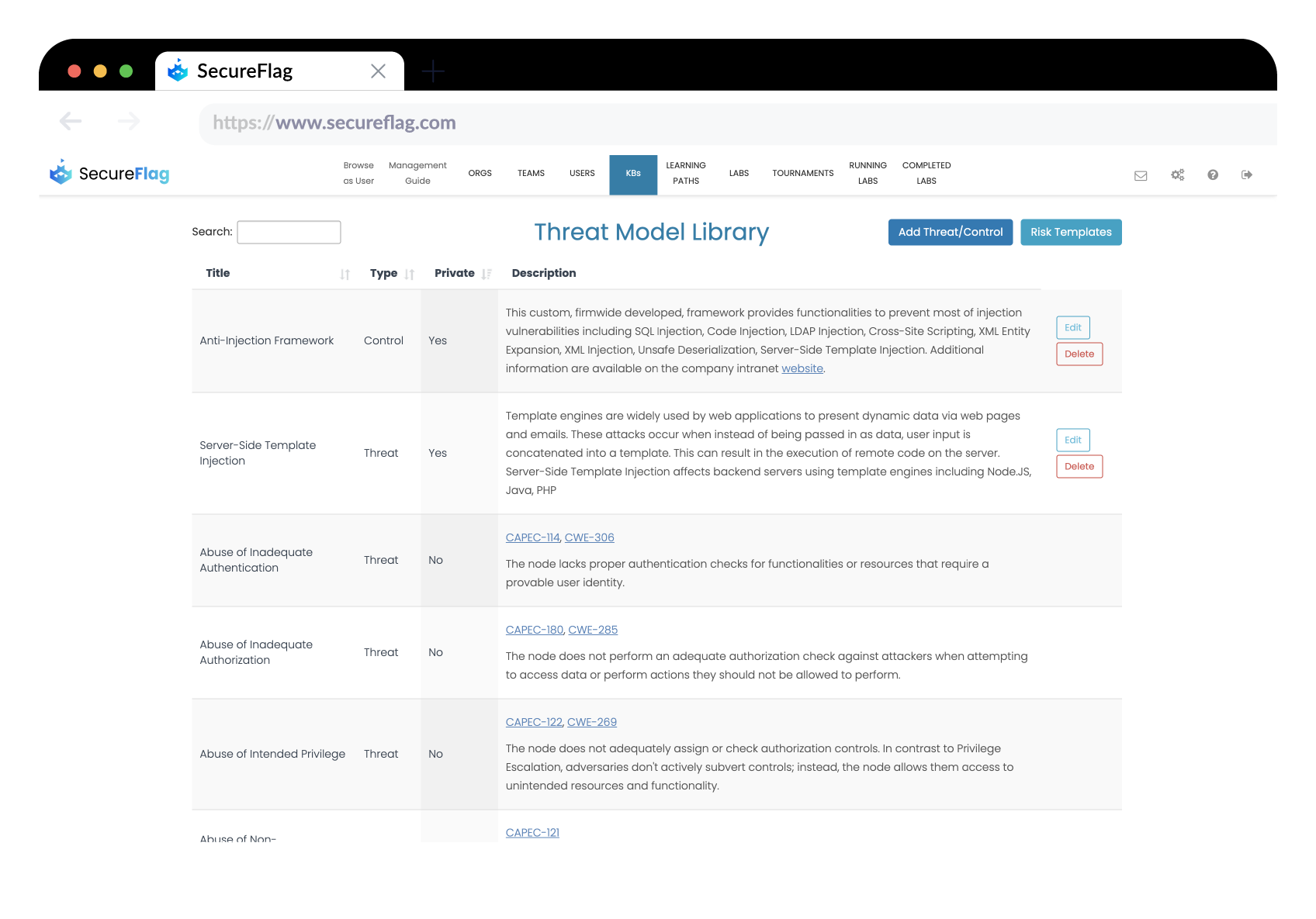
Illustrative Examples of Custom Threats and Controls
- For a VPN provider, the confidentiality of customer IP addresses is paramount. To safeguard this, a custom threat titled “Customer IP Address Disclosure” can be added, paired with a control such as “Perform IP Anonymization.” This ensures that the specific risk of IP disclosure is addressed with an appropriate, company-approved mitigation strategy.
- For a Payment Processor that handles sensitive financial data, the non-disclosure of a card’s Primary Account Numbers (PANs) is crucial. A threat like “PAN Disclosure” could be identified, with a corresponding “Ensure PAN Tokenization” control to mitigate the risk. This custom control ensures that PANs are tokenized, significantly reducing the risk of data breaches.
Crafting Custom Risk Templates: A Focus on Priority
The ability to group Threats and Controls from the Threat Library (including your custom ones) into Custom Risk Templates is another significant enhancement. Risk Templates enable organizations to create tailored risk assessments focusing on the threats and controls most pertinent to their unique requirements or compliance needs. This feature is akin to having a security engineer individually remind developers of critical threats and the approved methods to mitigate them. It ensures that security is not just a checklist but a priority integrated into the development lifecycle.
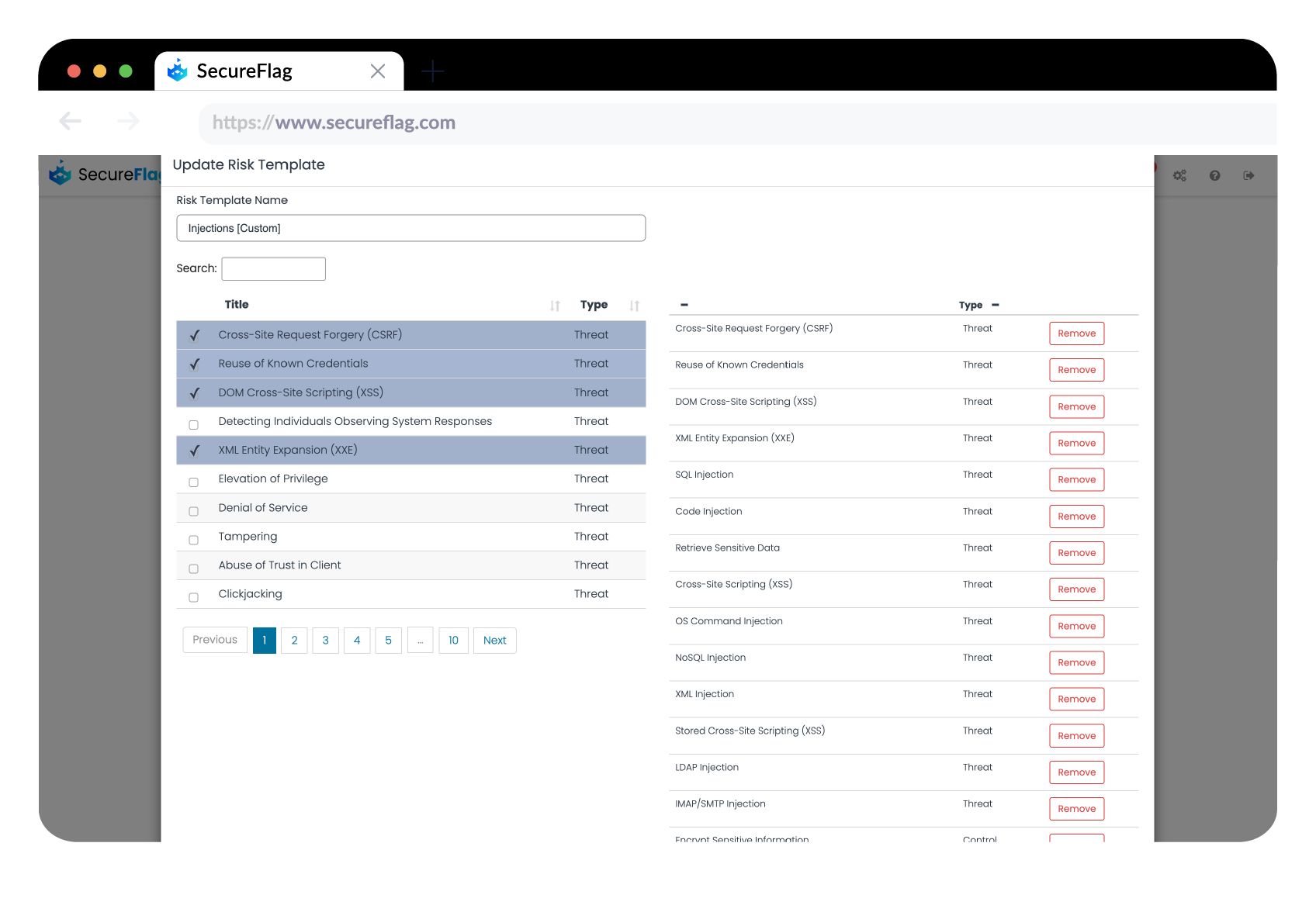
Illustrative Example of Custom Risk Templates
-
VPN Provider: A risk template that combines the security considerations of the OWASP Top 10 with specialized threat/controls relevant to VPN services (example pairs of Threats/Controls: Encryption Failure/Adoption of Secure Protocols, IP Leak/IP Anonymization Techniques, Mandatory Kill Switch) ensuring both broad application security and specific measures for privacy and data integrity.
-
Payment Processor based in EU: A risk template designed to address the dual requirements of securing payment information as per PCI-DSS standards while also ensuring the privacy and protection of customer data in accordance with GDPR guidelines (example pairs of Threats/Controls: Payment Data Breach/PCI-DSS Compliant Payment Processing, Customer Data Violation/GDPR-Compliant Data Processing).
A Bridge Between Security Teams and Developers
By customizing threats, controls, and risk templates to align with an organization’s unique risk profile, developers are presented with tailored recommendations that reflect the specific risk appetite of the organization, its various business lines, or even individual products. This customization facilitates a more nuanced approach to security, enabling the identification of relevant threats and controls directly tied to each application’s risk characteristics. Such a targeted strategy not only enhances the precision of security measures but also ensures comprehensive compliance with all pertinent regulations, fostering a more effective and informed security posture throughout the development process.
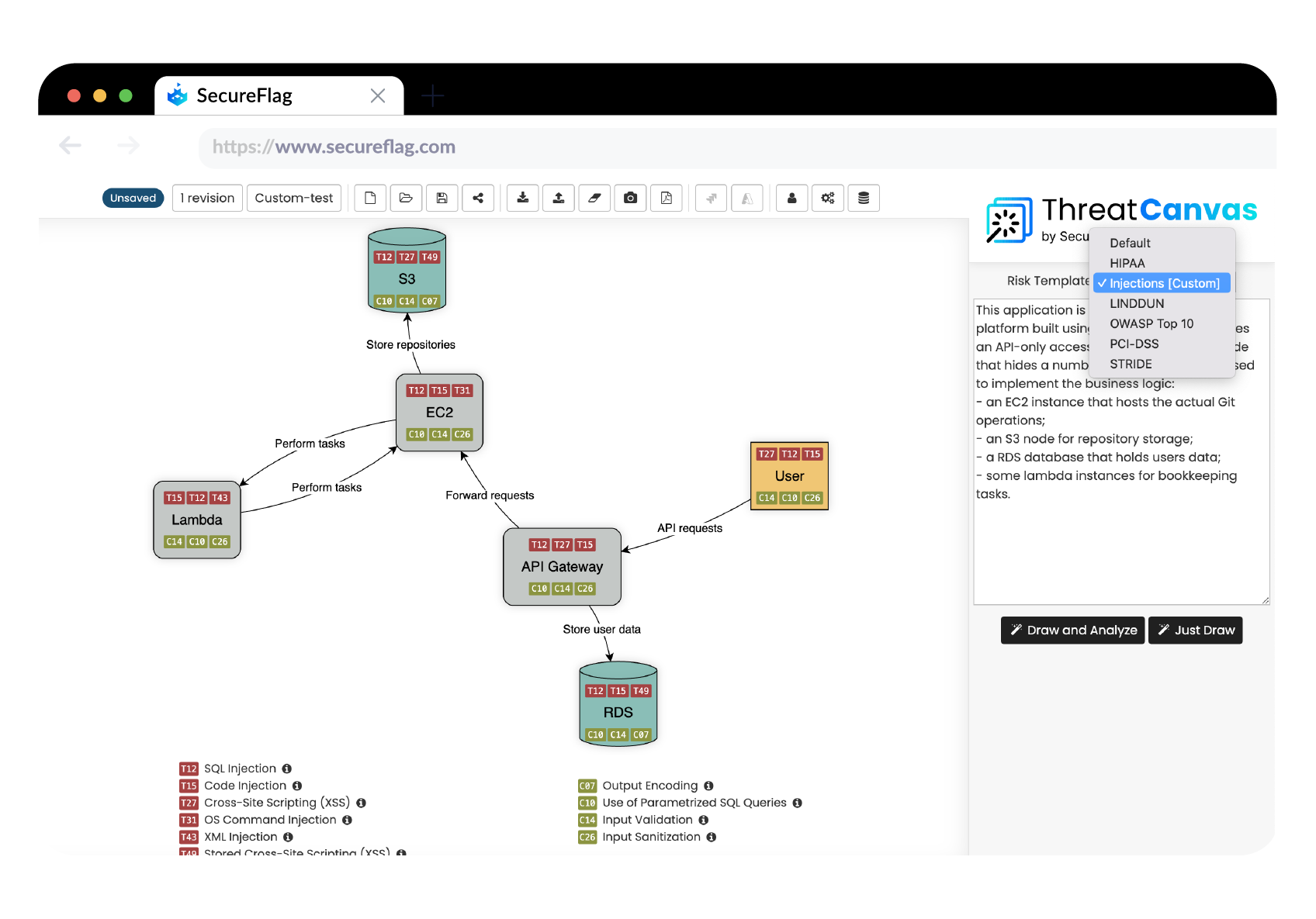
Integrating Automated Threat Modeling into the Software Development Lifecycle
ThreatCanvas’ latest features emphasize the seamless integration of automated threat modeling into the software development lifecycle. By allowing the definition of custom threats and prioritizing them in the analysis, developers are made aware of their importance to the organization. This approach guarantees that ThreatCanvas acts as a strategic ally in scaling security measures, reaching every developer during the design phase. By doing so, we can consistently inform them about the most pressing threats to the organization and guide them toward the most effective strategies for mitigation.
Contact us today to start your journey toward a more secure and collaborative software development environment.