- What is the Concept of Shift Left in Security
- The Evolution of Security Training: From Reactive to Proactive Approaches
- Importance of Security Training in Today’s Digital Landscape
- Building a Security-Conscious Culture
- Realizing Time and Cost Savings: Benefits of Shifting Left Through Training
- Developers are Front and Center for Shifting Left
- Leveraging Real-World Scenarios with SecureFlag: The Effectiveness of Hands-On Training
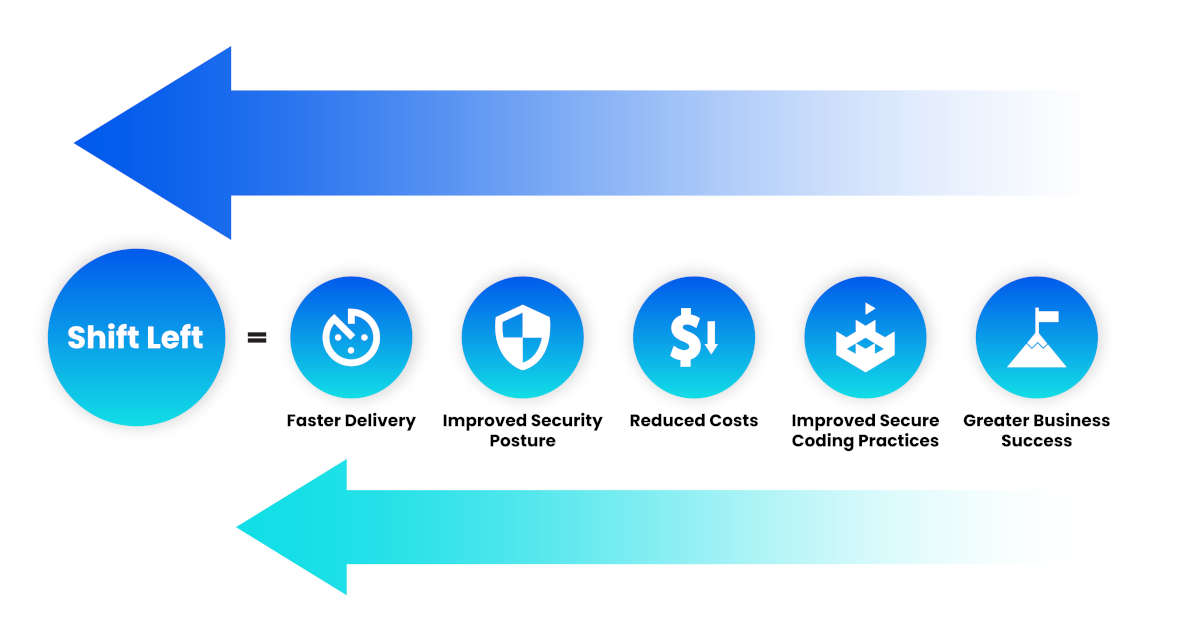
What is the Concept of Shift Left in Security
In the world of software development, Shift Left is a proactive approach to security, as historically, security measures and testing were implemented later in the software development lifecycle (SDLC), often as a last stage of development. However, with the Shift Left method, the focus moves towards integrating security practices earlier in the SDLC; this has the impact of reducing costs and time-to-fix and improving the overall security posture.
In this post, we discuss further what Shift Left entails, why it is crucial, and how effective security training is pivotal in its implementation.
The Evolution of Security Training: From Reactive to Proactive Approaches
Some past approaches to securing the SDLC have been to implement fixes as vulnerabilities are discovered (either before or after deployment) or after a breach has occurred. This approach has been reactive to the consequences of already committed code.
There has been widespread adoption of software that scans and tests your codebases for a range of different areas, such as Software Compositional Analysis (SCA), Static Application Security Testing (SAST), and Dynamic Application Security Testing (DAST) tools into development pipelines, which help look for vulnerabilities in Open Source Software packages and dependencies, scan your code for any detectable security flaws, and run tests on the application for any exploitable weaknesses respectively. The adoption of these tools is a net positive in the overall topic of improving security in software development. Still, these methods and tools come after the code has been committed and integrated, putting teams on the backfoot of having to refactor already written code. Implementing a more proactive approach and encouraging developers to continue training and improving their secure coding knowledge can be addressed earlier in the development process, to the stage when the code is being written.
Importance of Security Training in Today’s Digital Landscape
Training teams in security practices, be they Developers, DevOps, or members of your security team, is only getting more challenging and essential due to the range of different security practices, concepts, and ever-growing list of vulnerabilities.
New CVEs and vulnerabilities are published regularly, where mitigation isn’t always as straightforward as waiting for the vendor to release a security patch and updating the dependency version. Likewise, scripts that can be used by hostile actors are more common and easily obtainable by anyone with an internet connection and slight technical know-how, meaning that if your product has a known weakness with the potential to be exploited, it likely is a matter of when this will be exploited rather than if.
Raising your team’s awareness of relevant topics in ways that engage them is crucial to driving home the information to carry forward. By making sure your team is well-versed in the best practices, you can ensure that released products are well-prepared to handle the ongoing stream of vulnerabilities that appear each day or that, at the very least, your teams are well-positioned to deal with any undetected vulnerabilities as they become known.
Building a Security-Conscious Culture
When looking at security practices and implementing new policies to adopt into the pipelines or checks afterward, it is always about flagging issues that have appeared. Either through code review or perhaps an alert that has popped up from one of the many different scanning tools used - but what if we used this opportunity to, instead of just fumbling through remediation, implement a method of learning and training on the particular issue so that the problem is avoided altogether in the future.
So, how would this look in practice?
It’s almost guaranteed that if you mention training to someone, the first idea that comes to mind is sitting down and watching a 20-minute video exercise with a short test at the end, and failing this test might mean you have to retake the test again and perhaps have to rewatch the content too. With this in mind, it’s no surprise that the perceptions of training don’t stir excitement in the average person.
Training doesn’t have to be boring; by introducing engaging, interactive, and informative material that is directly relevant and applicable to the topics being seen by developers, you can create a culture of “looking for training” rather than turning away from it. Training that engages developers and team members should be interactive and relevant to be immediately useful to whatever project is being worked on; it should be implemented in such a fashion to be actionable and scalable for development teams.
This might include:
- Leading by example, as managers and project leads, you should participate and demonstrate the benefits of continuous training to the rest of the team.
- Encouraging members of teams to specialize in a particular topic to become the security champion whom others can call upon for help.
- Integrate training into issue tracker boards and pipelines to embed training in routine everyday tasks so it reinforces the idea of integrated learning.
- Implementing gamification into your training by introducing leaderboards and friendly competition and encouraging pride in work.
Realizing Time and Cost Savings: Benefits of Shifting Left Through Training
It’s well-known that it becomes more expensive, in multiple ways, to address a vulnerability further along in the SDLC it is discovered. Remediating a vulnerability later in development means that an entire system may already be developed, and the underlying code is more complex, taking more time, design, and implementation to navigate around. Using tools such as SCA, SAST, and DAST can help identify these issues earlier.
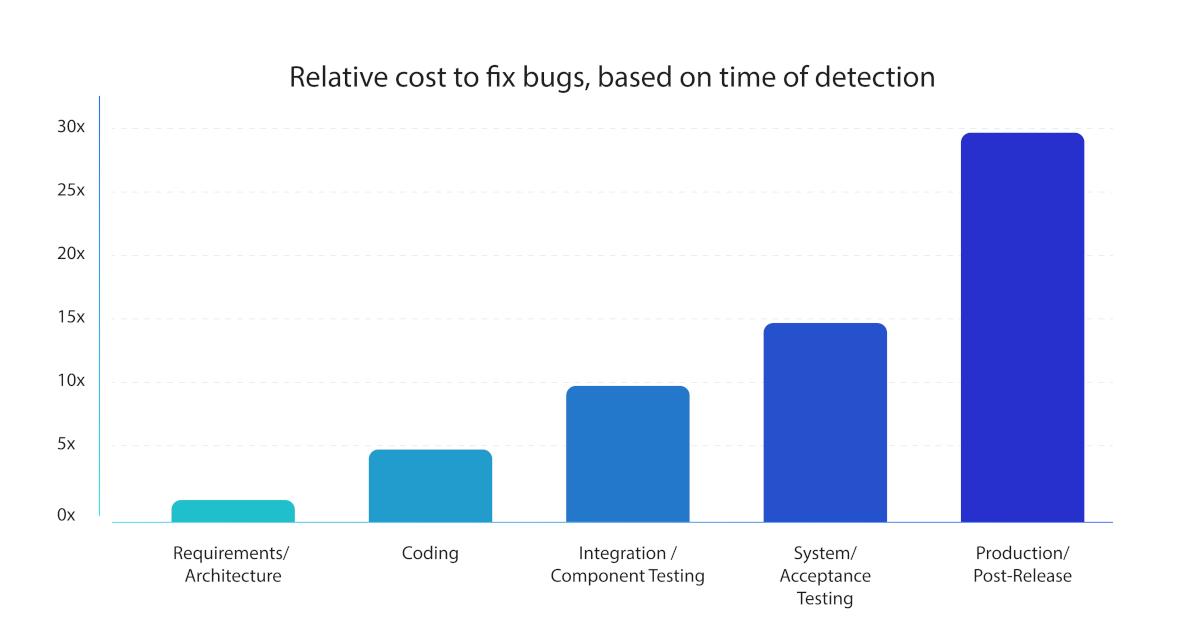
For an idea of what kind of savings can be made in real terms, IBM’s “Cost of a Data Breach” report put the average data breach cost at $4.45 million. The average cost difference between breaches that took more than 200 days to find and resolve and those that took less than 200 days was $1.02 million. Having your developers trained in remediating vulnerabilities and applying security fixes could be the difference between this quoted average of $1.02 million.
By encouraging effective training before any potential issues arise, you save time and money. Time is saved because your developers are already equipped to resolve the problem, and money is saved because, as mentioned above, the longer it takes to resolve either a breach or a discovered vulnerability further in the SDLC, the more intricate and costly it becomes.
Developers are Front and Center for Shifting Left
The idea of shifting left is often thought of in conjunction with Dev-Ops teams to implement changes. So, introducing the concept to the earlier stages of the development process might sound like extra work being hefted onto developers. While an understandable assumption, it isn’t entirely correct; shifting left will benefit developers in the long run by ensuring that vulnerable code is not introduced to the development environments, meaning that it won’t affect systems after they have already been deployed to production. Ensuring that your organization has the correct tools for developers is a big point towards this.
A large number of organizations have shifted their development methods to agile practices which usually encourages sprints and a more fast paced development cycle. This means there are a lot of opportunities for vulnerabilities to be introduced to software which is at risk of being missed by testers, code reviewers and devsecops teams.
Leveraging Real-World Scenarios with SecureFlag: The Effectiveness of Hands-On Training
So where does SecureFlag fit in with Shift Left? Well as mentioned thoughout this post, implementing a practical and useful method of training is core to how we see Shift Left. Improving standards of coding by emulating production environments and programming languages that teams are familiar with.
SecureFlag’s Platform allows access to a whole range of different interactive labs to gain insight into how to remediate security vulnerabilities across a wide variety of technologies, including Java, C++, Infrastructure as Code templates, Docker, generative AI, and many more.
Using 100% hands-on labs means that training can be assigned to team members based on the programming languages and technologies being used in your projects. This allows developers to become familiar with implementing security fixes in a virtualized environment that reflects real-world scenarios.
Our Platform can integrate with existing CI/CD tools like Jira, Azure Boards, GitLab, and GitHub to deliver targeted training for identified issues. Hence, training is relevant and immediately applicable for upskilling and improving your developers’ technical skills.
Implementing Shift Left is already a well-known idea in development teams, but continuous training can often be overlooked as a way to drive better quality and more secure code. As well as a tool to help make remediation and disaster handling more efficient and less costly. Consider improving or expanding your training offerings to your team; contact our team at SecureFlag for more information on how our Platform can help!