For organizations, protecting payment card data is a top priority. With new Payment Card Industry Data Security Standard (PCI DSS) requirements, there are a variety of new controls and approaches to security. It is therefore vital that your organization is PCI DSS compliant.
With cyber threats growing in sophistication, organizations need to ensure they have processes in place to grow with them. We previously wrote an article on how threat modeling can help achieve PCI DSS compliance, but with version 4.0, what’s changed?

What is PCI DSS?
Introduced by the Payment Card Industry Security Standards Council, the Payment Card Industry Data Security Standard (PCI DSS) has long been the cornerstone for anything related to payment security, such as cardholder information, credit cards, and anything else involved in the cardholder data environment (CDE). With the introduction of PCI DSS 4.0, the standard has been expanded to better address the complexities of modern cybersecurity and payment processing environments.
Released in March 2022, PCI DSS 4.0 is the first major update to the standard since 2018’s version 3.2.1 and provides organizations with more flexibility, encourages a continuous approach to security, and focuses on risk-based decision-making.
PCI DSS requirements apply to everything within the CDE. This includes system components and people storing, processing, or transmitting cardholder data and sensitive authentication data. The scope also extends to any connected systems that could impact the security of the CDE.
If something could affect the security of cardholder data, it falls within the scope of PCI DSS.
How have PCI DSS requirements changed
Compared to version 3.2.1, PCI DSS 4.0 introduces several key updates to enhance organizations’ overall security posture. These changes are part of a broader shift toward continuous security practices emphasizing the importance of adapting to the continuously evolving threat landscape.
PCI DSS Requirements for Your Organization
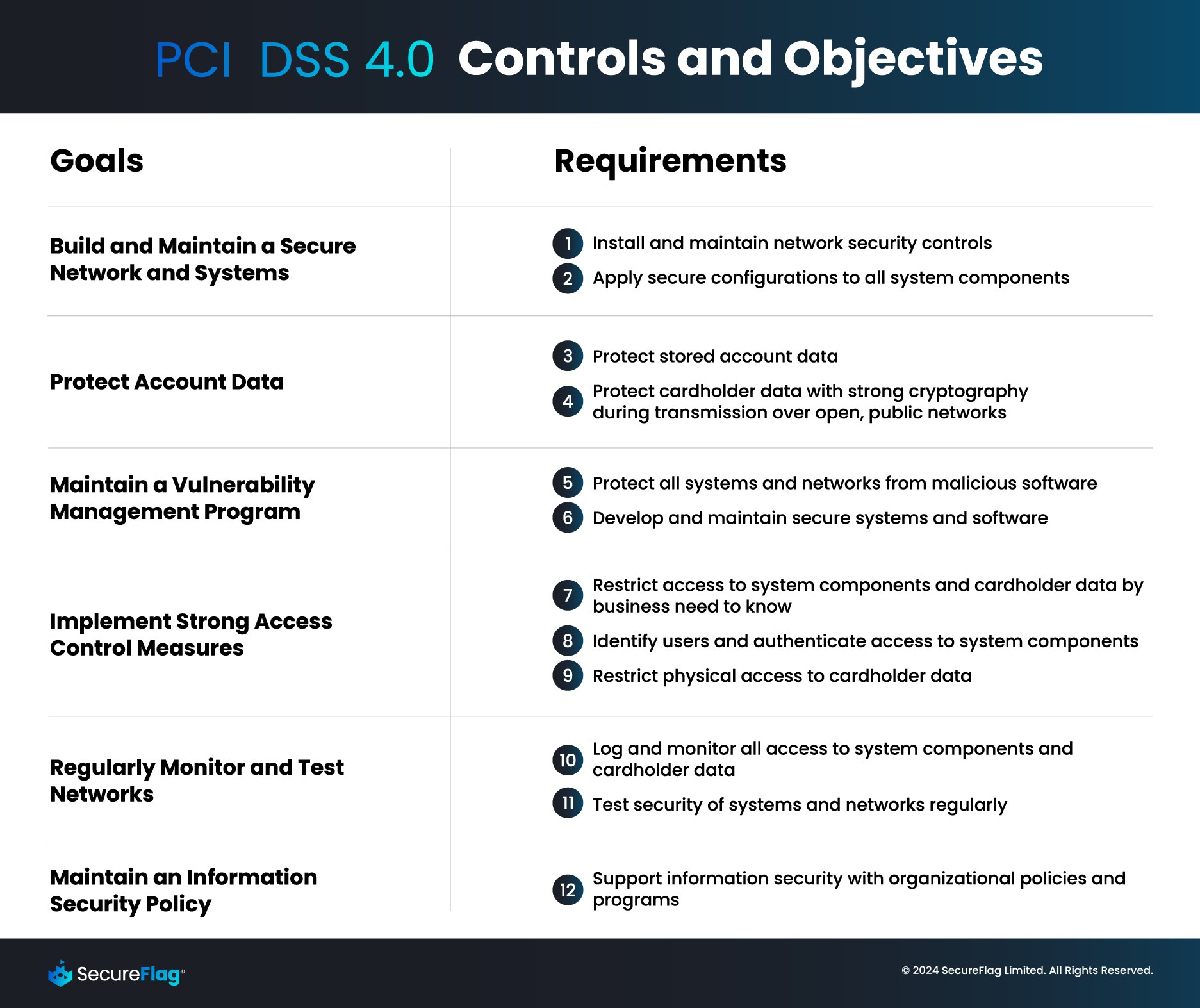
Increased flexibility through customized approaches
One of the biggest changes in PCI DSS 4.0 is the introduction of the “Customized Approach” for meeting security requirements.
Previously, the standard provided controls that organizations had to implement exactly as outlined. While this approach ensures that the same level of security is maintained across the industry, it poses challenges for organizations with more unique or complex environments.
With PCI DSS 4.0, organizations can design and implement controls that meet the intent of the requirements in ways that best suit their specific needs. This increased flexibility allows organizations to innovate and optimize their security measures without being constrained by one-size-fits-all methods.
However, this also places greater responsibility on organizations to ensure that their customized controls are effective and take the extra steps to prove their controls are suitable.
Security as a continuous process
At SecureFlag, we have always maintained that security is an ongoing task, requiring secure code training and regular security involvement from all teams associated with the software development life cycle.
With PCI DSS 4.0, this is emphasized by including promoting security as a continuous process. This is to encourage organizations to move beyond annual assessments to a state of continuous compliance and monitoring.
This change in approach is crucial because the cyber threat landscape is ever-changing. New vulnerabilities and attack vectors emerge regularly; what was secure yesterday might not be secure today.
By embedding security into daily operations and integrating tools, organizations can detect and respond to threats more quickly, which reduces the risk of data breaches and other security incidents.
Stronger authentication requirements
PCI DSS 4.0 introduces more stringent authentication requirements with methods like Multi-factor authentication (MFA). MFA is now mandatory for all access to the CDEs, extending beyond just administrative access.
The reason for this change is that compromised credentials are one of the most common methods used by attackers to gain unauthorized access to systems. By requiring MFA, PCI DSS 4.0 helps ensure that even if credentials are stolen, additional authentication factors will still protect the CDE.
Enhanced vulnerability management
Recognizing that not all threats are created equal, PCI DSS 4.0 encourages organizations to adopt risk-based approaches to security. This means prioritizing resources and efforts based on the most significant risks to the organization and its cardholder data. However, PCI DSS does now mention that procedures and a regular update schedule should be in place to address low-risk issues, too, with a plan to address them within a reasonable timeframe.
The standard also includes updated requirements to address new and emerging threats. For example, PCI DSS 4.0 requires enhanced logging and monitoring capabilities, where critical system logs should be maintained for at least 12 months and have three months readily available for immediate analysis.
Furthermore, the standard places a greater emphasis on encryption and key management, mandating strong cryptographic protocols and stringent key management practices to protect sensitive data. Organizations are encouraged to adopt a risk-based approach, continuously adapting their encryption and monitoring strategies to counter evolving threats.
The role of Secure Code Training in PCI DSS Compliance
As organizations adapt to the requirements of PCI DSS 4.0, it’s important to recognize that technical controls alone are not enough. A strong security posture depends on the people behind the technology—developers, engineers, and everyone else involved in the SDLC who design, build, and maintain the systems.
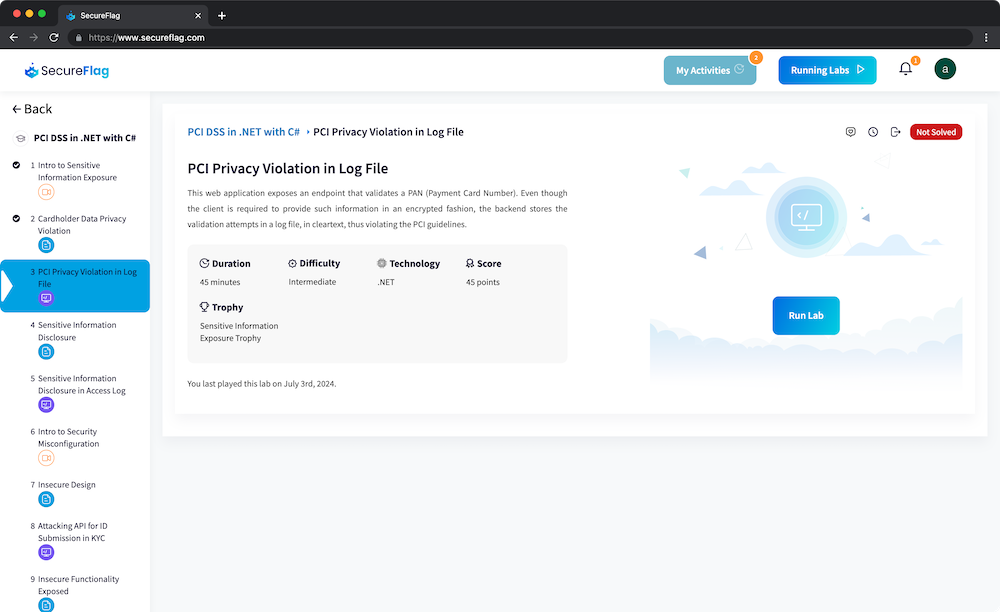
Secure code training plays a critical role in this equation, particularly when it comes to establishing security as a continuous process. Developers are at the frontline of security, writing the code that powers payment applications and systems. If they are not equipped with the knowledge and skills to write secure code, then it’s a matter of time before flaws and gaps start to appear.
1. Embedding Security in the Development Lifecycle
Implementing a secure code training plan ensures that developers understand the security implications of their work and are equipped to incorporate security best practices throughout the SDLC. This means identifying and addressing potential vulnerabilities early in the development process or even preventing insecure code from being written rather than waiting for them to be discovered in production.
Processes for this might include providing contextual information on identified security issues in project management software, allowing for immediate triage and remediations. Or embedding relevant training into developer tasks as needed. This proactive approach aligns with PCI DSS 4.0’s emphasis on continuous security, as it helps to create secure applications from the ground up.
2. Adapting to a Dynamic Threat Landscape
Secure code training equips developers with the skills to stay ahead of threats by understanding current trends and adapting their coding practices accordingly.
For example, training might focus on the latest secure coding practices for managing encryption keys, handling user authentication, or mitigating common web application vulnerabilities like SQL injection and cross-site scripting (XSS). As these threats evolve, so too should the training that developers receive.
3. Creating a Culture of Security
Beyond technical skills, secure code training fosters a culture of security within the organization. When developers are trained to think about security as a fundamental part of their job, they become more vigilant and proactive in identifying and addressing potential security issues. This cultural shift helps achieve the continuous security model promoted by PCI DSS 4.0 and makes sure it is maintainable in the long run. When everyone in the organization—from developers to executives—prioritizes security, the likelihood of a successful attack decreases, and the organization’s overall security posture improves.
Achieve PCI DSS compliance with SecureFlag and ThreatCanvas
For organizations seeking to meet the requirements of PCI DSS 4.0, SecureFlag can help ensure that your development teams are fully prepared to meet the challenges of continuous security.
Using the SecureFlag Platform, developers can access a range of virtual labs and Learning Paths specifically tailored to meeting PCI DSS requirements, empowering your developers with the skills they need to write secure code and protect sensitive payment card data.
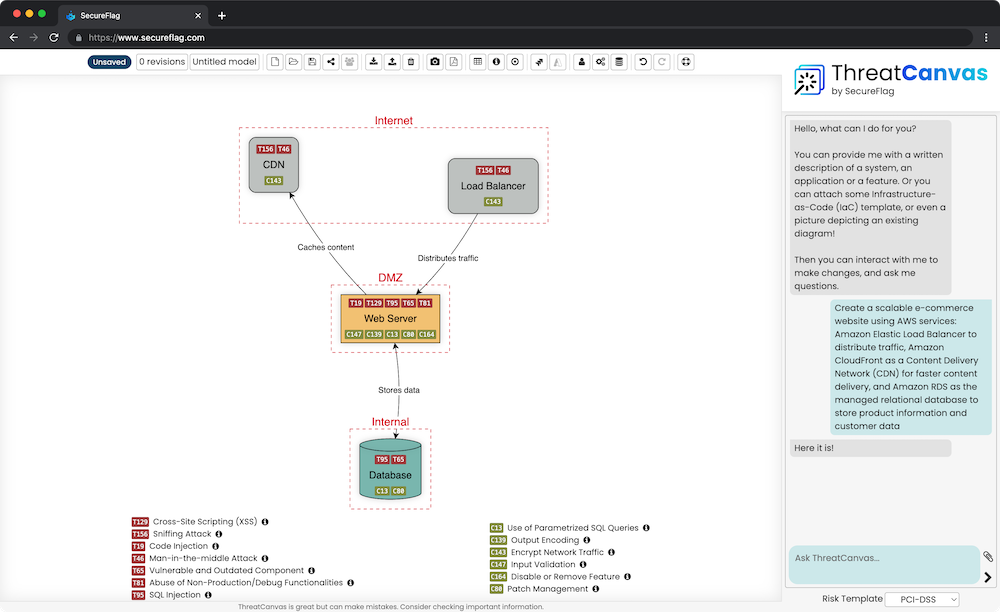
Additionally, SecureFlag’s ThreatCanvas enables teams across organizations to scale threat modeling. What is usually an activity restricted to security experts can now be used by developers to help identify and mitigate security risks early in the development process.
By integrating threat modeling into your SDLC, you can ensure that your applications are secure by design, aligning with the continuous security approach promoted by PCI DSS 4.0. Don’t wait—visit SecureFlag today to learn more about how our solutions can help you achieve PCI DSS 4.0 compliance and strengthen your organization’s security posture.
Get in touch with the SecureFlag team today to learn more about how secure coding training and threat modeling with ThreatCanvas can help prepare your organization for PCI DSS 4.0!