For many organizations, meeting compliance can be a daunting task, as overlapping regulations can consume valuable time across multiple teams.
So, how do organizations manage a list of regulations? For many, the answer comes in the form of a Governance, Risk, and Compliance (GRC) framework.
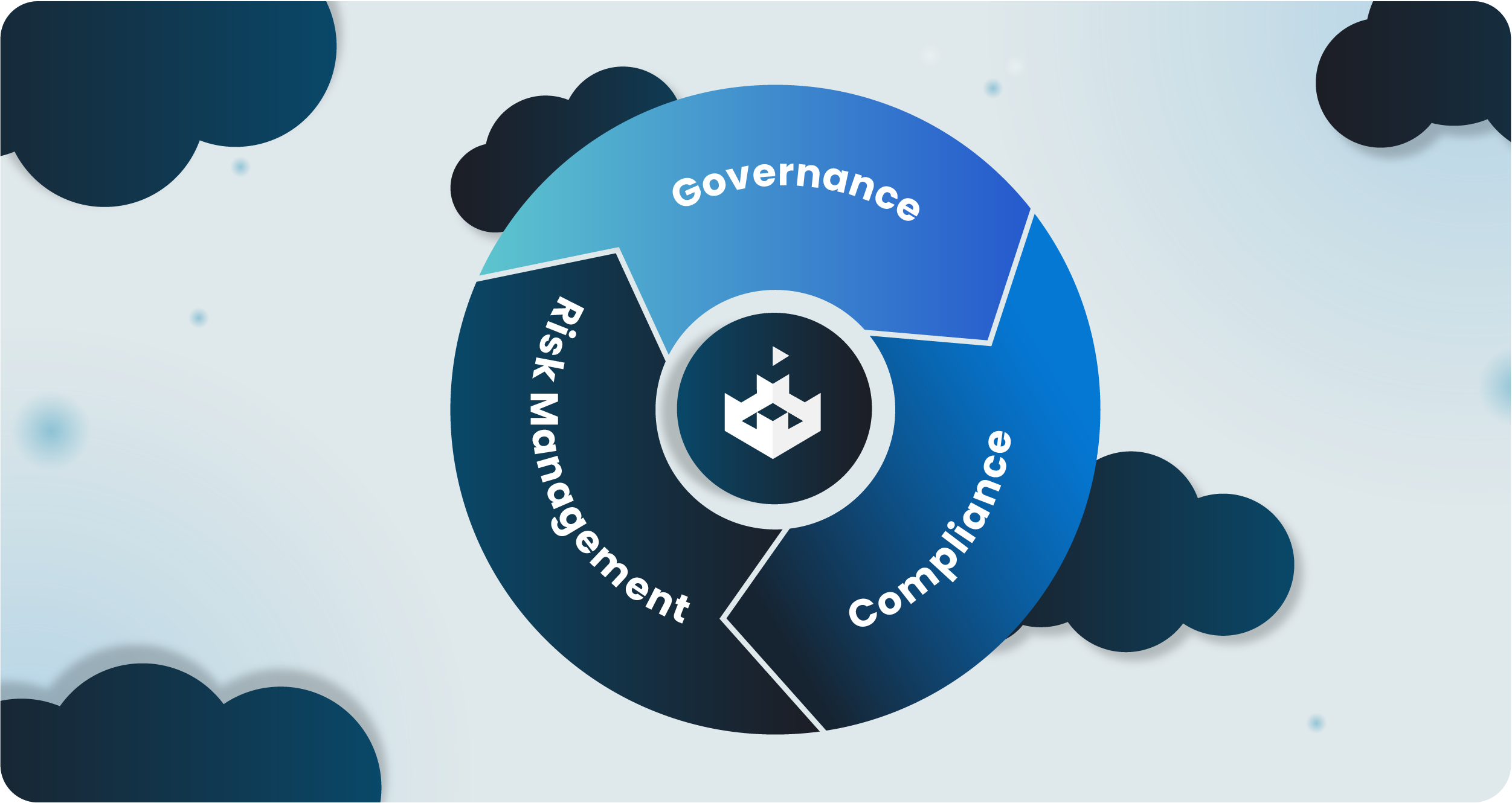
What is GRC?
GRC is a framework that ensures an organization’s operations are aligned with its business objectives while managing risks and adhering to legal and regulatory requirements. At its core, GRC serves to streamline the interconnected areas of governance, risk management, and compliance.
GRC in cybersecurity
GRC connects these three pillars in its approach to risk and compliance management, reducing redundancies, improving efficiency, completing risk assessments, and ensuring that the risks are proactively addressed. For a Chief Information Security Officer (CISO), a strong GRC program provides the structure to manage the complex landscape of cybersecurity and regulatory demands.
Governance
With Governance, it’s all about setting up the right policies, processes, and controls to help achieve the organization’s goals while ensuring accountability. Within cybersecurity, this means creating, and upholding security protocols that protect and align with the business strategy.
Risk Management
Identifying, assessing, and mitigating potential threats are all parts that make up effective risk management. Since this can disrupt your organization’s success and work. This includes everything from cyber risks and data breaches to vulnerabilities that leave you exposed.
Compliance
Compliance means peace of mind for organizations. This ensures all of the legal and regulatory frameworks are being followed. Whether it’s PCI DSS, ISO 27001, HIPAA, GDPR, or any number of other regulations, staying compliant means building trust with customers and keeping up a reputation of a pragmatic cybersecurity program.
The evolving role of the CISO
The general role of the CISO has transformed in recent years. No longer limited to just the organization’s security, the modern CISO is responsible for aligning security initiatives with broader business goals. This shift is driven by the digital transformation many organizations have undergone and are undergoing, as well as the growing complexity of cyber threats.
Today’s CISO must have a deep understanding of the company’s risk appetite and balance that against emerging threats. What this means is they must collaborate with other departments to ensure that security is integrated into all aspects of the organization, from development to operations.
Perhaps most importantly, the CISO is also tasked with navigating the ever-expanding web of regulatory requirements. Whether it’s data privacy regulations or industry-specific standards, maintaining compliance is a critical part of the CISO’s job. This is where a robust GRC program becomes invaluable, offering a structured way to manage these complex and overlapping demands.
What is GRC in cybersecurity?
Traditionally, cybersecurity policies and GRC were treated as separate frameworks—security teams focused on technical defenses while compliance teams dealt with audits and regulations. However, these days, it’s becoming more clear that these areas need to work together.
By integrating cybersecurity efforts with GRC frameworks, organizations gain a more complete view of their risks, allowing CISOs to shift from reactive defense to proactive risk management, so that security controls are both effective and aligned with the company’s broader risk strategy.
For example, threat modeling can be incorporated into GRC programs to identify potential security risks early in the development cycle. Similarly, secure coding practices can be tied to compliance requirements, ensuring that new software is both secure and adheres to relevant regulations from the outset.
This integrated approach allows organizations to reduce risk more effectively, while also simplifying the process of maintaining compliance across multiple frameworks.
The benefits of GRC for CISOs
For CISOs, integrating GRC with cybersecurity offers significant advantages. One of the primary benefits is increased visibility into the organization’s risk landscape. A unified GRC program provides a comprehensive view of where vulnerabilities lie, how severe the risks are, and what actions are being taken to address them. This allows for more informed decision-making and resource allocation.
The ability to clearly report on the organization’s security posture is another major advantage. Instead of focusing on metrics like the number of patches applied or attacks blocked, a GRC-driven approach allows CISOs to demonstrate how these efforts are reducing business risks and contributing to overall security and compliance goals.
Enterprise-wide alignment: The CISO’s key role
Achieving enterprise-wide alignment around security and compliance is one of the more challenging aspects of the CISO’s role. From the C-suite to frontline employees, everyone plays a role in protecting the organization’s assets.
By working closely with other key departments—such as HR, legal, and engineering—CISOs can ensure that security policies are integrated into every aspect of the business. This requires clear communication and often, a shift in culture where security is seen not as a barrier but as a critical business enabler.
Employee training is a fundamental part of this alignment. By equipping staff with the knowledge they need to identify risks and follow best practices—whether it’s avoiding phishing emails or writing secure code—CISOs can significantly reduce the risk of human error, which remains one of the largest contributors to cyber incidents.
Streamlined compliance management
Managing compliance across multiple frameworks can be a daunting task, especially as regulations continue to evolve. Each framework comes with its own set of requirements, and it’s easy to get bogged down in the details. However, a strong GRC program helps simplify this process.
By implementing a core set of controls that can be mapped to multiple frameworks, organizations can reduce the administrative burden associated with compliance. For instance, a single control for access management might simultaneously satisfy the requirements for PCI DSS, HIPAA, and ISO 27001, allowing the organization to maintain compliance without duplicating efforts. Saving time and resources and ensuring a more cohesive security strategy across different regulatory environments.
Automation also plays a key role in streamlining compliance. GRC platforms that offer real-time visibility into compliance status can alert the CISO to potential gaps or issues, enabling the team to address them before they become full-blown problems.
Improving cybersecurity posture through GRC
Ultimately, the goal of GRC is to strengthen the organization’s overall security posture. By proactively identifying and managing risks, companies can minimize the likelihood of incidents and reduce the impact of those that do occur. This means not only faster response times and fewer breaches but also a stronger overall defense against evolving threats.
Secure coding practices are a critical part of this improved posture. When developers are trained to write secure code from the outset, vulnerabilities are less likely to make it into production, reducing the risk of exploitation. GRC programs that emphasize secure development practices help ensure that security is embedded into the software development lifecycle, lowering overall risk.
How SecureFlag and ThreatCanvas fit in
This is where SecureFlag and ThreatCanvas come into play. SecureFlag’s secure coding training equips developers with the knowledge and skills they need to write secure code, reducing vulnerabilities early in the development process. By focusing on hands-on training, SecureFlag ensures that developers can spot and prevent common security issues, making your software more resilient.
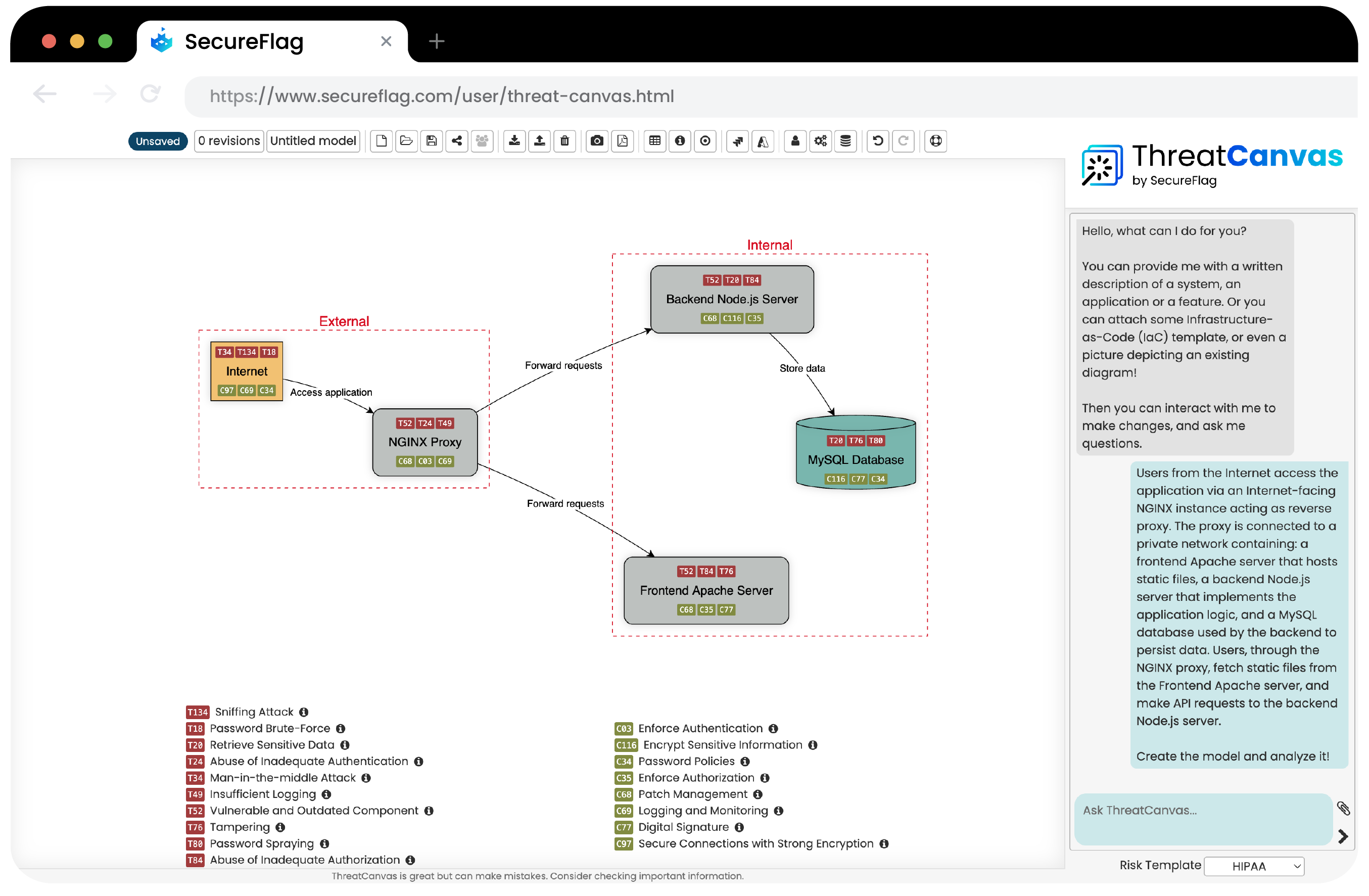
ThreatCanvas complements this by mapping security threats and their corresponding controls within contexts such as HIPAA and PCI DSS, helping CISOs ensure that their security efforts are aligned with compliance needs. Together, these tools provide a comprehensive approach to managing risk and compliance in a streamlined, efficient manner.
The bottom line: Secure your future
Security can no longer be treated as an afterthought. By integrating GRC, secure coding practices, and threat modeling into a unified strategy, CISOs can build a more secure, resilient, and compliant organization.
Ready to take the next step? Reach out to SecureFlag to discover how we can help you secure your future with confidence.


