If you’ve ever worked on traditional threat models, you’ve probably experienced firsthand how hard it can be to keep them useful and consistent across different teams. One of the reasons is that they are so large and hard to scale, they become problematic. SecureFlag’s ThreatCanvas takes a different approach.
Built around the lightweight, developer-friendly RaD-TM methodology, it keeps security practical and scalable. And now, we have a new feature to add to that—Linked Threat Models! Teams can break down large, complex systems into smaller, connected models, which makes collaboration, visibility, and consistency in threat modeling much simpler.

How Linked Threat Models Make a Difference
Security teams and developers often find it challenging to keep threat models actionable and relevant, especially in complex systems. Traditional approaches tend to create massive, one-size-fits-all models that don’t capture the details needed for effective risk management.
Linked Threat Models in ThreatCanvas solve this by letting teams:
-
Break Down Large Models: Instead of trying to map out an entire system in a single, overwhelming model, teams can link smaller, more focused threat models to different components or features.
-
Improve Collaboration: Security teams can outline the high-level system threat model, while development teams take ownership of specific security-critical components.
-
Ensure Standardization: Linking models makes it easier for organizations to apply a structured and consistent approach to threat modeling across teams and projects.
-
Simplify Compliance: Compliance-driven models often feel too broad and impractical. Linked Threat Models, on the other hand, give teams a much broader view of compliance while connecting it to detailed, security-focused models.
How It Works
By using Linked Threat Models, teams can:
-
Create a system-level threat model to get an overview of the entire application or infrastructure.
-
Identify security-critical components, focusing on the areas that need a closer look.
-
Generate component-level threat models so teams can create specific models for the parts they’re responsible for.
-
Link threat models to keep everything connected, ensuring traceability and a full security picture.
-
Improve visibility and actionability to see how different threats and mitigations are connected across the system.
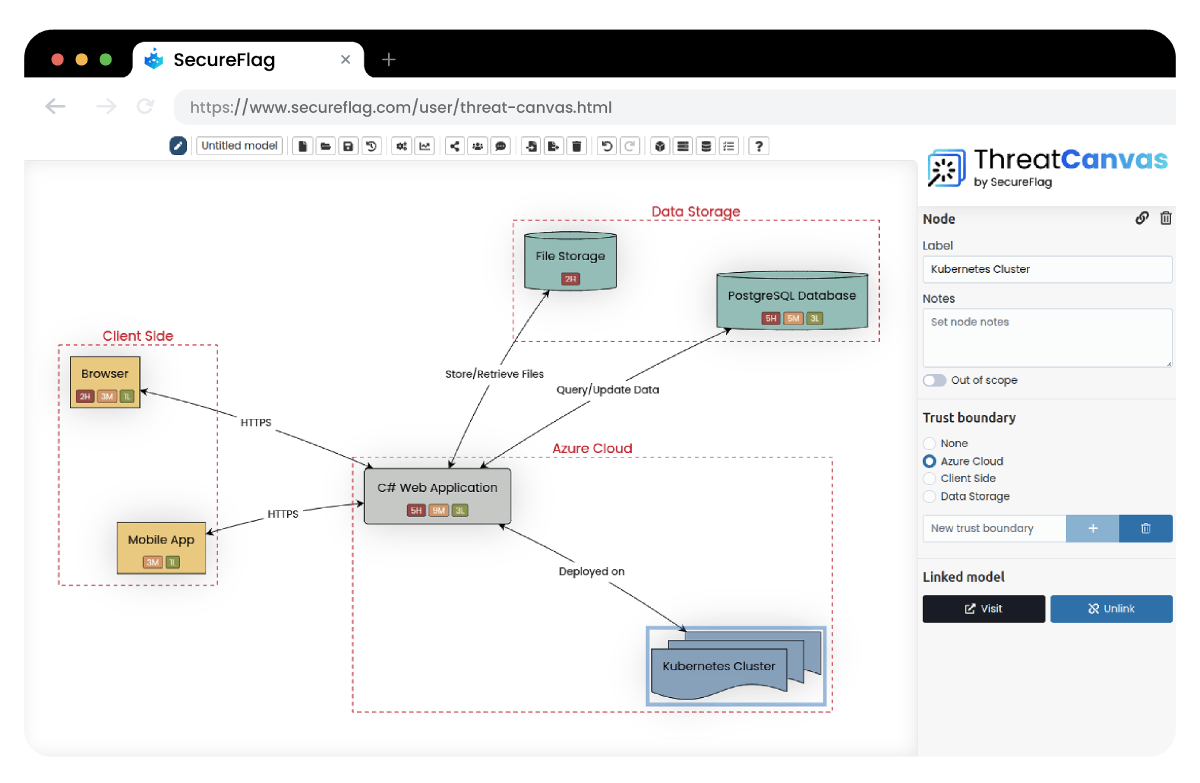
What is ThreatCanvas?
SecureFlag’s ThreatCanvas is an automated threat modeling solution that was created to streamline the process. Teams can easily create and manage threat models at both the system and component levels, and get insights into security threats throughout the development lifecycle.
With built-in Risk Templates for industry standards like GDPR, HIPAA, and FedRAMP, ThreatCanvas helps teams quickly align with compliance requirements. Not only is it scalable, but it simplifies risk assessment and management. Most importantly, it makes sure that security is built into the development process from the very beginning.
Expanding New Use Cases
Most organizations need a way to improve security that doesn’t slow down development. Linked Threat Models in ThreatCanvas can help you do that. Here’s how:
-
Integrated security reviews: Add security checks directly into development workflows, making it simpler to stay on top of risks as software evolves.
-
Scalable for large teams: Large organizations with multiple development teams can standardize threat modeling while letting teams focus on their own parts of the system.
-
Improved compliance alignment: Organizations can link high-level compliance models with detailed, actionable security models to meet regulatory requirements like FedRAMP, HIPAA, PCI DSS, and GDPR.
Get Started with Linked Threat Models in ThreatCanvas
ThreatCanvas is changing the way security teams and developers work together on threat modeling. It’s time to move away from difficult and resource-draining threat modeling processes by using Linked Threat Models. If you’re looking for a more scalable and practical way to assess security risks, this is it!
Want to see Linked Threat Models in action? Book a demo today!