Believe it or not, threat modeling doesn’t have to be overwhelming. Sure, thinking about security risks can seem complex, but with the right approach and tools, organizations can catch potential issues early, before they become costly problems.
How can teams make sure their threat modeling process is worthwhile? First, let’s see what threat modeling is all about, and then get into some of the ways you can simplify the threat modeling process.

What is Threat Modeling?
If you’re already familiar with the basics, then you should know that the aim of threat modeling is to find, analyze, and mitigate potential threats before they become major issues.
It’s a way to help you find your organization’s security strengths and weaknesses, especially threats, and figure out how to stay safe. It helps teams prioritize their security efforts, work out how to use their resources properly, and make better choices on where to invest in protection.
To follow the threat modeling process properly, you first need a good understanding of your system’s assets, such as data and infrastructure, as well as security requirements. And of course, you’ve got to be on the lookout for potential threats, whether they’re from insiders or external attackers. By taking into account all these factors, organizations can catch vulnerabilities and find strategies to minimize risks.
At the core of threat modeling best practices threat modeling is team effort, bringing together security teams, developers, and business stakeholders. Also, remember that the threat modeling process isn’t done once-off. Rather, it’s an ongoing process where, as new threats emerge, models need to be updated.
When to Start the Threat Modeling Process?
Sometimes, it can be confusing to know when teams should start the threat modeling process. Well, the simple answer is to start as early as possible, preferably during the planning and design stages of the software development lifecycle (SDLC). Getting ahead on the threat modeling process helps catch security risks before they turn into bigger issues, making it easier to build security into the design from the beginning.
There could be changes in an application, like adding new features, adjusting existing ones, or dealing with a security incident. In this case, a review of the threat model should be required again. Regularly checking your threat models keeps security assessments updated and aligned with new threats.
Which Threat Modeling Methodology to Use?
Organizations use a few different threat modeling methodologies to identify and take on potential security threats. Each one has its own approach and works best depending on the specific needs and resources. Here are two of the most popular ones:
-
STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege): Developed by Microsoft, STRIDE is widely used because it offers a thorough way to spot and categorize threats.
-
PASTA (Process for Attack Simulation and Threat Analysis): PASTA takes a hands-on approach by simulating attacks and analyzing threats in a structured way. If organizations want to better understand how different attack scenarios play out, this is a good method to use.
-
Rapid Developer-Driven Threat Methodology (RaD-TM): For organizations that want a scalable, lightweight, developer-focused approach to threat modeling, SecureFlag’s Rapid Developer-Driven Threat Methodology (RaD-TM) is the answer. It provides an easy way for developers to integrate the threat modeling process into their daily workflows. A big plus is that it reduces the need to rely on security experts.
Automation Tools
As some of you may know, when the threat modeling process is done manually, it can be really time-consuming. So why use traditional methods when there are automation tools?
SecureFlag’s ThreatCanvas is an automated threat modeling solution that makes the threat modeling process easier. Teams can quickly create and manage threat models at both the system and component levels, getting clear insights into security risks throughout development.
Built-in risk templates for GDPR, HIPAA, and FedRAMP (and many more!) also help teams stay on top of compliance. It simplifies risk management, is scalable, and, importantly, embeds security into the development process from the beginning.
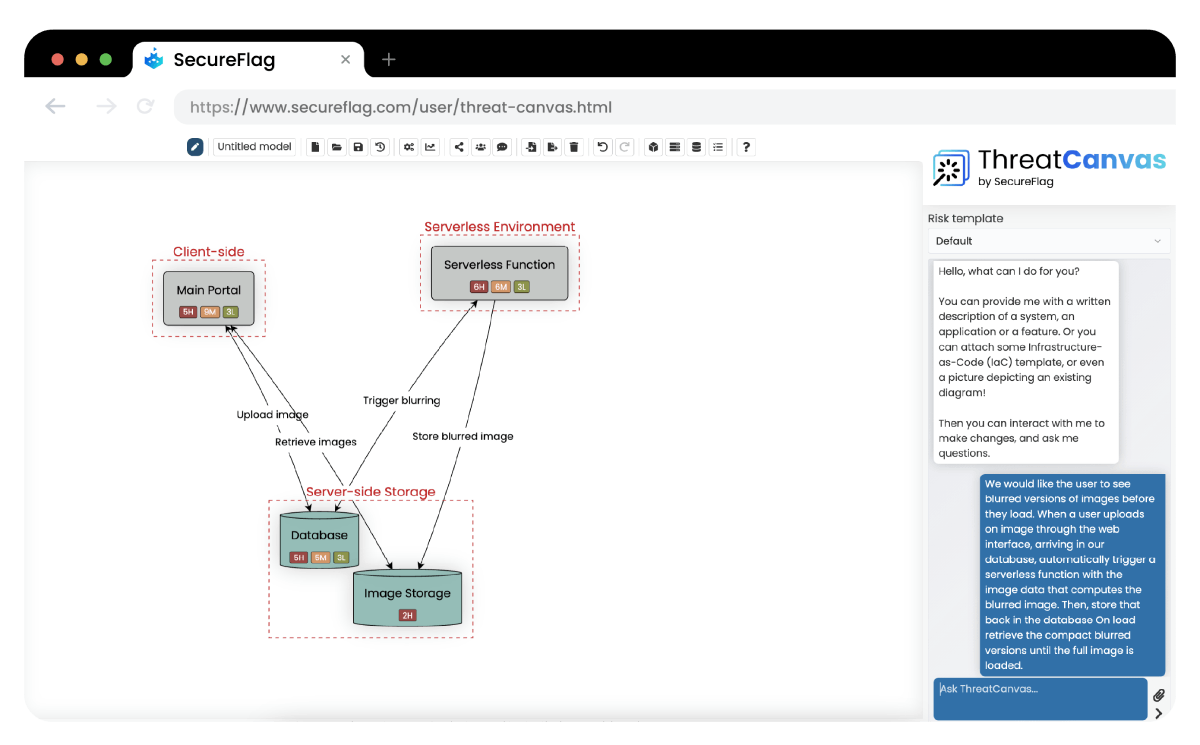
DevSecOp Workflows
As mentioned, security should be factored in early, during the planning and design phases. If the threat modeling process is embedded into DevSecOps pipelines, teams can assess risks as they build and deploy software. Getting developers to use threat modeling patterns in user stories and backlog items helps make security a natural part of the development flow.
The responsibility of security should be shared across development, security, and operations teams. There shouldn’t be only one team taking the burden. It’s much easier to spread security awareness across the organization that way.
Continuous Threat Modeling
The threat modeling process isn’t something you only do once and then forget about (it may have been like that in the past, but not anymore!) Rather, it has to be a continuous process, as the system evolves and new threats and vulnerabilities emerge all the time. Just as your organization’s secure posture doesn’t remain static, threat models need to be updated to reflect this.
Continuous threat modeling involves monitoring for new threats and vulnerabilities, updating threat models to reflect changes, and refining them to improve their accuracy. Also, by continuously testing your threat models, you’ll be making sure they’re working as they should.
Document and Reuse Threat Models
Creating new threat models every time isn’t always needed. As the saying goes, why reinvent the wheel? To make the process faster, teams can keep a repository of all the threat models done in the past and then reuse them to save time. It also gives more consistency and gives you time to refine your approach.
Another advantage to keeping a threat model repository is that new team members can get a good understanding of your company’s security concerns and learn how they are usually dealt with.
Also, you should consider versioning your threat models to keep track of changes over time. If updates are properly documented, then teams can look back at earlier assessments if needed.
Prioritize Threats Based on Risk
It stands to reason that some risks are more urgent than others and need more attention. Others might not be too much of a huge issue that needs to be dealt with straight away. How do you work out what’s more important? Using a risk-based approach helps teams prioritize the most serious security issues first. It takes into account factors such as likelihood, impact, and exploitability. Working out which threats to prioritize and putting countermeasures in place is key to managing risk.
You can also use threat intelligence feeds to stay ahead of emerging threats relevant to your industry. By aligning your threat modeling with real-world risks, you’ll better prioritize which issues to address first.
Keep It Practical and Collaborative
We know that the threat modeling process can often feel complicated and overwhelming, which are precisely the reasons that many teams would prefer not to do it. The answer is to keep the threat modeling process as collaborative as possible. Get developers, architects, and security professionals talking together instead of making it just a security-focused task. The goal is to build a security-aware culture where everyone knows how their choices affect risk. Understanding the different types of threat agents and what drives them helps prioritize and protect critical assets.
Collaboration across teams makes sure threat models take both technical and business needs into account. For example, developers can share specific insights about the application they’re working on, while security teams can give advice on attack paths and ways to reduce risk. (Although, if you use the RaD-TM model, developers don’t have to rely on security teams!)
Attack Simulation and Threat Analysis
Another good way to find out where security gaps are and plan what defense strategies to use is through simulation and threat analysis.
Attack simulation tests how real-world threats could exploit vulnerabilities in an organization’s systems. This is where teams can use penetration testing, which simulates attacks to find vulnerabilities. Another technique, red teaming, mimics real attackers to see how strong the organization’s defenses are.
Organizations can use threat analysis and attack simulations to find potential threats and improve security strategies. Another thing is that teams can also analyze threat intelligence to understand who might be targeting the organization and how.
Avoiding Common Pitfalls in the Threat Modeling Process
The threat modeling process isn’t always straightforward, and there are a few things to look out for that can make it less effective. Here’s what they are:
-
Leaving people out of the process: Threat modeling works best when security teams, developers, and business stakeholders collaborate to provide a more complete and accurate threat model.
-
Overlooking potential threats: It’s easy to focus on external attackers, but internal threats and different attack motivations should also be considered to avoid blind spots.
-
Not prioritizing risks: Focusing on threats that are most likely to occur and have a higher impact ensures efforts are spent where they matter most.
-
Treating it as a one-time task: Threat models should keep up-to-date with new risks and business changes to keep them relevant and useful.
Measure and Improve the Threat Modeling Process Over Time
As threat modeling is an ongoing process, it’s something that should improve over time. How can you tell if what you’re doing is working? Teams can track progress by setting key performance indicators (KPIs), like the number of threats identified, time spent on remediation, and how well they’ve done at resolving issues.
Regular reviews can also show what’s working and what needs adjustment. By always refining the threat modeling process, it becomes more well-run each time.
Streamline the Threat Modeling Process With ThreatCanvas
We get it, traditional threat modeling can be daunting and complex sometimes, which is exactly why we created ThreatCanvas, to simplify things. It makes the threat modeling process easier and smoothly integrates with existing workflows. Identifying threats and figuring out how to mitigate them also becomes much easier when using methodologies like RaD-TM.
ThreatCanvas also improves collaboration between different teams in organizations, which is pretty important when it comes to threat modeling. It has features like Linked Threat Models and is designed for scalability, so organizations can ensure that security always remains a central part of their development process as they grow.


