For most organisations, managing their rapidly-expanding IT infrastructure can be a challenging endeavour. As more components and applications are added to the infrastructure, even experienced IT teams struggle to keep pace with its increasing scale and scope using manual processes.

To counter this increasingly complex reality of managing rapidly expanding environments, Infrastructure as Code, or IaC, has emerged as a technology to eliminate these infrastructure configuration management challenges and eliminate manual effort.
With IaC, infrastructure specifications are added to configuration files. These files are then used to provision and manage infrastructure, so there’s no need to do these steps manually every time an application is deployed or upgraded.
In addition to simplifying infrastructure configurations, IaC also ensures that a consistent environment is provisioned every time and prevents undocumented configuration changes.
Over the years, many tools have emerged to help organisations set up and manage their IaC needs. One of the most popular is Terraform.
Terraform is a cloud-agnostic, IaC software tool that enables organisations to describe their entire infrastructure in the form of code and easily manage their IT stack through automation.
IaC is a great approach; however, as with traditional configuration and deployment, it can introduce security issues for organisations if developers don’t follow security best practices.
So, what can your organisation do to avoid common issues and adopt desirable practices with Terraform?
This article will explore how SecureFlag’s new cloud security training labs can help you make the most of Terraform and IaC while keeping security risks out of your enterprise.
TL;DR
- Terraform is the most popular Infrastructure as Code (IaC) tool.
- Cloud Engineers and DevOps teams can define their entire cloud infrastructure in code using Terraform’s configuration files and reusable modules.
- It still requires Cloud Engineers to (know how to) write secure configurations.
Why Terraform Stood Up for IaC?

Terraform can easily provision, manage, and orchestrate an entire IT ecosystem via IaC, regardless of whether it is a single-cloud or multi-cloud deployment.
A single Terraform configuration allows users to quickly build all the required infrastructure resources and easily manage them in parallel, even if different providers and multiple clouds are involved. Since the same syntax can be reused for all deployments, there’s no need to use multiple tools and technologies.
Terraform supports 100+ cloud providers, including the three largest - AWS, Azure, and GCP. Once you configure and authenticate your cloud provider, you can define any number of cloud resources in a configuration file to modify your infrastructure as needed.
Terraform also supports state management. It keeps track of all changes in an environment and maintains up-to-date information about what the current infrastructure should look like. These state files can help close gaps between the infrastructure’s current state (what is) and desired state (what should be).
In sum, when it comes to simplifying infrastructure management using IaC, Terraform is one of the most user-friendly tools available today. Plus, it is platform-agnostic and works with any cloud provider. It is also agentless, meaning there’s no need to install agent software on servers to use Terraform.
Why You Should Care about IaC Security
As we have already seen, IaC enables organisations to quickly set up and scale their infrastructure across multiple cloud environments and providers. It works by adding layers of configuration and abstraction to cloud resource provisioning.
But this is exactly why it also presents new security risks in cloud environments. One cause of these risks is that modules are built to optimise infrastructure functionality and performance, so security sometimes gets overlooked. The result: the organization could become vulnerable to a variety of security threats as the attack surface can be pretty large since you can do almost anything you can do on the cloud using IaC.
Due to a lack of attention to security, you may apply misconfigured Terraform modules or default configurations that are not optimised for security. You may also fail to enable logging, use unencrypted databases, create insecure queues, publicly exposed buckets, or deploy vulnerable microservices. Any of these security misconfigurations can increase the risk of cyberattacks and breaches against your organization’s infrastructure.
It’s also very common to forget about these misconfigured modules and other mistakes, which means they may remain misconfigured and insecure long after initial implementation, creating further security problems in the future (especially if modules are reused). For example, development configurations may be left over and make their way into the production cloud environment, increasing the risk of a serious security incident.
If an attack or breach does happen, it can disrupt normal operations, which can ultimately impair the availability of your services. Downtime and service availability may result in financial and reputational damage to your firm.
A cyberattack can also create compliance headaches, especially if it results in the loss of customer data or other kinds of business-critical data. Today, any organisation that deals with sensitive data, such as Personally Identifiable Information (PII), financial data, or intellectual property, is required to comply with many privacy regulations. And to do this, it’s vital to implement robust security controls to protect the infrastructure, no matter how you build it - manually or through IaC tools like Terraform.
Introducing New Cloud Labs @ SecureFlag
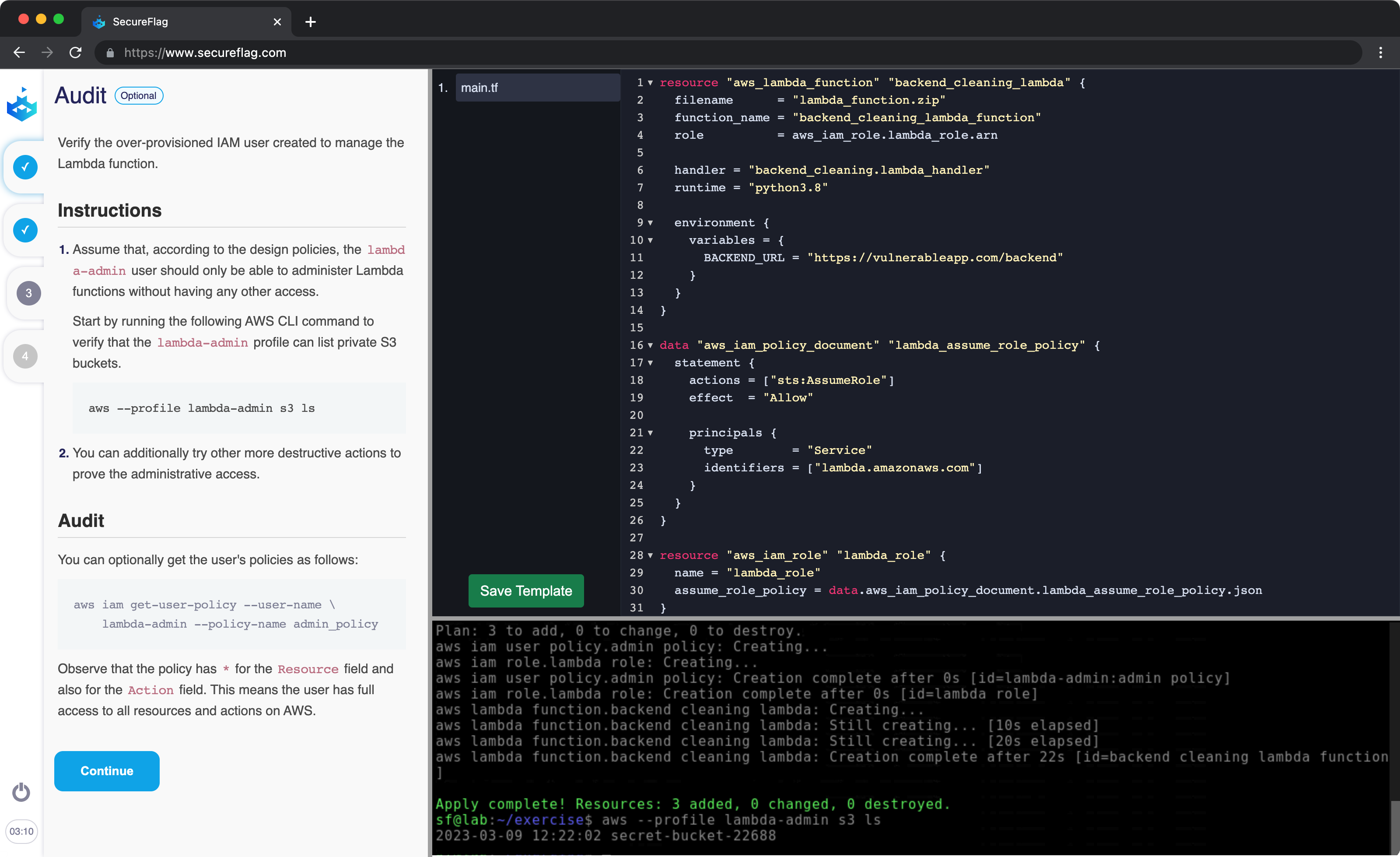
Most security vulnerabilities in cloud infrastructure come from insecure design, such as the use of insecure configuration and non-adherence to security best practices. To prevent such design-related security mistakes, it’s essential for DevOps, Cloud, and Security teams to understand and implement best practices and create secure Terraform templates.
The best way to learn and internalise these best practices is through hands-on learning. At SecureFlag, we teach DevOps and Cloud Engineers how to build secure infrastructures using real cloud environments.
Our brand new Cloud labs provide learners with a full AWS account, which means your developers get a real cloud environment in which they can identify and fix real-world problems and understand how to build secure infrastructures from the very first keystroke.
The labs include a built-in Terraform editor, full terminal access, and step-by-step instructions. These labs will enable you to find security defects in the IaC template. More importantly, you will learn how to remediate these defects in order to create secure and compliant AWS infrastructure using Terraform.
TL;DR
SecureFlag’s new cloud labs will empower DevOps, Cloud, and Security engineers to:
- Understand common security exposures that affect Cloud infrastructure.
- Learn how to fix security defects in Terraform templates before they can reach production code.
- Maintain compliance with all applicable security and privacy regulations.
Terraform is a useful and powerful tool that allows you to make the most of IaC for your cloud environments. You can use Terraform to define your entire cloud infrastructure as code, so all your resources can be effortlessly managed and versioned like application code. This ability will create numerous advantages for your company and team, including repeatability, consistency, and the ability to roll back changes if something goes wrong.
However, with great power comes great responsibility. If Terraform templates are not produced with security in mind, it can result in leaving your cloud resources vulnerable to security exposures. The best way to reduce your attack surface is to develop infrastructure following security best practices and learn how to use IaC securely. And the best way to do this is with hands-on cloud training labs that allow you to identify and fix misconfigurations in a safe environment.
Take advantage of SecureFlag’s labs to gain hands-on experience with Terraform and learn proven best practices to use it safely. For more information about these labs and how they can help your team achieve true IaC success with Terraform, contact us.