Are you responsible for safeguarding sensitive healthcare data? If so, ensuring compliance with Health Insurance Portability and Accountability Act (HIPAA) should be high on your list of priorities. By conducting a thorough threat modeling exercise, you can identify potential risks and vulnerabilities in your healthcare system’s architecture, helping you implement effective security controls before it’s too late.

Understanding HIPAA and the need for threat modeling
Before we take a look at the details of threat modeling for HIPAA compliance, let’s first understand what HIPAA is and why it is important in the healthcare industry. HIPAA was enacted in 1996 to protect the privacy and security of individuals’ health information. It sets standards for the electronic exchange, privacy, and security of health information.
According to the HIPAA Journal, in 2023, 725 data breaches were reported and across those breaches, more than 133 million records were exposed or impermissibly disclosed, highlighting the importance of implementing secure practices when handling sensitive data of this nature.
Violations of HIPAA regulations can result in severe penalties and damage to an organization’s reputation. Threat modeling plays a crucial role in ensuring HIPAA compliance by identifying potential risks and vulnerabilities before implementing systems that could compromise the security of sensitive healthcare data.
What is threat modeling?
At SecureFlag, we talk a lot about Threat Modeling, with our other blog posts looking at how to use it for Privacy, and how to use it for contexts such as PCI DSS. To sum it up, Threat modeling is a proactive approach to security that involves analyzing an organization’s infrastructure, applications, and data flows to identify potential threats and the likelihood of them being exploited. By understanding the potential risks and vulnerabilities, organizations can prioritize security measures and allocate resources accordingly.
In the context of HIPAA compliance, threat modeling helps healthcare organizations identify potential threats to the confidentiality, integrity, and availability of patient data. It allows them to assess the impact of these threats and implement appropriate security controls to mitigate the risks.
Benefits of threat modeling for HIPAA compliance
Threat modeling offers several benefits for HIPAA compliance. Firstly, it provides a structured approach to identify and prioritize potential risks and vulnerabilities. This helps organizations allocate resources efficiently and implement security controls that address the most critical threats.
Secondly, threat modeling helps organizations gain a deep understanding of their system’s architecture and how it interacts with sensitive healthcare data. This understanding is crucial for identifying potential attack vectors and designing effective security measures.
Lastly, threat modeling promotes a proactive security mindset. By continuously assessing their systems for potential threats, organizations can stay one step ahead of attackers and ensure the ongoing protection of sensitive healthcare data.
The threat modeling process for HIPAA
To effectively conduct threat modeling for HIPAA compliance, it is important to follow a systematic process. The following steps outline the key components of a threat modeling exercise:
Identifying assets and data flows in the healthcare industry
The first step in threat modeling for HIPAA compliance is to identify the assets and data flows within the healthcare organization. This includes understanding the types of sensitive healthcare data being processed, stored, and transmitted, as well as the systems and applications involved in handling this data.
By mapping out the data flows, organizations can gain a clear picture of how sensitive healthcare data moves through their systems and where potential vulnerabilities may exist.
Assessing threats and vulnerabilities in HIPAA compliance
Once the assets and data flows have been identified, the next step is to assess what kind of threats and vulnerabilities that could impact the confidentiality, integrity, and availability of sensitive electronic protected health information (ePHI).
The Security Rule outlines the need to ensure that mechanisms are in place for threats resulting from poorly implemented encryption techniques; this might arise from using outdated encryption methods or insufficient access control. Also mentioned is the need to enforce access control and authentication to prevent unauthorized access to sensitive data, including ePHI, stored in healthcare databases.
While it’s important to secure data at rest, the Security Rule also notes the need for security in transmission with encryption, preventing any opportunities for data breaches due to network packet sniffing and other forms of Man-in-the-Middle attacks.
Mitigating risks and implementing security controls
After identifying the threats and vulnerabilities, organizations should consider the HIPAA Security Rule, which provides specific requirements for safeguarding ePHI, such as ensuring appropriate administrative, physical, and technical safeguards are in place to maintain the confidentiality, integrity, and security of electronic protected health information. The Rule does not mention the use of specific technologies but requires a reasonable and appropriate implementation of security measures.
Keeping this in mind, the next step is to mitigate the risks by implementing appropriate security controls. HIPAA § 164.312 lists details about what functions the safeguards should perform, with examples such as access controls to only grant users the minimum level of authorization for the resources needed in their roles and mechanisms such as automatic logoff systems to prevent idle workstations being a target of malicious opportunists. Another HIPAA Security Rule requirement is the use of transmission encryption to safeguard ePHI privacy and integrity.
Auditing capabilities should also be implemented to allow for recording and examining activity in information systems that contain or use ePHI. Such systems allow for monitoring for potential breaches or if any violations have occurred.
Best practices for conducting threat modeling for HIPAA
To conduct a successful threat modeling exercise for HIPAA compliance, it is important to follow the best practices:
- Involve stakeholders from different departments, including IT, security, compliance, and legal, to ensure a comprehensive approach.
- Regularly update your threat model to incorporate new threats and vulnerabilities as technology and threats evolve.
- Conduct regular risk assessments to identify emerging risks and prioritize security measures accordingly.
- Document your threat modeling process and findings to ensure consistency and enable future audits or reviews.
SecureFlag’s ThreatCanvas for HIPAA
With ThreatCanvas, the time and effort to create expert-level threat models is greatly reduced, thanks to the use of risk templates and Artificial Intelligence to generate models based on input system descriptions or with an Infrastructure as Code template.
Using ThreatCanvas you can create custom risk templates to use throughout your organization to ensure accuracy and consistency across teams or use one of the predefined risk templates to model threats in the context of health insurance compliance with HIPAA, focusing on Privacy Threat modeling through LINDDUN, or performing security threat modeling using OWASP Top 10, PCI-DSS, or Microsoft’s STRIDE.
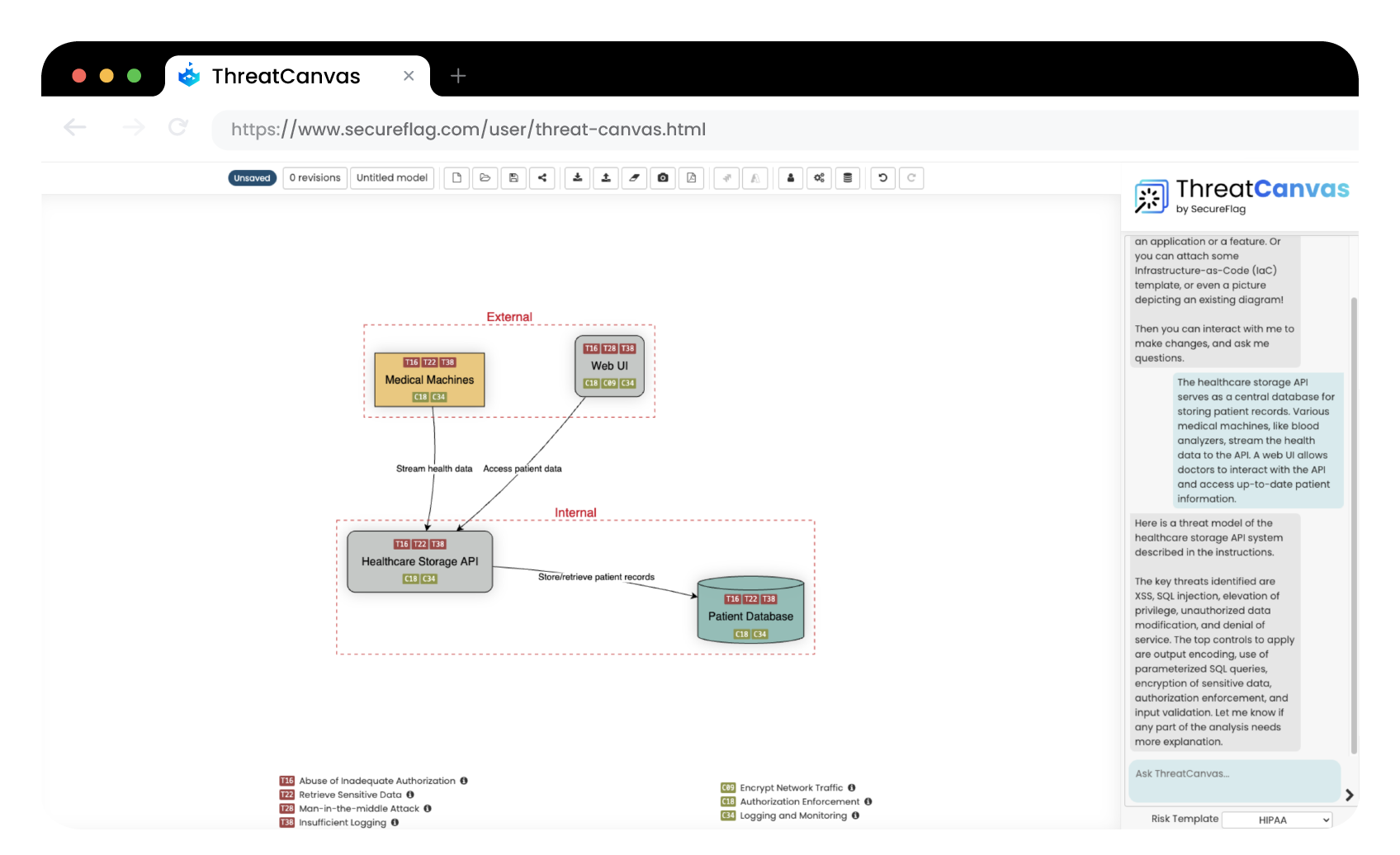
We recently introduced the new capabilities of ThreatCanvas Assistant so every one of your teams can have access to a security expert for questions on compliance, vulnerabilities, or with assistance in guiding them through the steps of threat modeling.
For more information about SecureFlag’s AI powered threat modeling tool ThreatCanvas, contact us today.