The Haskell programming language is considered very difficult to learn and master, with features such as strict immutability, higher-order functions, and lazy evaluation.
It’s a highly complex functional programming language, more so than other programming languages, so there is a higher risk of introducing insecure code if not everyone is fully familiar with it.

This is where we at SecureFlag want to help. We have been busy working on some Haskell virtual labs with the OWASP top 10 in mind—helping your teams write secure applications.
What is the Haskell programming language used for?
Thanks to its strong type system and other functional programming foundations, Haskell is used in many different areas and domains. It is widely used in academia to teach functional programming concepts, especially in courses such as Computer Science. Haskell is also widely adopted within the financial industry due to its high reliability and ability to create precise mathematical functions.
Another area where Haskell is utilized is web development, where its type safety helps build safer web applications and defend against vulnerabilities such as SQL Injection and XSS attacks.
What are some features of Haskell?
Haskell has many unique features that stand out. Some of these help drive security by nature and reduce runtime errors.
Type Safety and Security
Haskell’s type system enforces strict type rules at compile time. Unlike dynamically typed languages, like JavaScript, Python, and Ruby, Haskell requires variables and functions to be assigned specific types, ensuring that operations between incompatible types are caught as errors before the code is executed.
For example, the compiler will detect and flag type mismatches, preventing the potential for vulnerabilities such as memory corruption or unintended data transformations that could lead to security breaches. Haskell’s type system also encourages developers to write more explicit and self-documenting code, reducing the likelihood of errors and vulnerabilities caused by ambiguity or unclear code.
Immutability
Immutability is one of Haskell’s foundational features. In essence, immutability means that once a value is assigned to a variable, it cannot be changed. This principle prevents a wide range of issues in programming, such as race conditions, unexpected values, and inadvertent modifications. Since data cannot be altered after its creation, immutable structures inherently protect against many forms of data corruption and side effects.
For example, in concurrent programming, multiple threads can safely read shared data without the risk of one thread modifying it in a way that causes errors in another thread. This eliminates the need for complex locking mechanisms, which can be error-prone and introduce their own vulnerabilities.
Immutability also enhances security by making the code more predictable and easier to reason about. When data is immutable, you can trust that it will not change unexpectedly, which simplifies debugging and auditing—a function will always have the same result given the same inputs, unlike a Java method that could depend on the state of an object that might be unknowingly modified.
This reliability is crucial in security-sensitive applications, where data integrity and consistency are paramount. Moreover, immutable data structures are often more straightforward to test because they eliminate the complexity associated with state changes, making it easier to verify that code behaves correctly under all conditions. By enforcing immutability, Haskell helps developers create robust, secure applications that are less susceptible to common programming errors and security vulnerabilities.
Lazy Evaluation
Lazy evaluation, another core feature of Haskell, means that the compiler only evaluates expressions when their results are needed. This approach offers significant benefits for CPU and memory utilization, as it avoids unnecessary computations and reduces resource consumption. From a security perspective, lazy evaluation can mitigate certain types of vulnerabilities by limiting the execution of code. Since only the required computations are performed, the attack surface is reduced, making it more difficult for malicious code to execute undetected.
Lazy evaluation also helps prevent data corruption and unintended side effects by controlling when and how computations are performed. In Haskell, expressions are not evaluated until their results are required, which minimizes the risk of modifying data prematurely or unnecessarily. This deferred computation model ensures that data remains in a stable state until it is absolutely needed, reducing the chances of accidental corruption.
For example, in scenarios where multiple operations are performed on a dataset, lazy evaluation ensures that only the necessary computations are carried out, preserving the integrity of the data until the final result is needed.
SecureFlag’s new virtual Haskell training labs
Our Haskell virtual labs are designed to provide immersive, hands-on learning experiences. Each lab includes realistic scenarios and exercises that mimic real-world security challenges. After working through these labs, you’ll gain an understanding of how to attack your Haskell applications and learn how to implement secure Haskell code to apply it in your own projects. Scenarios and vulnerabilities include OWASP’s top 10 to represent a variety of the most critical security risks to web applications.
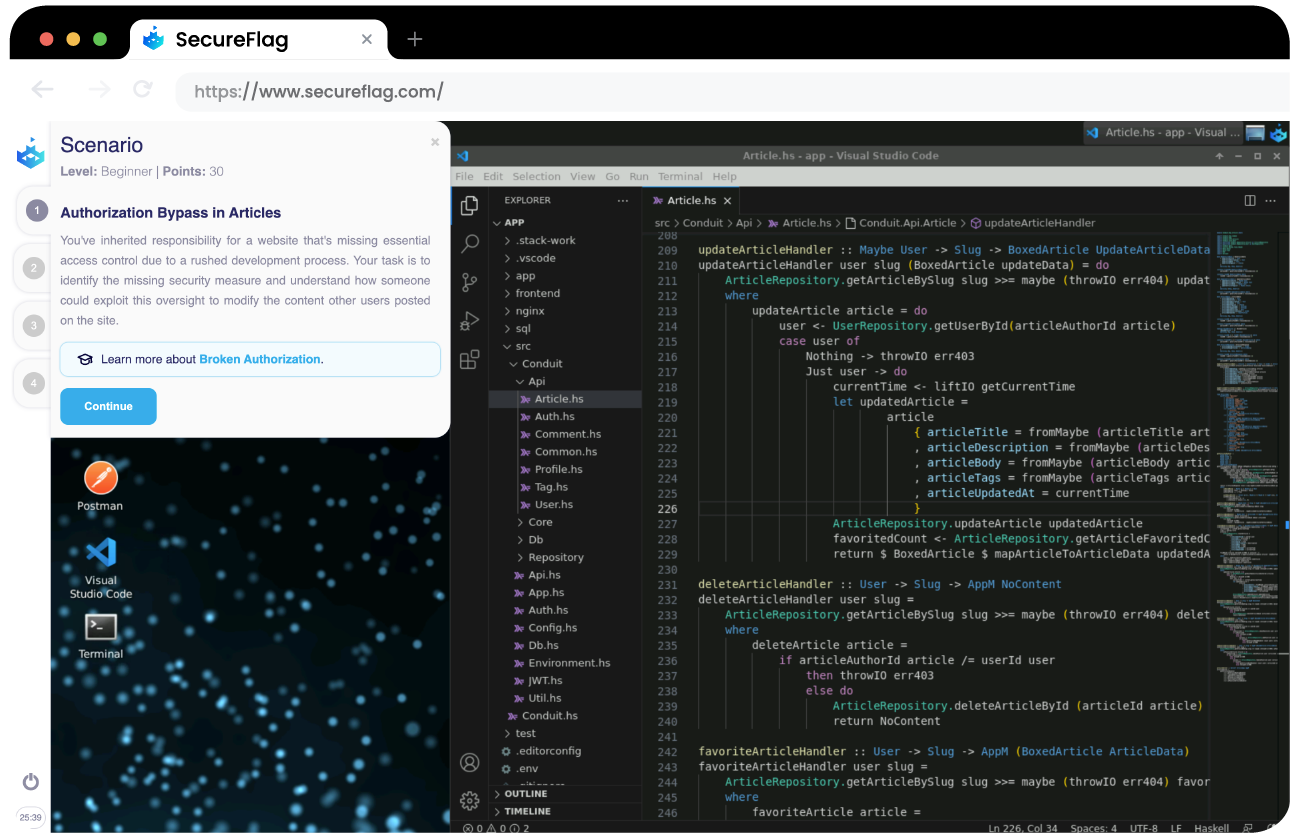
If you or other team members are a Haskell programmer, then SecureFlag’s platform provides instant feedback and guidance, helping you learn from mistakes and reinforce best practices.
Contact our team today to learn more about our labs and our AI-Powered threat modeling tool, ThreatCanvas. SecureFlag also has a joint initiative with OWASP where OWASP members can get access to Secure Code Training and ThreatCanvas. Read here to find out more!


