How secure is your organization’s Active Directory? One of its most essential features, Kerberos delegation, can expose systems to attacks, and even a single misconfiguration can put an entire network at risk.
To help SOC analysts address this challenge, SecureFlag has launched a new learning path on Kerberos delegation. It helps teams understand how delegation works and, through hands-on labs, how to secure it effectively.

What is Kerberos Delegation?
Kerberos is the primary authentication protocol used by Active Directory, ensuring that users and services can verify their identities without having to enter passwords repeatedly.
Delegation is a Kerberos feature that allows a service to perform actions on behalf of a user when accessing another service. For example, if a user logs in to a web application that requires information from a database, delegation allows the application to access the database in their name without asking them to log in again.
The Risks of Delegation
Unfortunately, delegation comes with its own set of risks. If attackers compromise a service account with delegation permissions or gain access to a server where delegation is enabled, they can impersonate users, escalate privileges, or move laterally across systems. What’s meant to help users can quickly become an entry point for attackers.
Why Attackers Target Kerberos Delegation
Kerberos delegation attacks are appealing to malicious actors because they exploit legitimate Windows features rather than software vulnerabilities. This gives attackers several advantages:
-
Hard to detect with traditional security tools.
-
Difficult to distinguish from regular network activity.
-
Effective for lateral movement after initial compromise.
Overcoming Delegation Challenges
Experienced SOC analysts can still face challenges when monitoring delegation activity, such as:
-
Unconstrained delegation: These configurations grant services wide-reaching access, so analysts should closely monitor them.
-
Constrained delegation: Even though access is more limited, misconfigurations or combinations with other vulnerabilities can still be exploited.
-
Resource-based delegation (RBCD): Attackers with write permissions on computer objects can abuse RBCD to gain unauthorized access, a risk that’s often overlooked.
-
Focusing only on alerts: Without an understanding of delegation, analysts may treat individual alerts in isolation rather than recognizing patterns of abuse.
Inside the New Learning Path
The learning path guides users through Kerberos delegation and abuse step by step, and includes:
-
Understanding the basics: Learn what delegation is and how it works in Active Directory.
-
Exploring attack techniques: See how attackers can exploit misconfigurations, including unconstrained, constrained, and RBCD.
-
Hands-on practice: Work through interactive labs to find vulnerabilities and apply defenses in realistic environments.
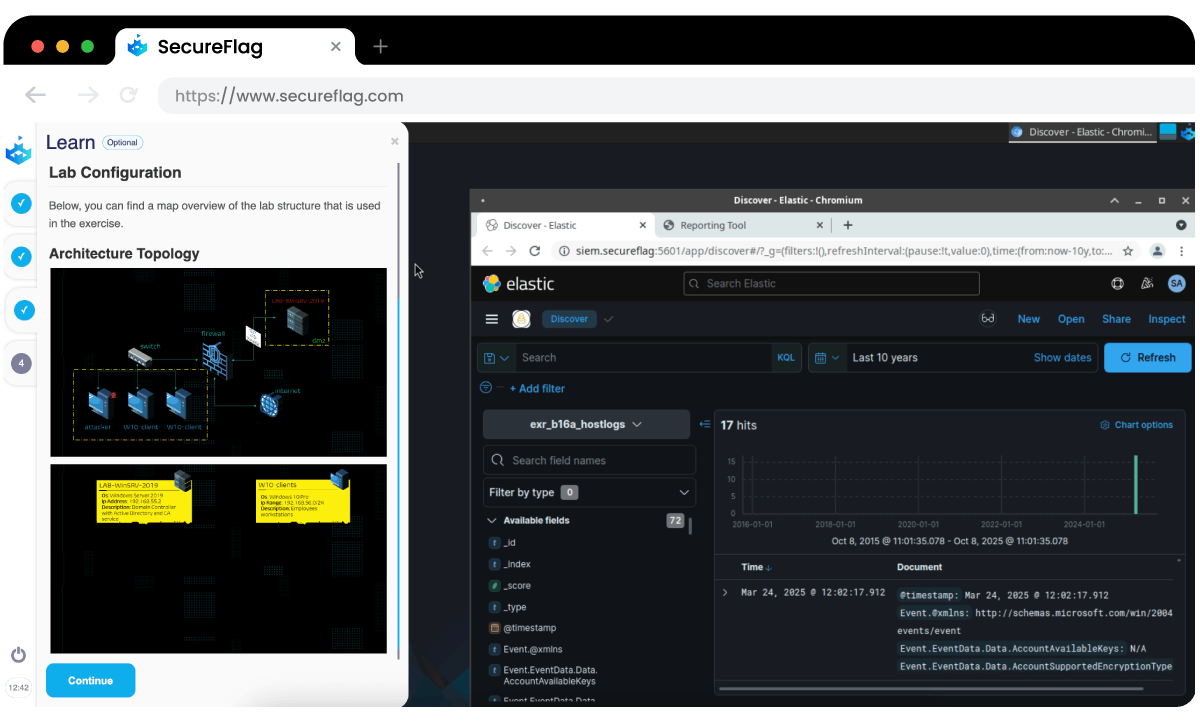
Gain Fundamental Skills
After the learning path is completed, SOC analysts will be better prepared to:
-
Identify insecure delegation configurations and potential abuse scenarios.
-
Investigate suspicious activity linked to delegation misuse.
-
Apply practical defenses to reduce delegation-related risks.
-
Respond to incidents involving delegation-based attacks.
Why SecureFlag Stands Out
SecureFlag helps analysts turn their theoretical learning into practical experience. Through interactive labs, learning paths, and real-life scenarios, they can practice detecting and responding to threats.
This learning path is part of SecureFlag’s ongoing mission to help organizations put security knowledge into action and strengthen defenses.