When working with software every day, it’s easy to see some processes in the software development life cycle (SDLC) as obstacles getting in the way of the new releases. Security is often seen as one of the final hurdles; one final scan before it’s ready. But what if this wasn’t the case? What if security was part of the whole sequence of development? At least, that’s part of the idea of DevSecOps.

What is DevSecOps?
If you are familiar with DevOps, you likely have a good idea of what DevSecOps might entail.
DevSecOps means Development, Security, and Operations; it’s a framework that integrates security into all phases of the software development life cycle (SDLC) with the aim of boosting overall application security.
The aim is to take it from an afterthought, to a practice embedded right from the start with a shared responsibility across all teams. DevSecOps involves a continuous, automated testing and workflow process to minimize security risks.
How DevSecOps Work
DevSecOps work by integrating security in a variety of ways. First, is the Shift Left approach which puts security at the beginning of the SDLC, even when the code is being written in initial stages. It encourages developers to continue to train and equip themselves with secure coding knowledge so that a proactive approach to security can be taken. DevSecOps automates a variety of security tasks such as vulnerability testing and code scanning, ensures there is a shared responsibility for creating and maintaining secure software and promotes collaboration between teams so that security risks can be identified earlier in the development process.
Benefits of DevSecOps
DevSecOps means embedded security from the start of your SDLC. This can benefit your organization by:
*Early identification and fixing of vulnerabilities to reduce security risks *Software can be released quicker with automated and integrated security practices *Improved resilience and compliance
The reason DevSecOps has been gaining traction throughout organizations is that it aims to reduce the risk of releasing vulnerable products by enhancing collaboration, implementing automation, and outlining clear processes from the beginning of the development process.
Learning more about DevSecOps is the first step in the right direction for your organization.
How did we get from DevOps to DevSecOps?
The change didn’t just happen suddenly. Organizations and management teams have been steadily becoming more aware that while DevOps has been great for improving efficiency and delivery speeds for new releases, security has been holding position at the end.
The need for change has come as a reaction to the trends in cybersecurity. Vulnerabilities are being announced daily, and the costs of failing to secure data are skyrocketing. Along with this is the need to prove to customers and stakeholders that security is being taken seriously at all levels in an effort to meet compliance and protect customer data.
DevSecOps emerged as a solution to maintain the speed associated with DevOps and integrate it with continuous security processes right through to delivery.
Is there a DevSecOps Engineer role?
Absolutely! Dedicated DevSecOps engineers are becoming more common throughout the software development industry. These roles are important for weaving security processes throughout the SDLC to ensure that they aren’t an afterthought but are also not intrusive to the normal development pipeline.
Key responsibilities of a DevSecOps Engineer
With the rise in DevSecOps, understanding the role and responsibilities of an engineer can help you better answer the question “what is DevSecOps?”
What might a DevSecOps engineer do? Here are some responsibilities they might look after:
- Pre-commit: Getting new code pushed to repos quickly is important, but ensuring they do not contain sensitive information takes priority. Using a process and framework of Pre-commit means teams can catch any secrets or credentials that have been accidentally hard-coded or left in the code before reaching the source code repository. Pairing this with a code Linter can mean picking up poorly formatted or poor-quality code before it finds its way into production.
- Implement security testing: DevSecOps engineers embed security processes into CI/CD pipelines to catch vulnerabilities early on. These might include implementing tools such as Static Application Security Testing (SAST), Software Compositional Analysis (SCA), and Dynamic Application Security Testing (DAST) to detect any vulnerabilities in code, dependencies, and in the application during runtime.
- Automate security tasks: As the role stems from DevOps, it’s no surprise the role also embodies streamlining as many tasks as possible, improving speed and efficiency by automating any security tasks. Many of the testing tools mentioned above can be integrated into CI/CD pipelines, speeding up the testing phase and failing a build process if certain standards are not achieved.
- Build a security-first culture: As the role name might suggest, DevSecOps engineers bridge gaps between development, operations, and security teams. They often encourage more security training and promote best practices, collaboration and helping everyone apply security best practices in their work.
- Threat modeling and risk assessment: DevSecOps is also about proactively searching for threats that might appear in the future and positioning teams in the best spot to remediate them quickly or avoid the issue altogether. Part of this is using threat modeling and performing regular risk assessments on features, products, and deployments.
- Monitoring and responding: Of course, being proactive and looking for future threats is good, but responding to them is part of the DevSecOps roles, ensuring that any identified threats are addressed quickly to reduce any impact.
DevSecOps and the shift-left philosophy
Shift-left is the idea of moving security processes further left on the development scale. Where left means closer to the developers at the time of writing code.
For DevSecOps, the aim is to bring the idea of shift-left to the absolute maximum.
We’ve discussed the idea of shift-left in the context of secure coding training before. With DevSecOps, the idea isn’t much different. Incorporating security training, security best practices and detecting vulnerabilities as early as possible are the ultimate goals of the role, after all.
This might look like:
- Early security: Implementing methods such as scanning, threat modeling, and secure coding training from the very beginning. Reducing the chances of insecure code reaching the final product.
- Automated security tests: Using automated security tools in the CI/CD pipeline to allow continuous assessment throughout the development process.
- Secure coding practices: Incorporating secure coding processes into developers’ daily activities. This can take the form of implementing relevant training into issue tracking software on tickets with identified vulnerabilities and security issues. Training helps speed up remediation by teaching developers best practices at the right time.
DevSecOps and secure coding training
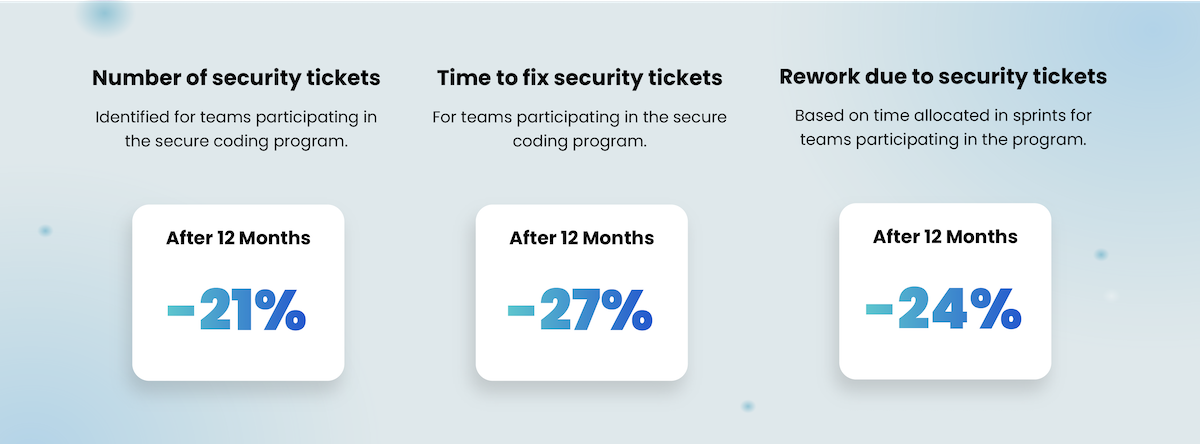
Secure coding training should be part of every security program.
At SecureFlag, we specialize in providing the most true-to-life training exercises available on the market. Our training uses virtual labs to immerse developers into familiar development environments, complete with IDEs, terminals, real applications, Postman, and other tools needed to write code.
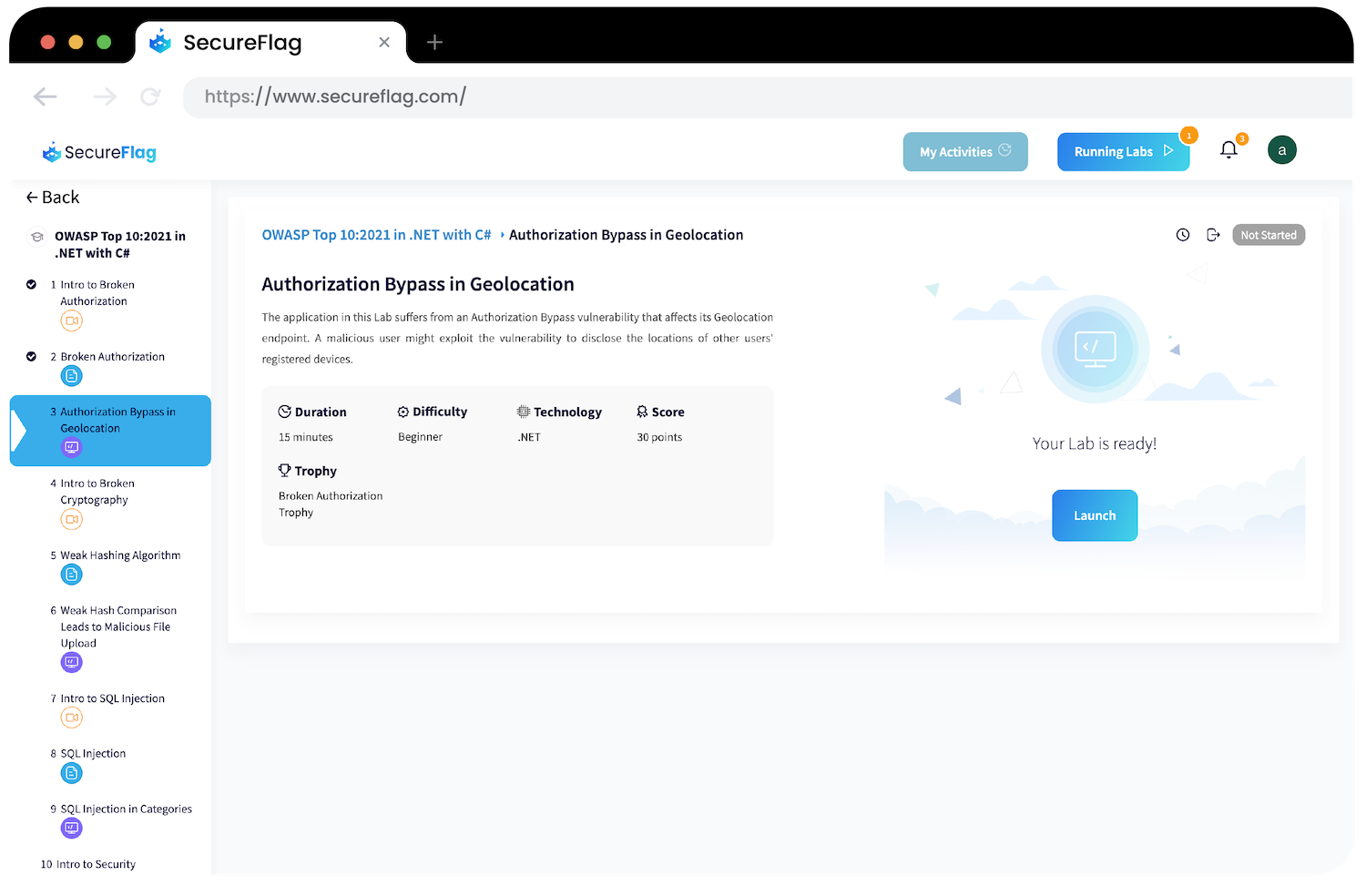
The SecureFlag Platform provides Learning Paths that cater specifically to different areas, roles, and languages; in fact, we will soon be releasing a Learning Path that specifically looks at the OWASP Top 10 CI/CD security risks. With our Learning Paths, developers and engineers can boost their skills in programming languages they know and develop new ones in the languages they are learning.
Each completed Learning Path earns a developer a certification to recognize their efforts and newfound skills.
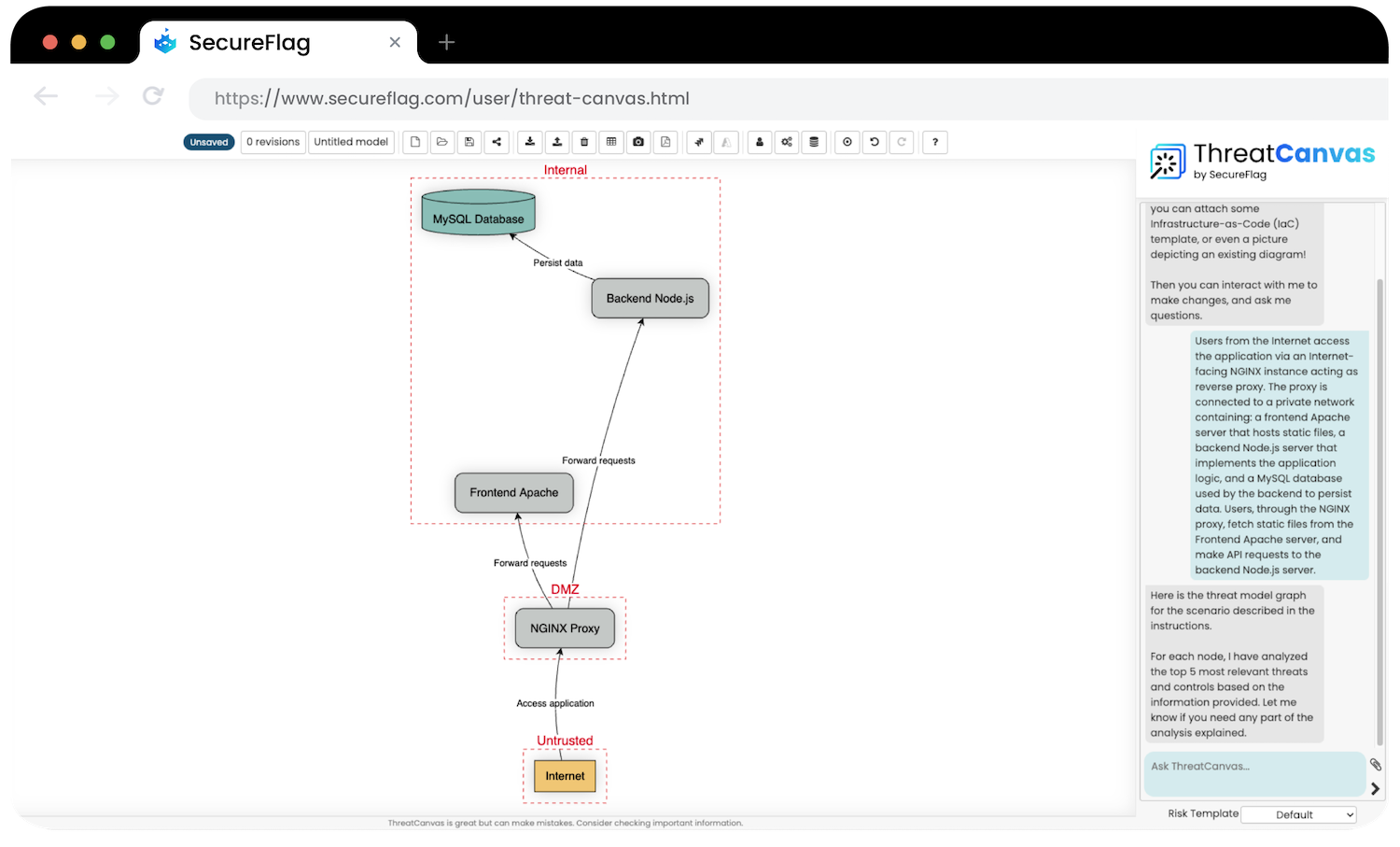
Threat modeling with ThreatCanvas
We’ve mentioned how part of DevSecOps will often use threat modeling throughout the SDLC. Threat modeling has historically been a difficult task to scale and a timely one to perform.
With ThreatCanvas, threat modeling becomes a straightforward and simple task that can be scaled across teams and collaborated on. Simply upload an existing diagram or enter a textual description of your features and applications, and ThreatCanvas will create and analyze a threat model specifically tailored to your needs.
Don’t wait for security issues to make their way into your applications. Boost your organization’s application security from the start by improving your developers’ secure coding training.


